2023HZNUCTF
Misc
致我那逝去的青春
炉石传说的代码解析,参考 https://zhangshuqiao.org/2018-12/炉石卡组代码解析/
直接贴php代码好了
1 |
|
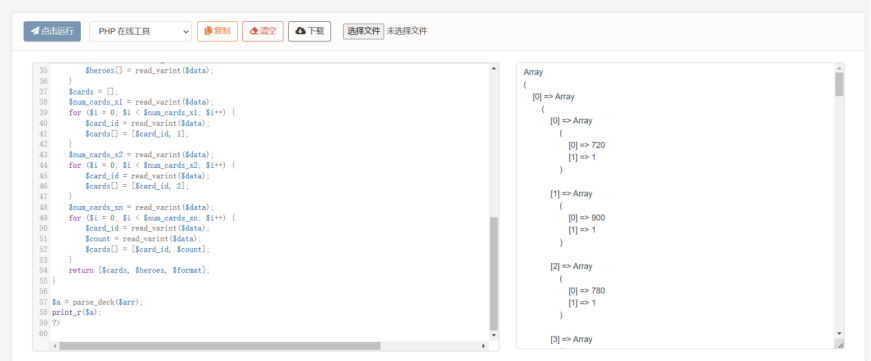
然后将其中的数组都除以十转ascii即可
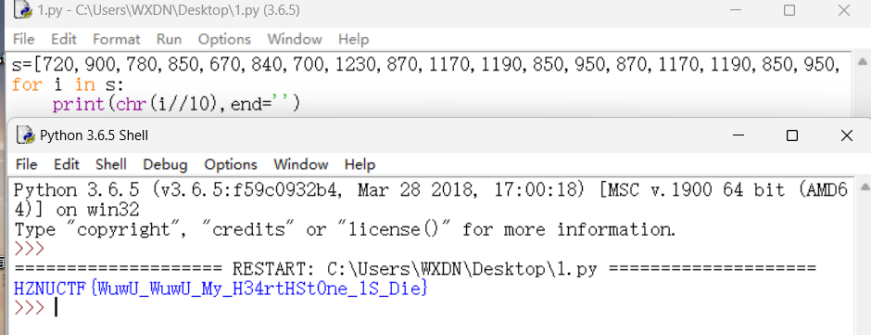
flag:HZNUCTF{WuwU_WuwU_My_H34rtHSt0ne_1S_Die}
还有python的一个库可以直接出
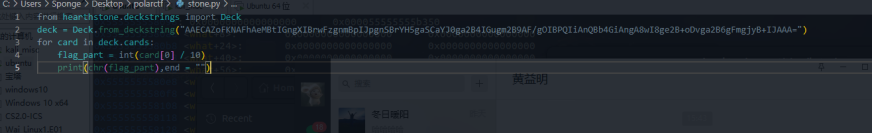
Snake
很经典,直接上pyinstxtractor
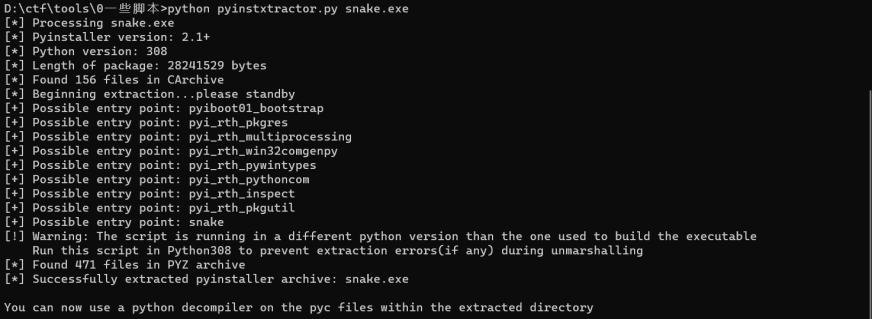
然后进去根据struct把snake.pyc的头补上
但是发现struct的头被去掉了
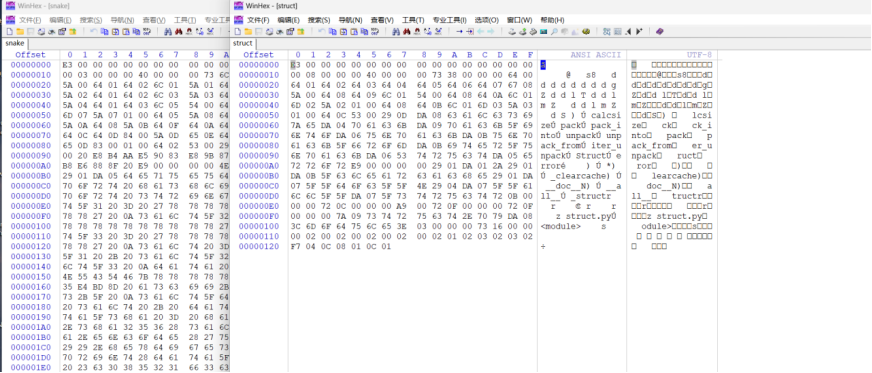
没关系,因为解压出来的还有base_library的文件,里面随便找个头补上就好了
然后在线反编译或者uncompyle6都行,我选择在线
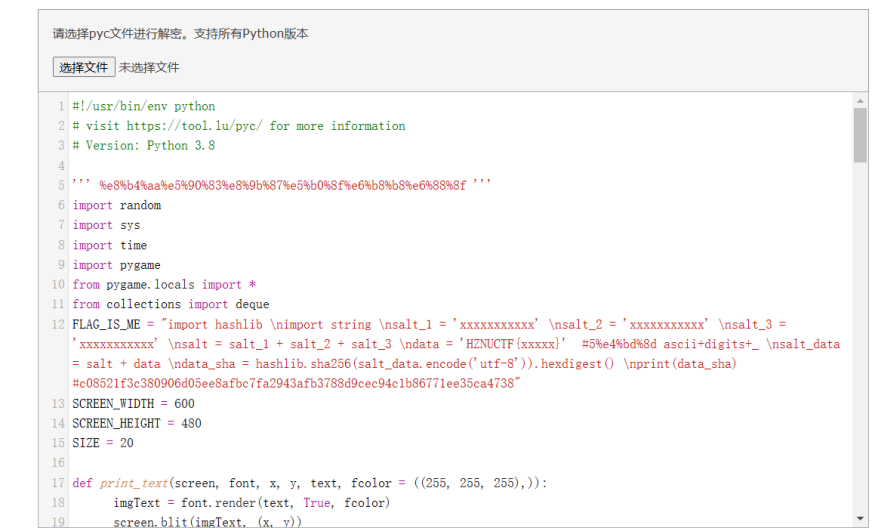
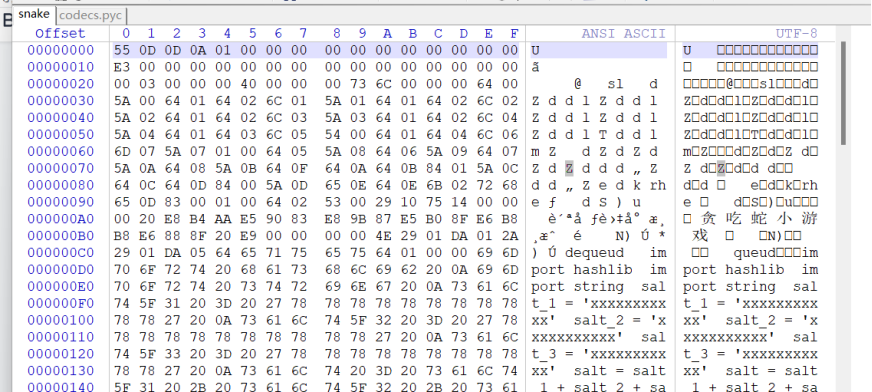
发现flag_is_me的关键字样,复制出来看看
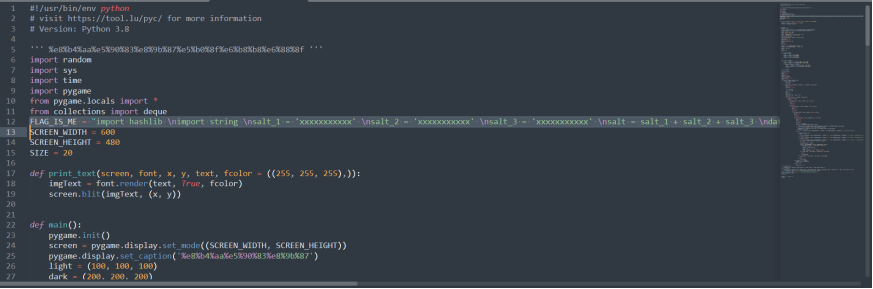
发现就是有三个盐值的sha256,中间#5%e4%bd%8d ascii+digits+_还提示了是五位的字母和数字还有下划线爆破
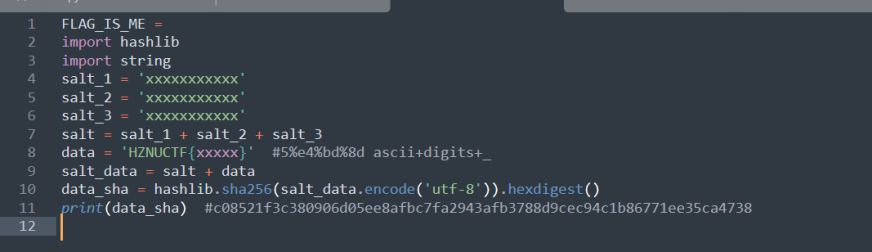
去源文件找盐值
第一个第二个很明显
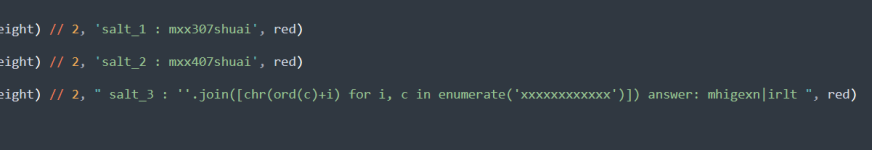
第三个就是每位减个下标就好
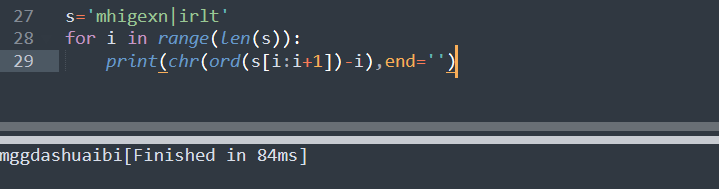
然后就是这样子
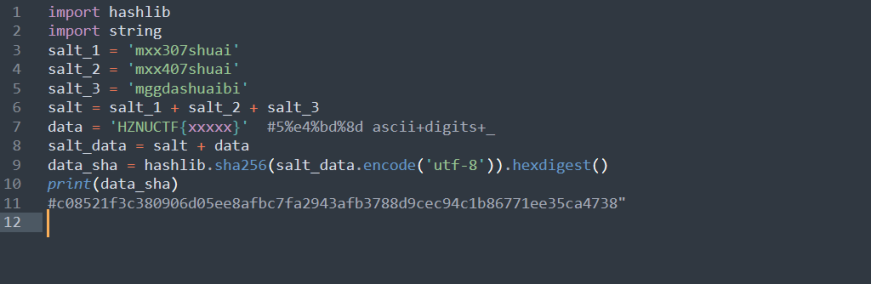
最后去爆破就好了
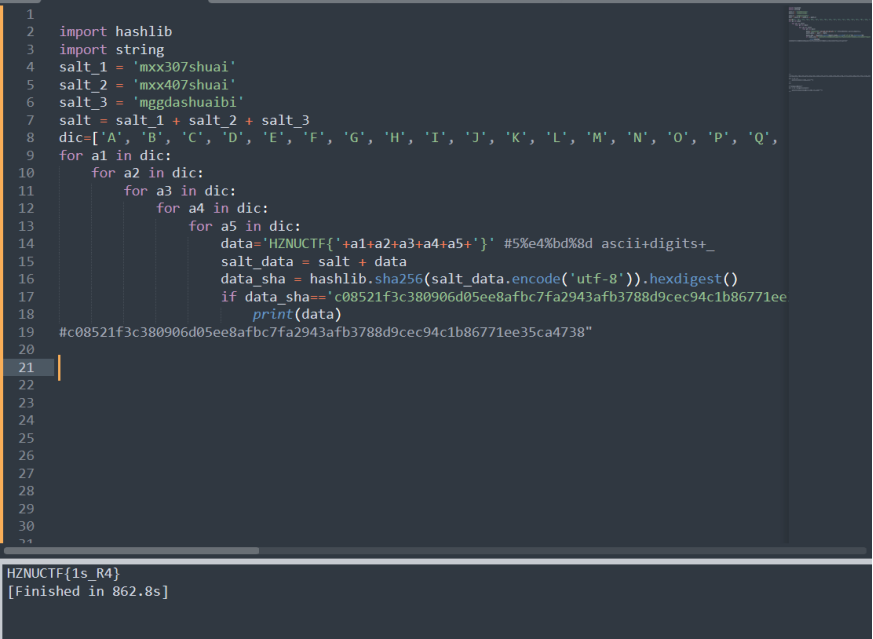
1 | import hashlib |
得到flag:HZNUCTF{1s_R4}
Pwn
easy_rw
Pwn佬说很简单,没什么好说的,就是迁移加个rw,直接贴脚本
1 | from pwncy import * |
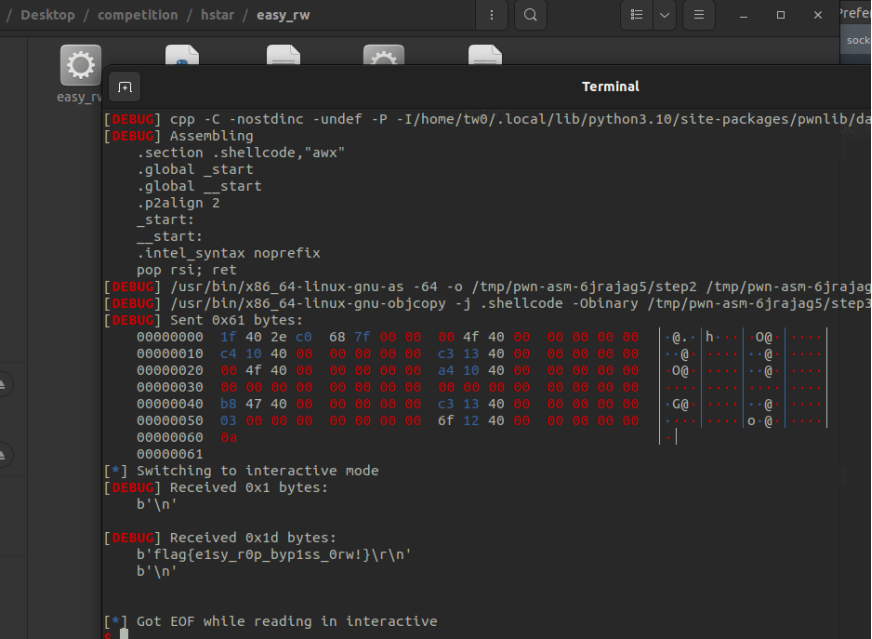
得到flag:flag{e1sy_r0p_byp1ss_0rw!}
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 Slagman!
评论
ValineDisqus




