2022NepCTF
Misc
签到题
是张图片,binwalk,得到压缩包,压缩包打开里面还有压缩包,压缩包名字还是递减的数字,显然是循环解压,找脚本跑
1 | import zipfile |
跑完了,用7z打开1.zip得到一个流量包,流量包一看就和国赛一模一样,直接上wp
tshark -r keyboard.pcap -T fields -e usb.capdata > usbdata.txt
每条数据都是十六个字节,用脚本加上冒号再对应一下
加冒号
1 | new = open('1.5.1.txt','w') |
一一对应脚本
1 | \#!/usr/bin/env python |
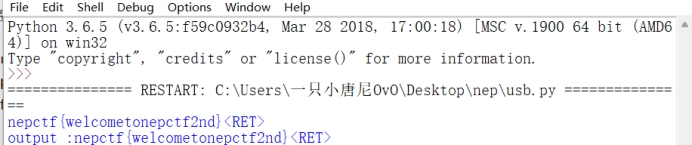
最后格式交半天交不对,大小写,首字母大写都试过了,没想到还有下划线在中间,还是得仔细阿
flag:nepctf{welcome_to_nepctf_2nd}
花花画画画花花
这道题就纯是找软件了,要解压掉,不然一开始的找osz后缀方向是错的,解压后发现osu后缀文件,整个osz用osu!音游软件编辑地图的功能打开,慢慢看就可以发现flag了,(一开始还以为要玩通,结果那难度根本玩不过,艹)
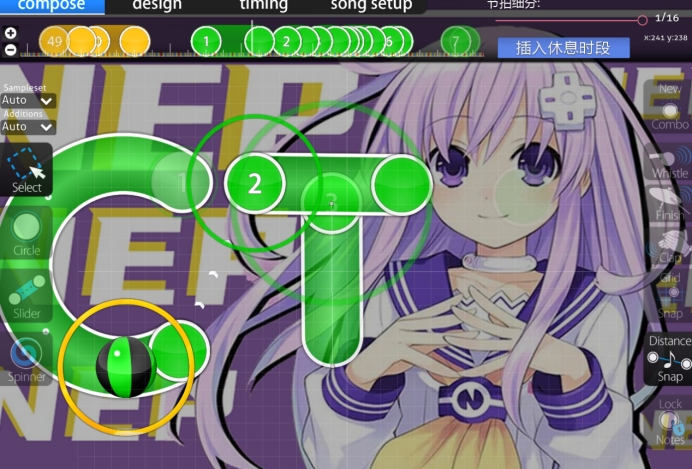
找到这个后面慢慢看就好了
flag:NepCTF{MASTER_OF_坏女人!}
9点直播
直播主页就有flag,不过昨晚直播间在打原是怎么回事,我超,原!
馅饼?陷阱!
一开始找东北饺子城,找不到,后来模糊搜索,搜大禾寿司上面的妆美业,结果真有
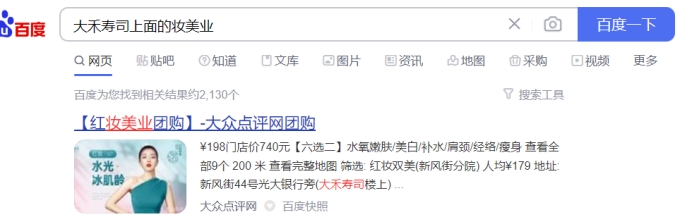
啥都出来了,就是光大银行
flag:NepCTF{www.cebbank.com}
少见的bbbbase
题目是一张jpg图片,用过steghide、binwalk、改宽高、stegsolve都没发现线索,直到找到了2020强网杯一道misc的一个步骤,其中stegdetect工具用了一下,发现也是jphide隐写
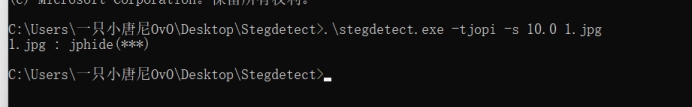
本来用stegbreak爆破
.\stegbreak.exe -r rules.ini -f password.txt -t p 1.jpg # password.txt为字典文件
但是爆了几十万的字典都没出,感觉有问题,可能密码要去别的地方找,结果是没有密码。。。。
直接jphs的seek空密码就出了
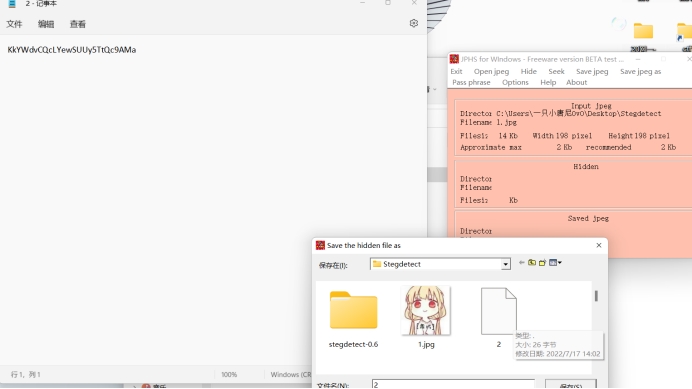
Basebreak爆一下就出了,是base58
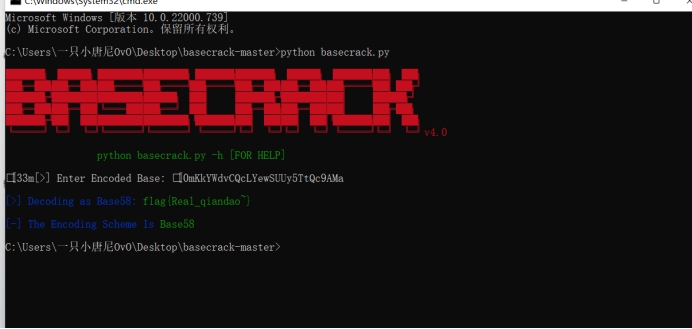
flag:flag{Real_qiandao~}
DCTris
这题属实是难搞,首先得知道cdi文件是一个DC游戏的光盘镜像,然后需要去找模拟器挂载,一开始都找的是主机模拟器,找过nullDC、Makaraon,但是要么不稳定要么就加载不了,最后找了安卓的一个模拟器reicast,还需要下载dreamcast的bios文件读取,后面就是苦练俄罗斯方块,真的太难了,玩了好久玩到4w多分才有后续
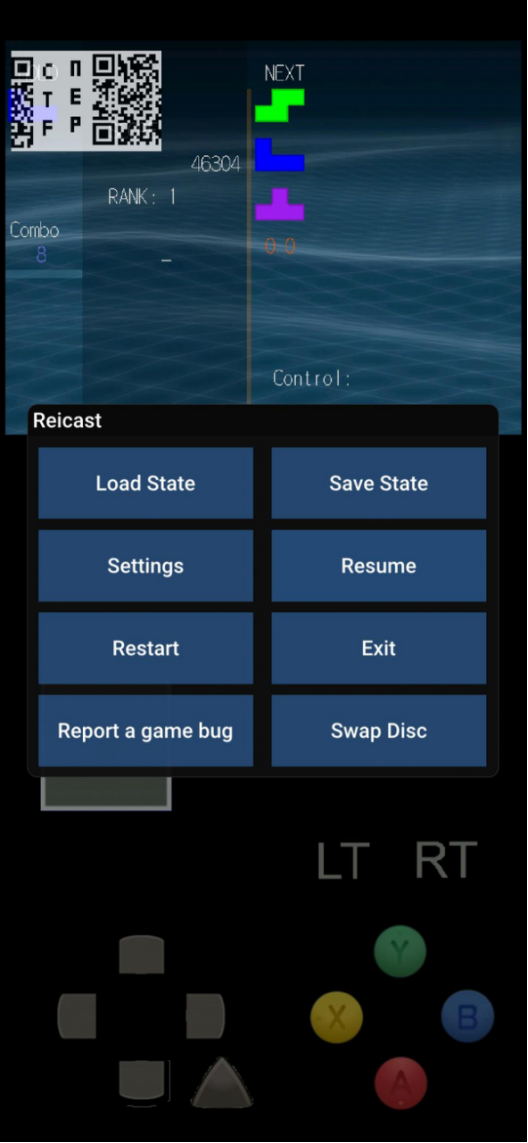
拼接一下

得到flag:NepCTF{LetsPlayFallingBlocksGameOnDreamCast!}
这题,感叹一下,太难了!!
Crypto
signin
题目给了n和e,先尝试分解n,factordb分解失败就用yafu分解
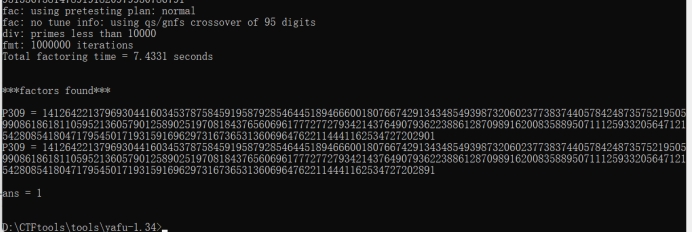
一开始还以为失败了,结果是两个素数太接近了
得到p和q之后,继续利用接下来的条件,已知p、q和c求余p和q的值,问了学数学系的同学知道了可以用中国剩余定理,于是找到脚本跑了一下得到c,再常规rsa解就出来了
中国剩余定理脚本如下:
1 | # 求两个数的最大公约数gcd函数 |
其中p、q位置需要换一下,得到c

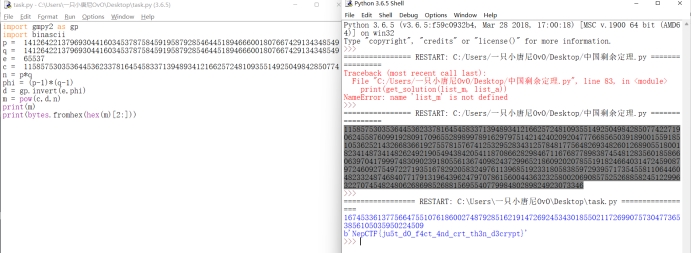
flag:NepCTF{ju5t_d0_f4ct_4nd_crt_th3n_d3crypt}
Reverse
快来签到
这题属实是没想到
用ida打开提示因为这个 main 函数太大,无法以流程图的方式显示出来,百度一下改下参数就行了
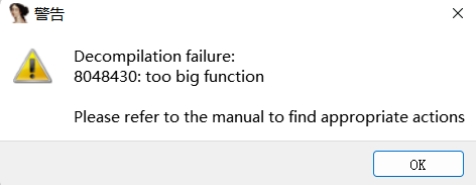
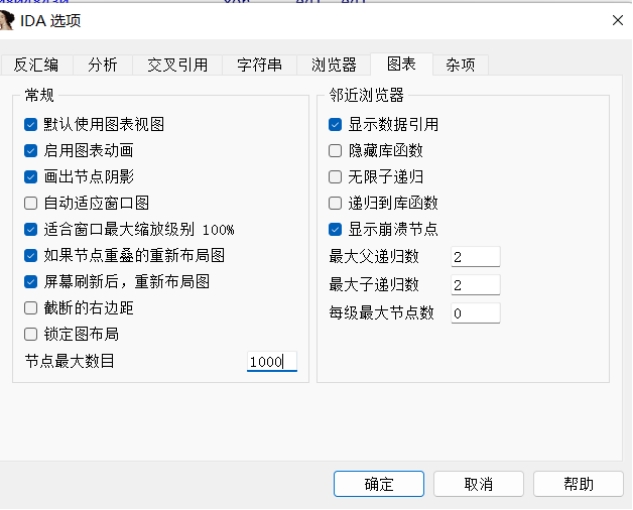
把这边节点最大数目改大一点就行了
flag:NepCTF{welc0me_t0_nepctf}




